
Intelligence Driven Cloud Incident Response with Cado Response and SophosLabs Intelix
By Daniel Hunt and Chris Doman
In the cloud, security incidents happen fast. But defenders can move even faster. In Cloud environments, such as AWS and Azure, defenders have the ability to get enough data to go both deep and wide at the same time. And a faster investigation means a faster recovery and less impact to the business.
Today we’re incredibly excited to announce the Cado Response integration with SophosLabs Intelix to deliver the speed that security teams need to protect their cloud environment.
Cado Response automates the acquisition of cloud systems with zero impact. When combined with a malware analysis platform, like SophosLabs Intelix, security analysts can submit files for analysis and use malware findings as an investigation pivot point.
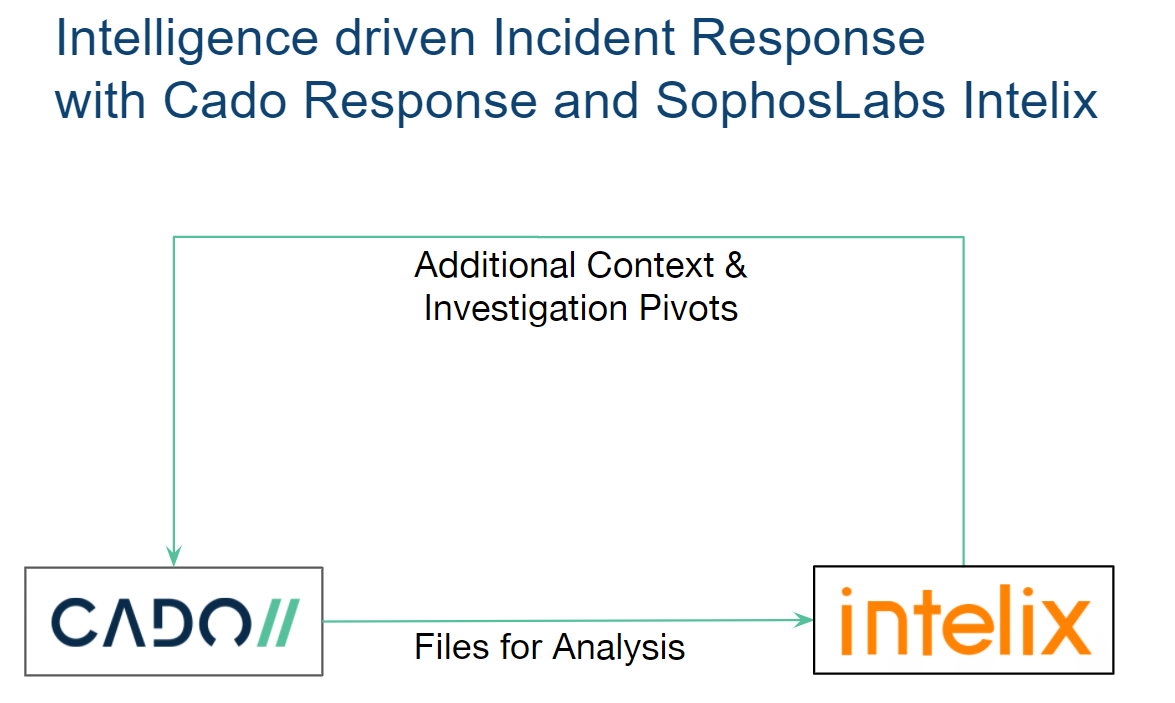
Let's dive into an example!
