
How Cado Helps Security Teams Perform Investigations Relating to Business Email Compromise (BEC) Attacks in M365
Business email compromise (BEC) is a type of cyber attack that falls under the broader umbrella of phishing. In a BEC compromise, an attacker crafts a convincing-looking email to trick someone (usually a senior member of staff or budget holder) into sending money or divulging confidential company information. The attacker imitates a trusted employee and then requests the victim to transfer them money or send sensitive data.
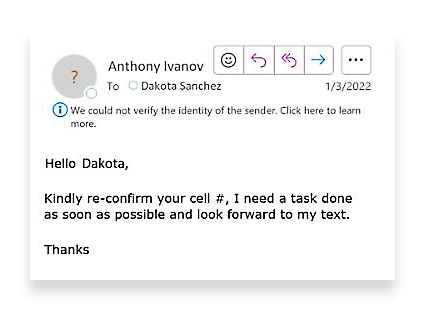
An example of a BEC fraud email, where an attacker impersonates a company executive
BEC is one of the most common and costly threats to organizations, with the FBI stating that from 2013 to 2022, BEC attacks cost organizations an incredible $50 billion globally. The increase in remote work has seen a significant rise in the prevalence of BEC, due to organizations heavily relying on email for transfer-of-funds requests. Attackers will utilize techniques such as email spoofing, phishing attacks, and using malware to take over legitimate email accounts or impersonate legitimate employees to carry out these attacks.
Because BEC attacks are so common, organizations require the ability to be able to quickly identify, investigate, and respond to such threats, to deal with the immediate attack, but also to strengthen their security posture and prevent further incidents.
M365 Unified Audit Log
Microsoft 365's Unified Audit Log (UAL) is a critical data source when investigating and responding to BEC incidents because it is a centralized source for all Office 365 events. The UAL contains over 70 categories of data, including events from Azure, Exchange, Sharepoint, and OneDrive. Cado recently launched its Microsoft 365 Incident Response cheat sheet to provide a quick reference guide to these logs. Microsoft currently offers a few different methods for viewing and exporting the UAL. For example, the UAL can be accessed through the Security & Compliance Center, and the Office 365 Management API. However, it’s important to note that there are limitations when acquiring the UAL, including how many records can be exported which is capped at 5,000 sorted records or 50,000 unsorted records. Unfortunately, this is often insufficient for many forensic investigations – as more data is needed to conduct a thorough investigation. Additionally, to enable log collection from the UAL, certain permissions are required, which are often overlooked until an analyst is actively attempting to collect the logs.
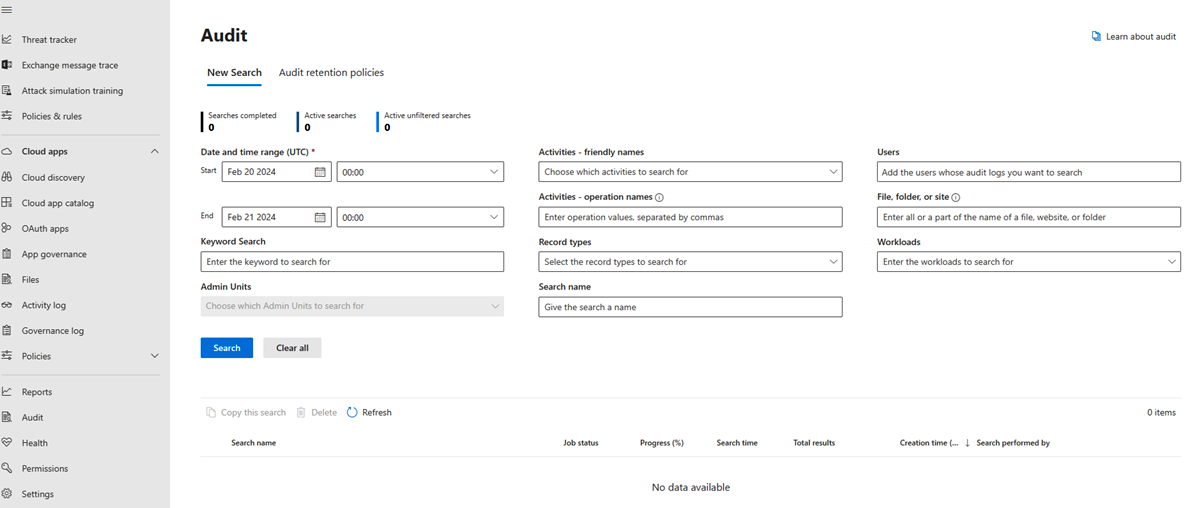
Searching the Audit log within Microsoft Defender XDR
Mailbox Audit Logs
Another important source of logs when investigating BEC is the Mailbox Audit Logs. Mailbox Audit Logs can be used to determine when a mailbox was updated unexpectedly or whether items are missing from a mailbox. These logs are retained for 90 days. Mailbox Audit Logs can only be accessed via PowerShell and only by members of the Audit Reporting Mailbox self-service group. Microsoft provides a guide to accessing and searching the Mailbox Audit Log, including a sample script for retrieving the logs.
