The cloud is complex. Data can be extremely difficult to access, or worse, disappear in the blink of an eye. With more organizations shifting to the cloud, it is essential that security teams to have the ability to efficiently investigate and respond to a potential compromise.
This blog covers some best practices and useful resources when responding to security incidents in AWS EC2.
In the event you’ve identified a potentially compromised AWS EC2 instance, there are a number of immediate actions you can take:
- Change the security group to one that doesn’t allow any outbound internet access to limit the possibility of data theft.
- Identify if there was an Instance Profile attached to the EC2. If there was, check CloudTrail logs to see if it may have been abused to access other resources in AWS.
- Take a snapshot of the EC2 to enable forensic analysis later on.
Community Resources
- SANS published a whitepaper titled “Digital Forensic Analysis of Amazon Linux EC2 Instances”.
- A number of useful tools were released at Blackhat 2016 for AWS.
- Whilst a little dated now, there are also a number of helpful tools in the ThreatResponse Github repository for preserving forensic artifacts from EC2 instances, as well as isolating them and associated IAM credentials.
Official AWS Resources
AWS provides a number of experimental solutions to help isolate, preserve and analyze compromised EC2 systems. A few key ones to play with include:
- Solution for AWS Cloud for Incident Response in EC2 instances: This is a CloudFormation deployment to quarantine EC2 systems via SSM commands on the host themselves, perform security group changes, and snapshot EBS volumes.
- Automated Incident Response with SSM: Another solution that uses SSM that can also quarantine EC2 systems, but is based on the outcome of GuardDuty events.