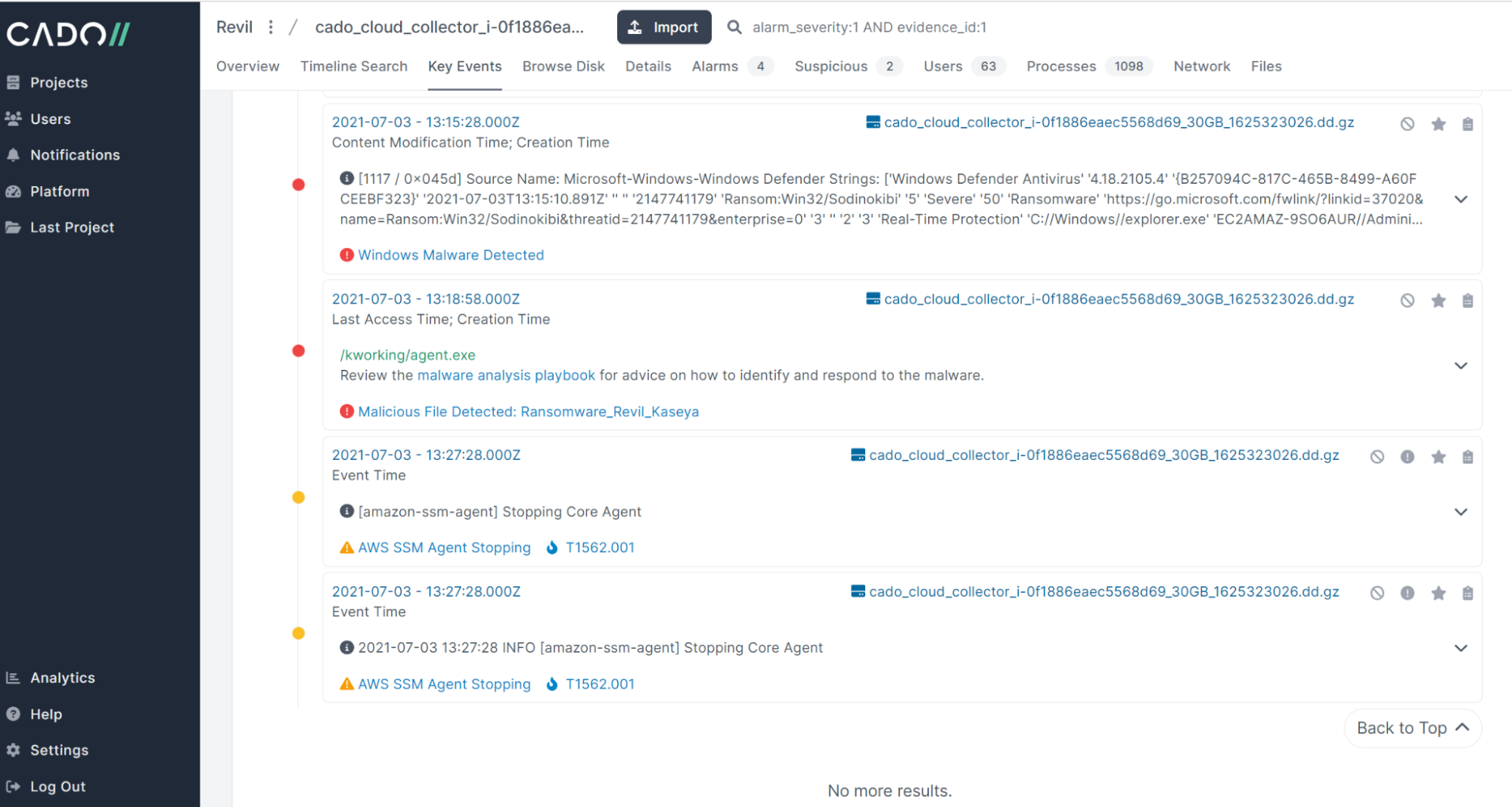
Below let's investigate an AWS EC2 Windows system we’ve intentionally infected with Revil Ransomware. If you’d like to perform your own investigation at home, we have details on how to enable the integration below and you can get a full copy of the disk imaging we’re analyzing here from our Github repository.
