
Automating Investigations to Turn your Response Pipeline into a Feedback Loop
One of the core concepts in DevOps (and DevSecOps) is the creation and amplification of feedback loops. By creating, shortening and amplifying feedback loops we are able to improve the security of our services through continuous learning and improvement.
Much of the effort to date has been focused on creation of loops early in the SDLC:
- Static analysis and dependency scanning to catch vulnerabilities before they are even committed
- Container and image scanning to prevent deployment of components with known vulnerabilities
- Cloud configuration scanners to detect common misconfigurations of networks or security groups
Despite all of this, things invariably slip through the net! As the last line of defense, most organizations have extensive detection tooling so they can quickly identify when one of their VMs or containers is compromised and take appropriate action.
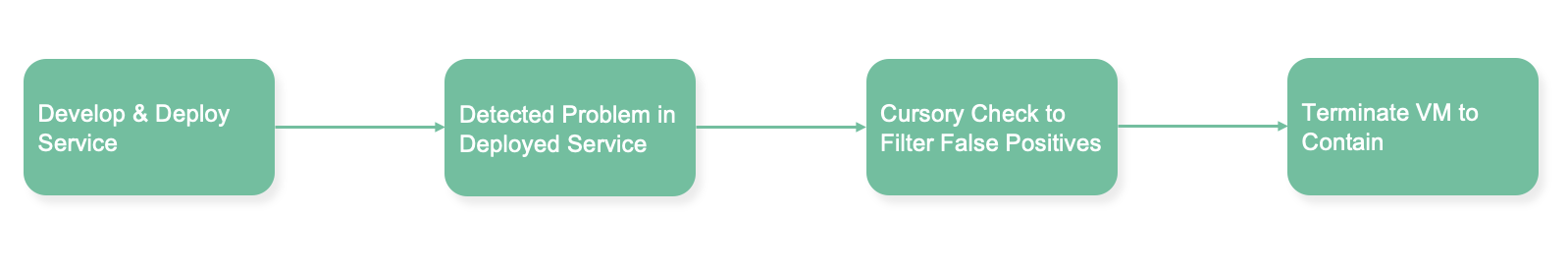
In many cases, this is surprisingly effective. Problems are quickly contained with minimal effort. But is this a great DevSecOps process? Where is our feedback loop?
With a response pipeline like this, it’s very common that after the compromised VM is terminated and redeployed from a fresh image it is immediately compromised again. Worms which automatically detect and spread to other vulnerable machines have been around for many years, and more recently research shows 80% of Ransomware victims that pay out are attacked again.
How can we add a feedback loop to our process which will allow us to learn from these mistakes and cut the problem off at the source?
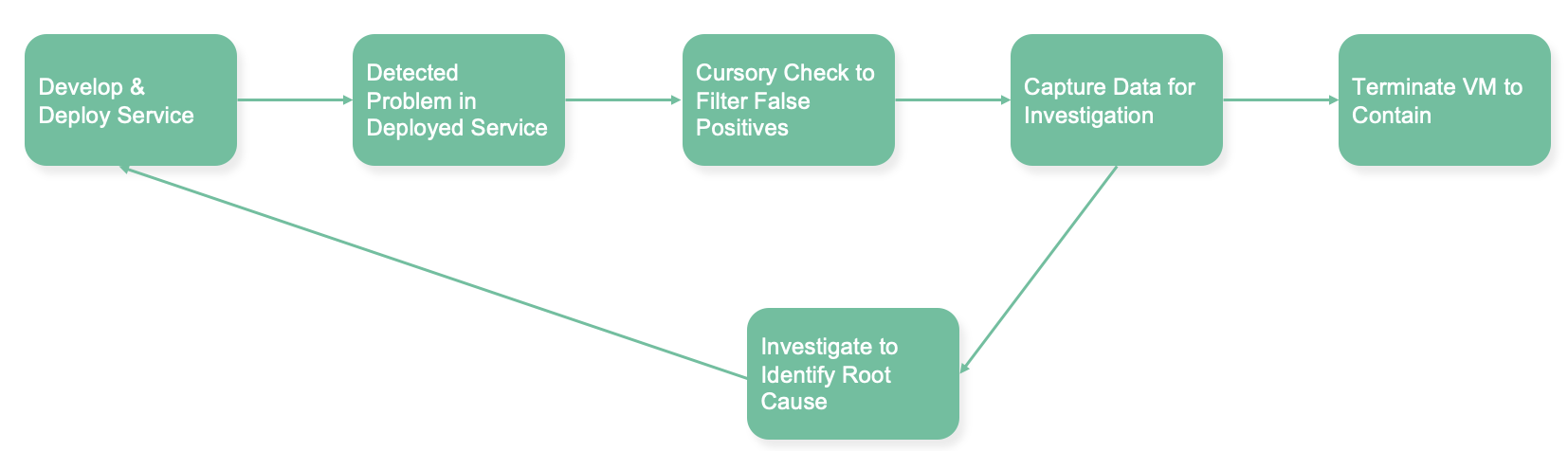
Unfortunately capturing the required data and identifying the root cause is easier said than done, especially in a complex cloud environment. The process requires many hours of manual effort from teams of expert cloud engineers and security analysts. This is where Cado Response comes in.
The Cado Response platform enables security teams to automatically capture the data needed for an in-depth cloud investigation with ease, and as soon as suspicious activity is detected. Further, the Cado Response platform was built to empower analysts of all levels. By presenting a single timeline of events, security teams can quickly understand the incident’s root cause and scope to facilitate proper containment, and ensure all existing gaps are closed to prevent future compromise. Ready to turn your response pipeline into a feedback loop? Get started with the Cado Response free trial today.
More from the blog
View All PostsOptimizing SOC Performance with Cado: Key Metrics for Faster Response and Resolution
December 17, 2024From SIEM to Ticketing: Streamlining Security Operations with Cado's Export Capabilities
January 23, 2025Why SOC Augmentation Should Be the Goal, Not SOC Automation
December 16, 2024

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.
