
Automated Remediation in the Cloud: Empowering Efficiency with Cado
Automated remediation is the process of responding to security incidents without human intervention. It is a critical component of modern cybersecurity strategies, but it should be approached with caution. Under the right circumstances and in favorable situations, automated remediation actions can drastically reduce response time and minimize human error.
Below we outline why automation is the way to go, and how the Cado platform can help automate end-to-end incident response in the cloud.
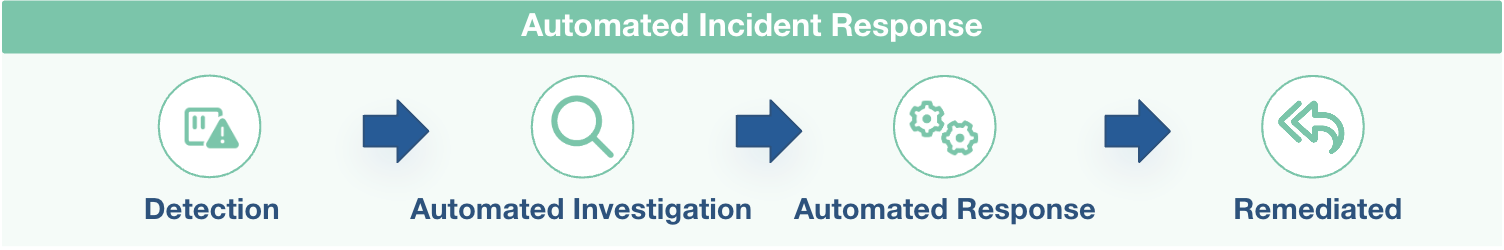
Automated Remediation: The Basics
An automated remediation process typically involves the following steps:
Threat Detection
Automated threat detection tools continuously monitor and analyze system metadata, network traffic, system logs, and other data sources to identify potential security incidents, anomalies, or vulnerabilities. These tools use various techniques such as signature-based detection, behavioral analysis, and machine learning to spot malicious activities.
Incident Investigation
Once a potential security issue is detected, it’s critical that security teams perform a deep-dive investigation to determine the nature and severity of the incident. This investigation should involve gathering additional data and context about the event, including forensic evidence, to ensure the incident’s true root cause and scope is determined.
Automated Response
Security teams can take advantage of automated response actions in the event they want to prevent the possibility of spread or damage while they perform a deeper dive investigation in the background. In this scenario, an analyst can automatically isolate or contain a system immediately following detection. In addition, another common automated remediation use case is to implement a remediation trigger based on alert severity. In this case, security teams can automatically execute additional response actions including blocking network traffic, quarantining infected systems, resetting user credentials, etc based on the specific nature of the threat.
The Benefits of Cado’s Automated Remediation Capabilities in the Cloud
There are specific benefits of implementing automated remediation that are unique to cloud environments.
Automated remediation enables security teams to:
Scale With the Cloud and Reduce MTTR
Cloud environments are constantly changing and can involve hundreds of virtual machines, containers and other services. The ephemeral nature of the cloud means that some services are constantly spun up, shut down and changed in a short duration of time. Because of this, it would be overwhelming and impractical to expect security teams to adequately investigate and respond to the sheer volume of alerts using manual techniques. Applying automation to the incident remediation workflow is the ideal solution to this problem, as it enables security teams to better manage risk identified in these environments and reduce overall MTTR (Mean Time to Response).
Operate 24/7, 365
Security threats can occur at any time. Continuous monitoring and automated response is critical in ensuring that threats are contained without delay. Threat actors are launching more and more attacks out of office hours and on holidays in a bid to catch security teams off-guard. With automated remediation, security teams can feel more confident that potential damage and spread can be prevented 24/7, 365 without human intervention. This approach considerably shrinks the attacker's window of opportunity.
Focus on What's Important
While the benefits of automated remediation are considerable, it is important to note that it should not be used to entirely replace human incident responders. Human oversight is an important part of the process and it is essential to validate automated response actions, investigate more complex incidents, and continuously adapt automated security policies as threats evolve. Automation should be used for mundane and repetitive tasks allowing security teams to focus on more important things – such as risk mitigation. A well-balanced approach combines both automation and skilled human analysts to effectively secure an organization's cloud environment.
How Cado Enables Security Teams to Automate Remediation Actions
Automation is a core pillar of the Cado platform. When it comes to automating remediation actions in cloud environments, the platform delivers two key features:
Automated Investigations
Cado’s Automated Investigation feature replicates investigative tasks a human analyst would take, such as running queries to identify the root cause of an incident. While it would be impossible to completely replace human analysts here, this feature was designed to free up analyst’s time so they can focus on the most important incidents and reduce hours spent on repetitive work.
The Automated Investigation feature provides a summary of what Cado has determined about a particular incident. This includes any malicious activity, the origin of the incident (root cause), a list of all compromised assets, and a full timeline of events to allow for easy pivoting.