Immediately, we can see ransomware detections which give us a starting point for our investigation:
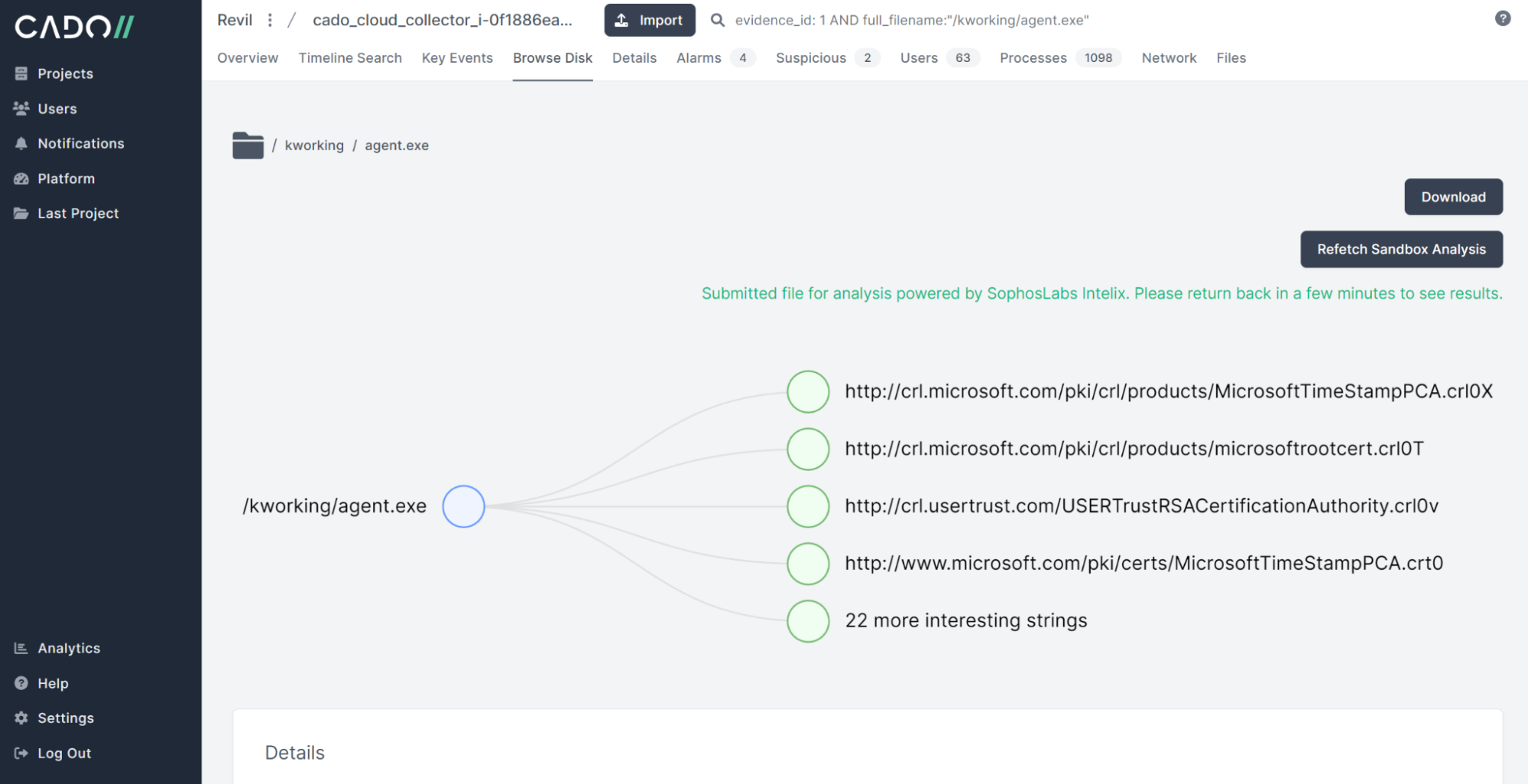
By opening the file /kworking/agent.exe, we can view the file contents as well as any VirusTotal detections and timestamps. But let's send the file to SophosLabs Intelix to get more information!