How Cado Can Help
The Cado team has recently introduced the ability to collect and analyze data acquired from SaaS environments within the Cado Platform. With the ability to automatically import and analyze Microsoft 365 Unified Audit Logs (UAL) and analyze these logs alongside other forensic artifacts collected from an affected user’s workstation in a central platform, security teams are able to accelerate the path to root cause and remediation.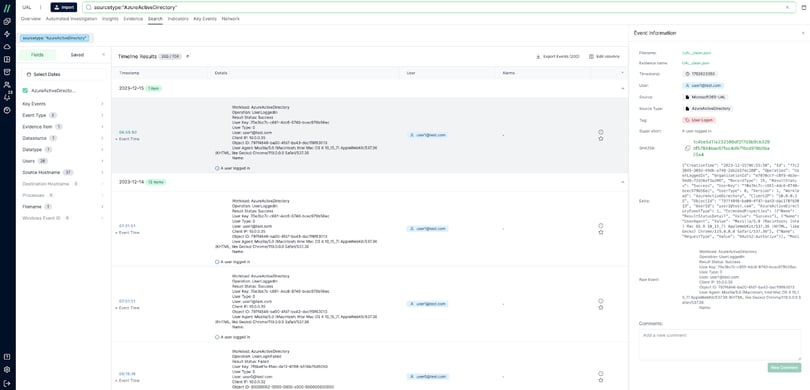
M365 UAL In the Cado Platform
The Cado platform eliminates many of the limitations previously mentioned with accessing the UAL. The Cado platform can be configured to automatically import the UAL, allowing investigations to kick off as soon as malicious activity is detected, eliminating the permission and export challenges. The imported logs are then immediately available to analysts in the Cado platform for investigation. Other artifacts captured across on-prem and cloud assets can also be imported into the same project, so that analysts can seamlessly investigate everything in a single platform, single timeline.
The Cado platform doesn't just extract the UAL, it provides a comprehensive solution that enables security teams to seamlessly search and analyze the contents of the UAL. The platform provides the ability to search by Time Frame, User, IP, or Workload (Microsoft 365 service, e.g. Exchange, Onedrive, Sharepoint, etc.) empowering security teams to quickly gain a deeper understanding of root cause, scope, and impact of any malicious activity.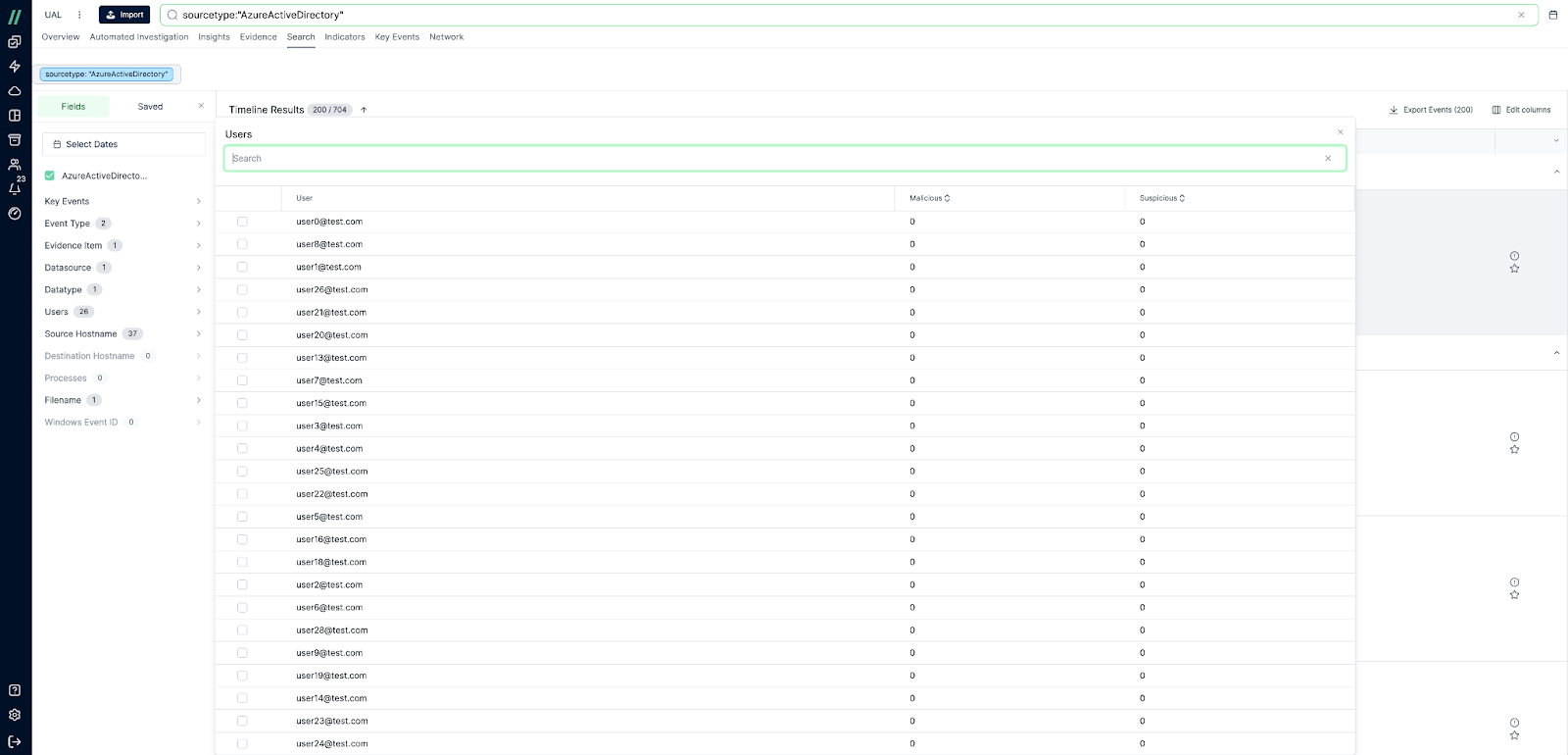
Searching the UAL in the Cado Platform
The Cado platform also delivers several other features that can significantly reduce the amount of time and effort required to investigate and remediate incidents, not just in SaaS environments but across the cloud:
- Single-Click data capture: Cado enables automated and single-click evidence collection across cloud and SaaS environments.
- Parallel Processing: The Cado platform’s patented cloud-native architecture enables hundreds of data formats to be normalized in just minutes.
- Automated Investigations:
-
-
- Cado AI Investigator, powered by Cado’s local LLM, delivers a high-level summary of an incident and analyzes potentially malicious files.
- Automated timeline & root cause analysis: The Cado platform automatically pulls together a full timeline of events to accelerate the path to root cause and remediation.
- Proprietary and third-party threat intelligence is leveraged to automatically flag malicious and suspicious activity so analysts can easily pivot their investigation based on key events.
- Single Pane of Glass:Organizations can gain a better understanding of the impact of threats with complete visibility across their entire ecosystem. Cado provides the ability to seamlessly analyze SaaS, cloud, container, serverless, and on-premises assets in a single platform, single pane of glass
-
By providing security analysts with the ability to quickly and seamlessly analyze UAL logs alongside other critical sources captured by the Cado platform across on-prem and cloud assets, organizations can be better prepared to handle compromises identified in Microsoft 365, including BEC. Cado also recently launched its latest cheat sheet for Microsoft 365 Incident Response, Interested in learning more? Schedule a demo with our team.
More from the blog
View All PostsCado Introduces Support of SaaS Environments to Expedite Investigation and Response to Microsoft 365 Compromises
March 14, 2024Top Cloud SaaS Threats and Tips for Investigation
March 7, 2024What's New in the Cado Platform Q1 2024 Recap
April 23, 2024

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.