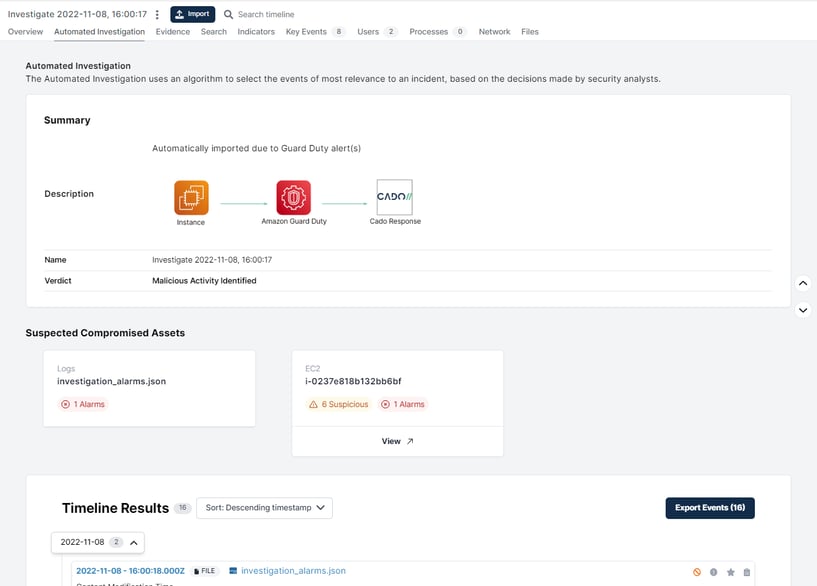
Automated Investigations in the Cado Platform
Cado's OpenAI Integration
Additionally, the Cado platform delivers an interactive Q&A interface powered by OpenAI’s GPT-3. This integration allows users to ask interactive questions of captured evidence and receive a rapid response. This feature further enhances and expedites the incident analysis process. For more information, see our in depth blog here.
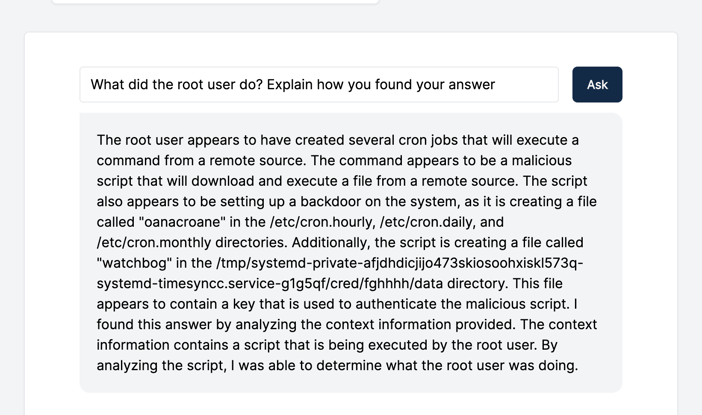
Cado + GPT-3: Interactive Incident Response
Automation Rules
The ability to automate remediation actions within the Cado platform is powered by automation rules.
These rules allow users to define:
- Environments where you wish to execute automated action(s)
- What data you want to collect (for example, following an alert you may want to automatically perform a triage capture or acquire full disk)
- What response actions you want to take
As an example, it is possible to create an automation rule that activates within a specific environment that contains sensitive data. As demonstrated in the image below, we have configured the rule to trigger immediately following a GuardDuty alert. The response entails the automatic collection of triage data, which will aid in the subsequent investigation. Additionally, the rule triggers the solution to automatically stop the instance to mitigate any potential spread or damage while we conduct our investigation.
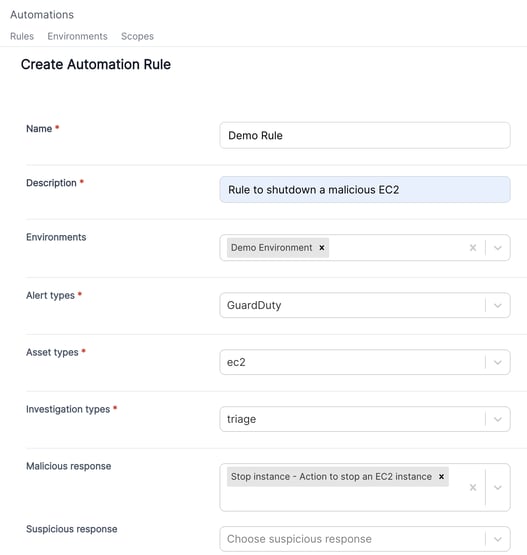
For a detailed tutorial on creating automation rules in the Cado platform, see our documentation here.
See for Yourself
If you want to see how Cado can bring automated remediation to your cloud environment. Contact us to schedule a demo or check out our 14-day free trial.
More from the blog
View All PostsAutomated Incident Response Definition, Best Practices and Tools
November 30, 2022Improving MTTR (Mean Time To Respond) Through Automation
December 13, 2022The Case for SOC Augmentation: Empowering Analysts, Not Replacing Them
January 7, 2025

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.