In just minutes, we can see a full analysis report natively within Cado Response:
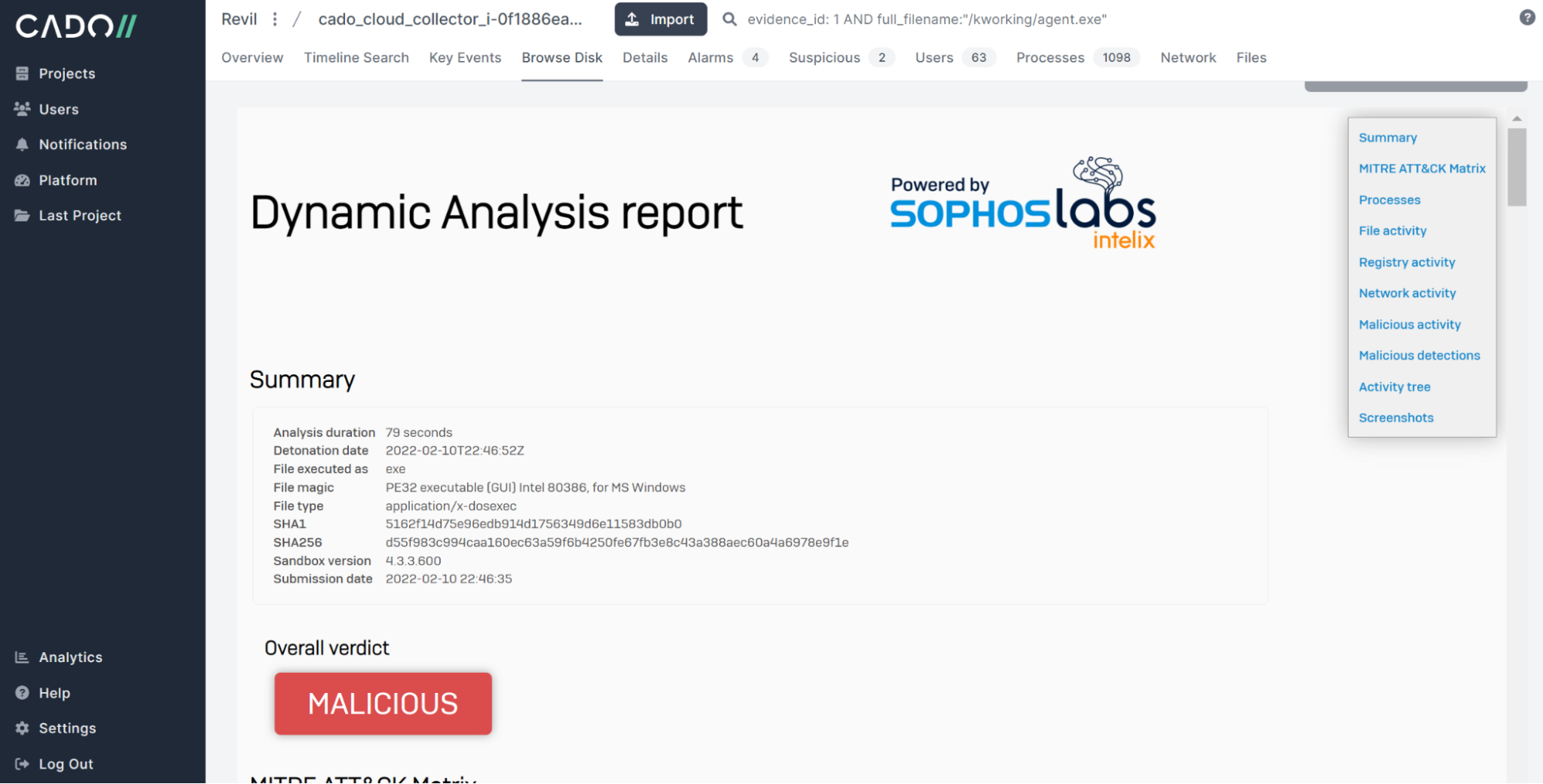
The report includes details such as the MITRE ATT&CK matrix of techniques the malware uses. We can look for these techniques on the disk we have acquired.