- Automated Incident Response and Forensics Framework: A set of Security Hub actions to acquire data from EC2 systems.
- Automated Forensics Orchestrator for Amazon EC2: A more recent CloudFormation deployment to acquire data from EC2 systems then points you to the free SANS SIFT Linux distribution for command line analysis at the raw disk level.
- EC2 Auto Clean Room Forensics: A CloudFormation deployment that will run the open-source fls tool to dump file timestamps from files found on a compromised EC2 system.
- On the more control plane level, AWS provides a tutorial on how to investigate a compromised EC2 system through CloudTrail and VPC flow logs.
Cado Security Resources
At Cado, we’ve published a video tutorial on how to investigate a compromised EC2 Instance. You can leverage the Cado Investigation and Response Automation Platform to expedite incident response of potentially compromised EC2 systems. Cado seamlessly integrates with existing security solutions so that organizations can seamlessly drive an automated response framework to ensure critical evidence is captured, processed and preserved immediately following incident detection.
For more, see our playbook: Ultimate Guide to Incident Response in AWS.
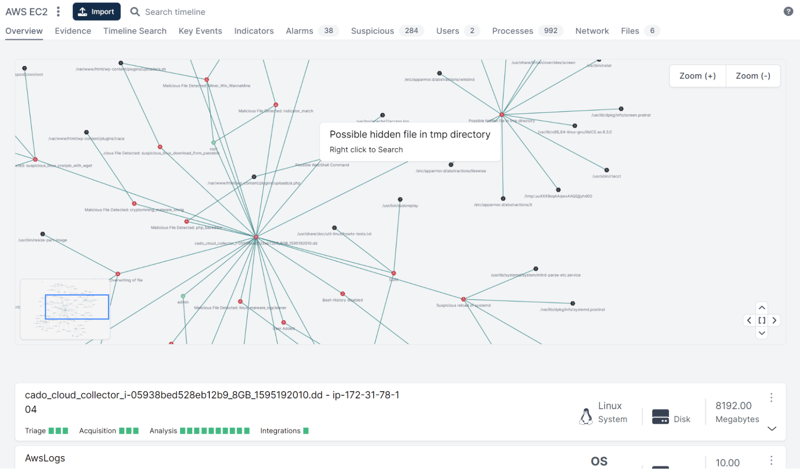
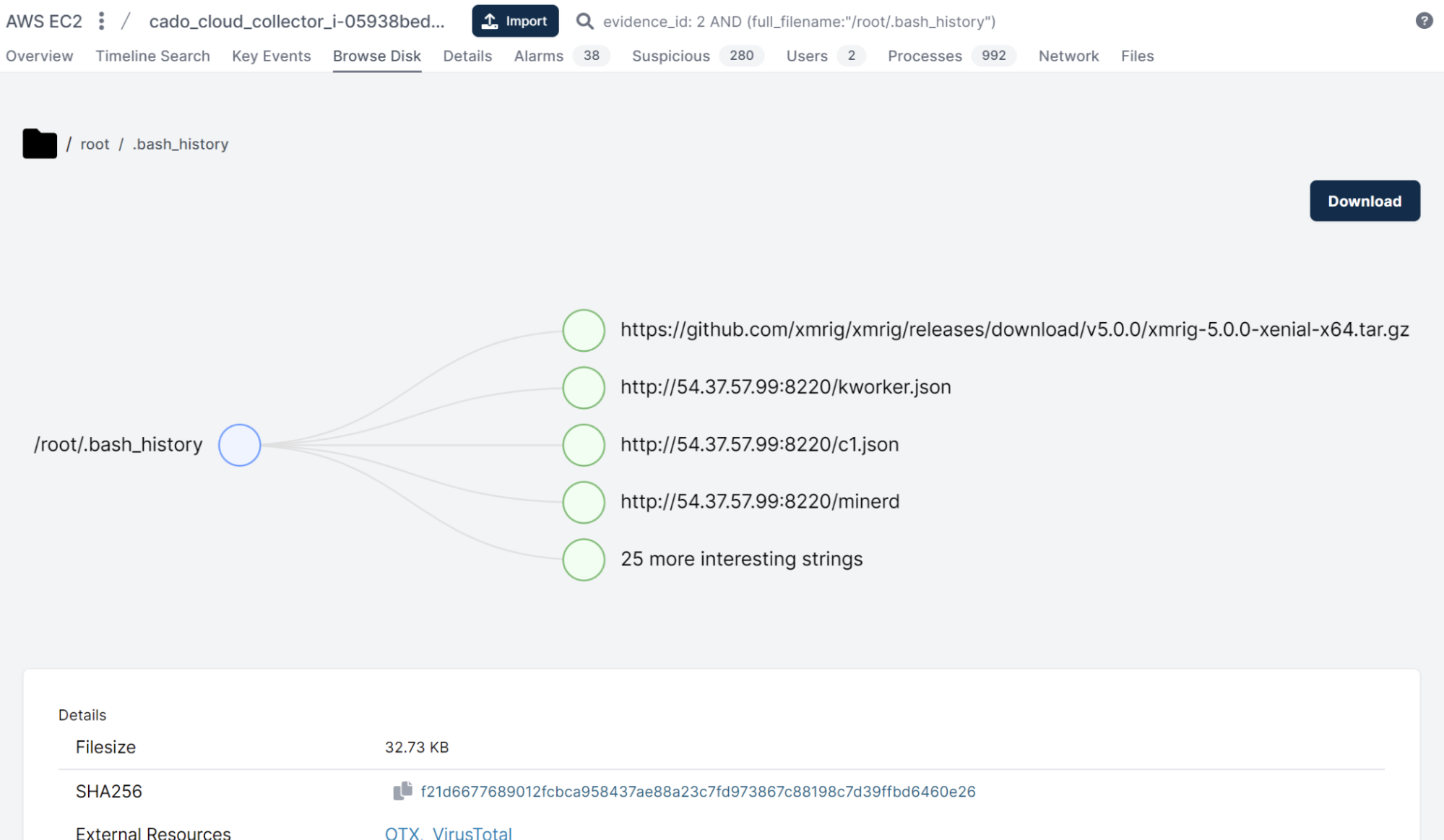
Interested in performing your own investigation using the Cado platform? Check out the 14-day free trial.
More from the blog
View All PostsA New Perspective on Resource-Level Cloud Forensics
October 30, 2023Leveraging Adversary Emulation for Effective Cloud Forensic Analysis
December 20, 2024Analyzing AWS Nitro Instances with Cado
August 23, 2023

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