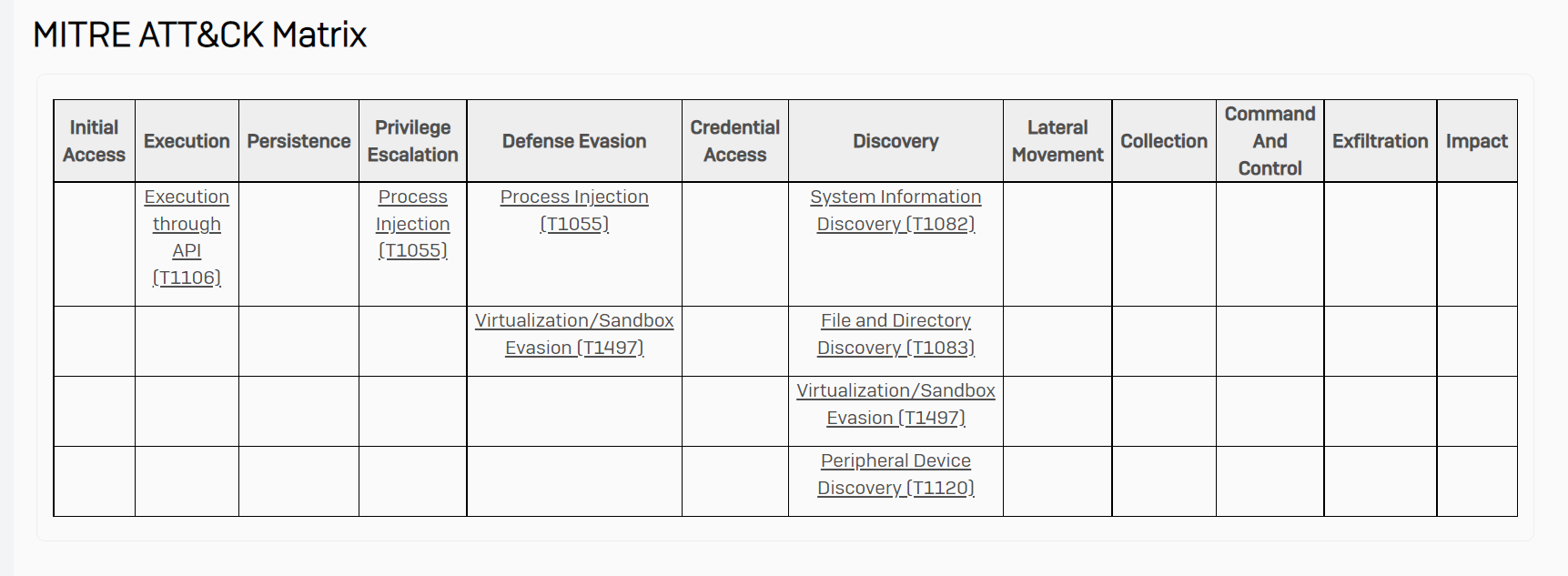
We also get a wealth of information from executed processes, file activity, registry activity and network activity. An easy place to start is by looking at the dropped files that SophosLabs Intellix has identified as malicious:
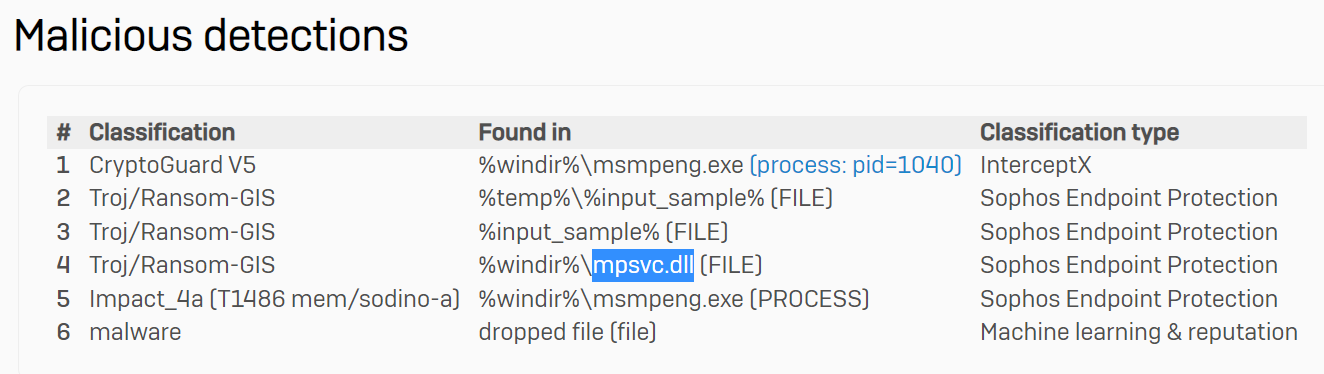
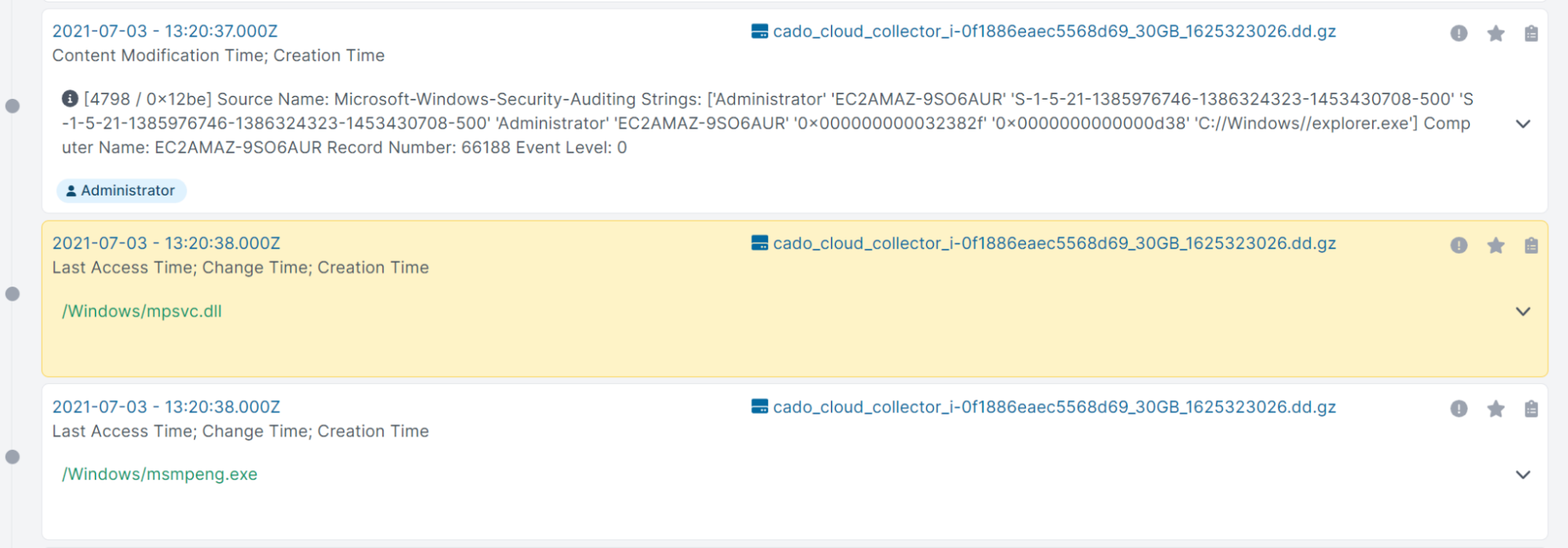
Let’s take a look at this file “mpsvc.dll” in Cado Response. Here, we can see some file contents:
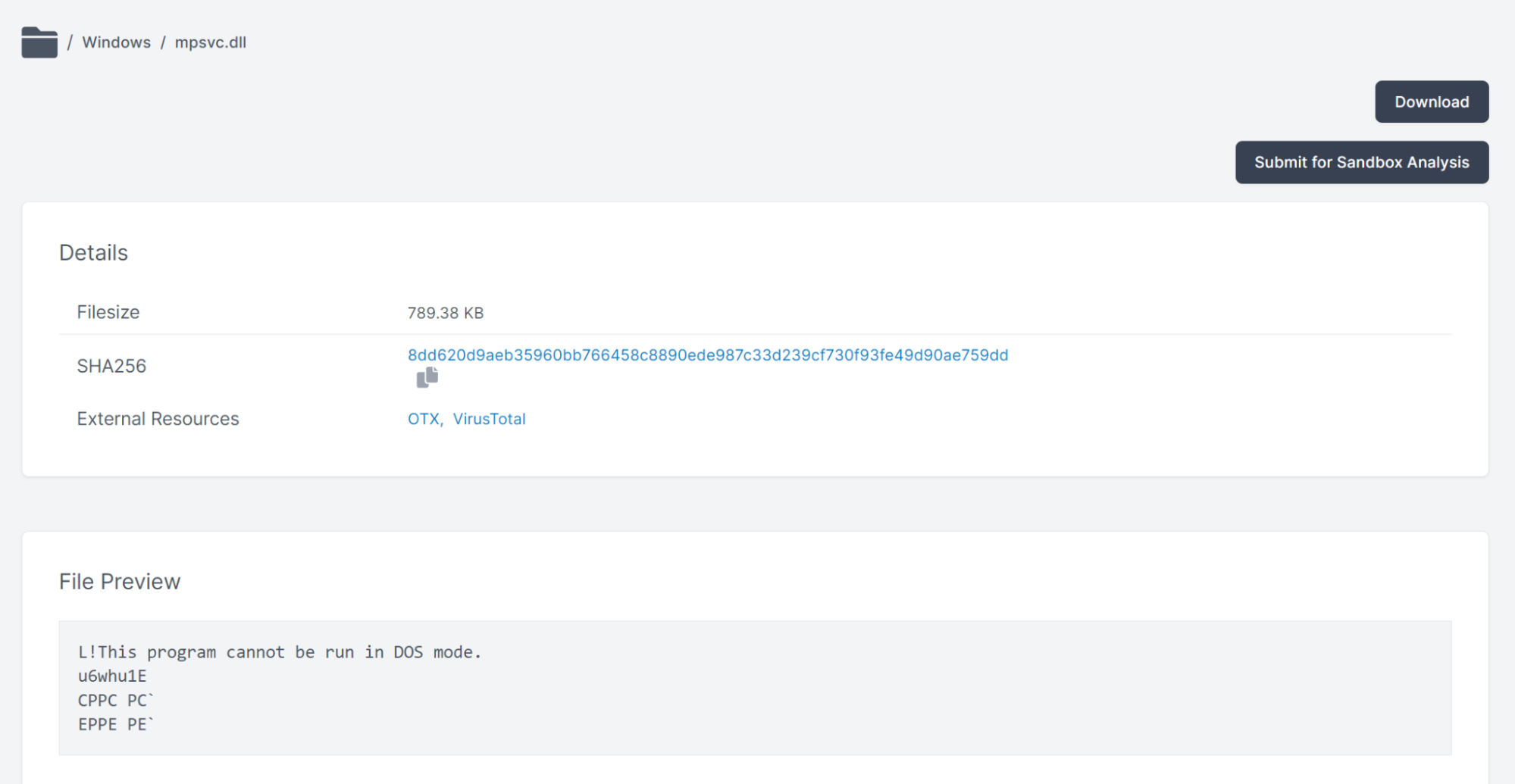
The file is named after the DLL library used by Windows Defender. After we submit the file to SophosLabs Intelix, however, we can confirm this file is indeed malicious and likely side-loaded to limit detection:
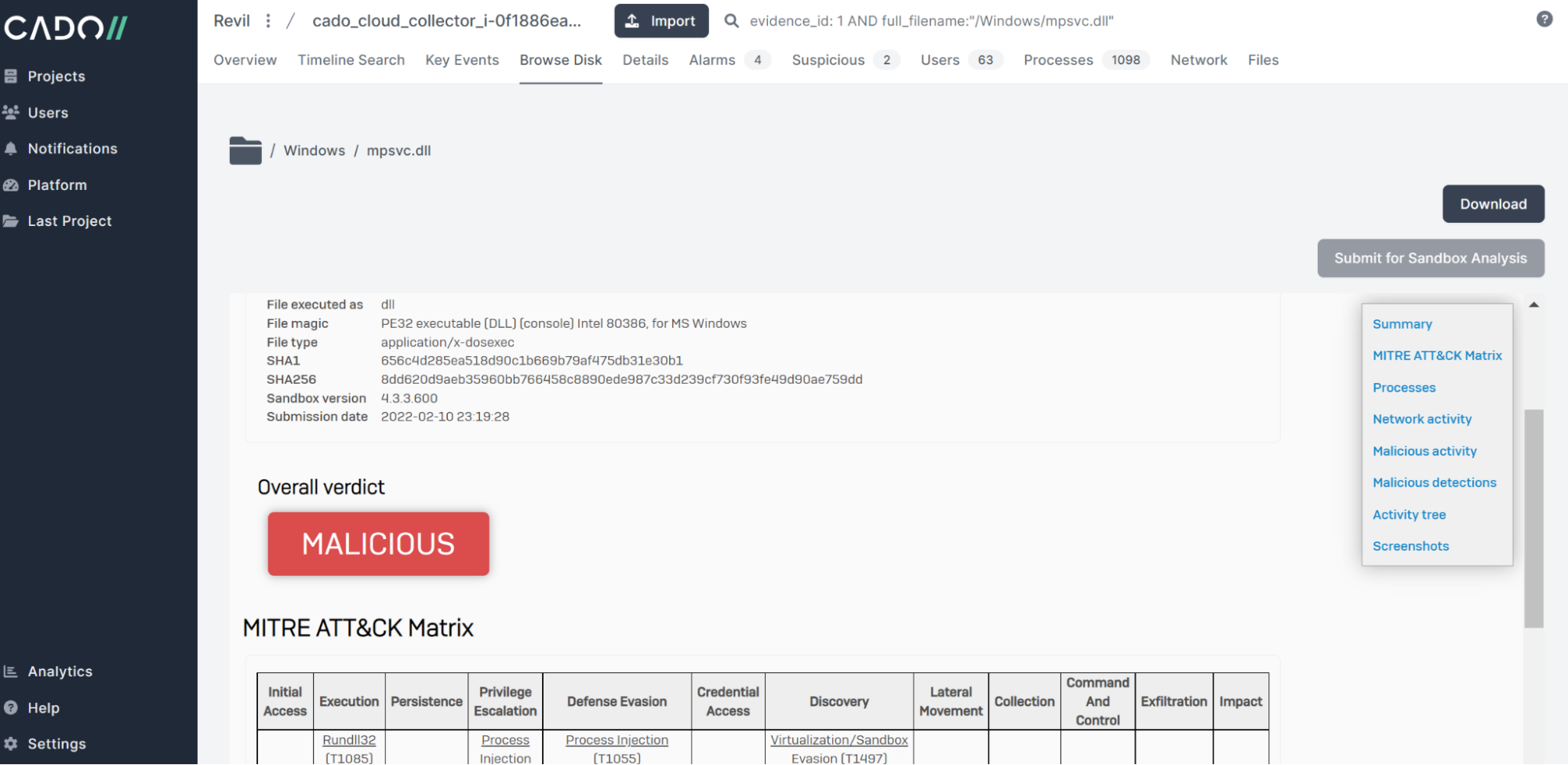
From here, we can continue our investigation. For example, by pivoting on the malicious file’s creation timestamp, we can find other related events on the system:
How to set this up in your environment
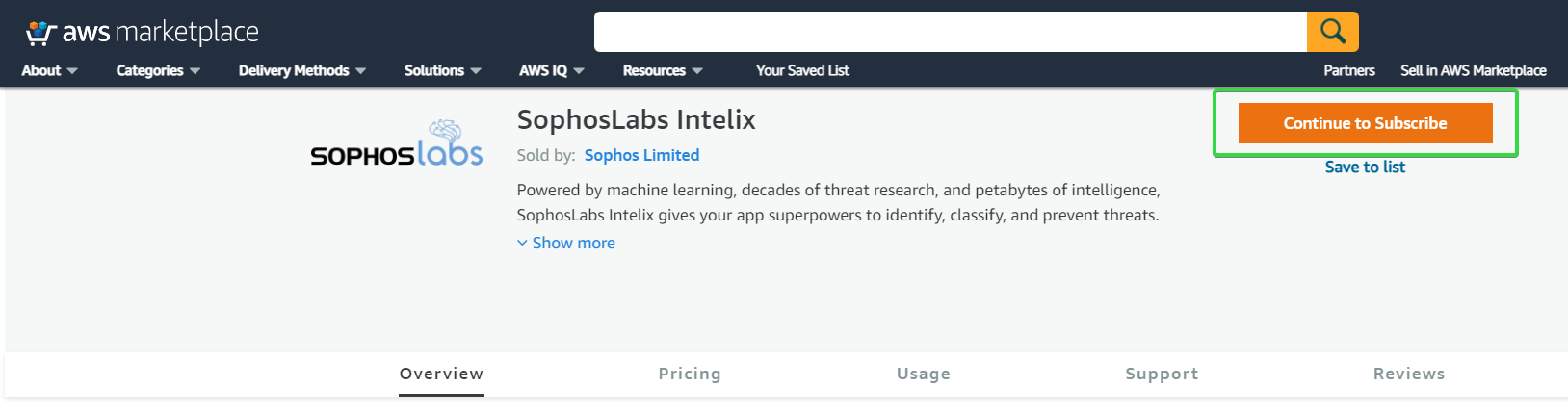
If you haven’t deployed Cado Response yet, you can deploy a free trial. And you can easily subscribe to SophosLabs Intelix through the AWS Marketplace to receive API credentials:
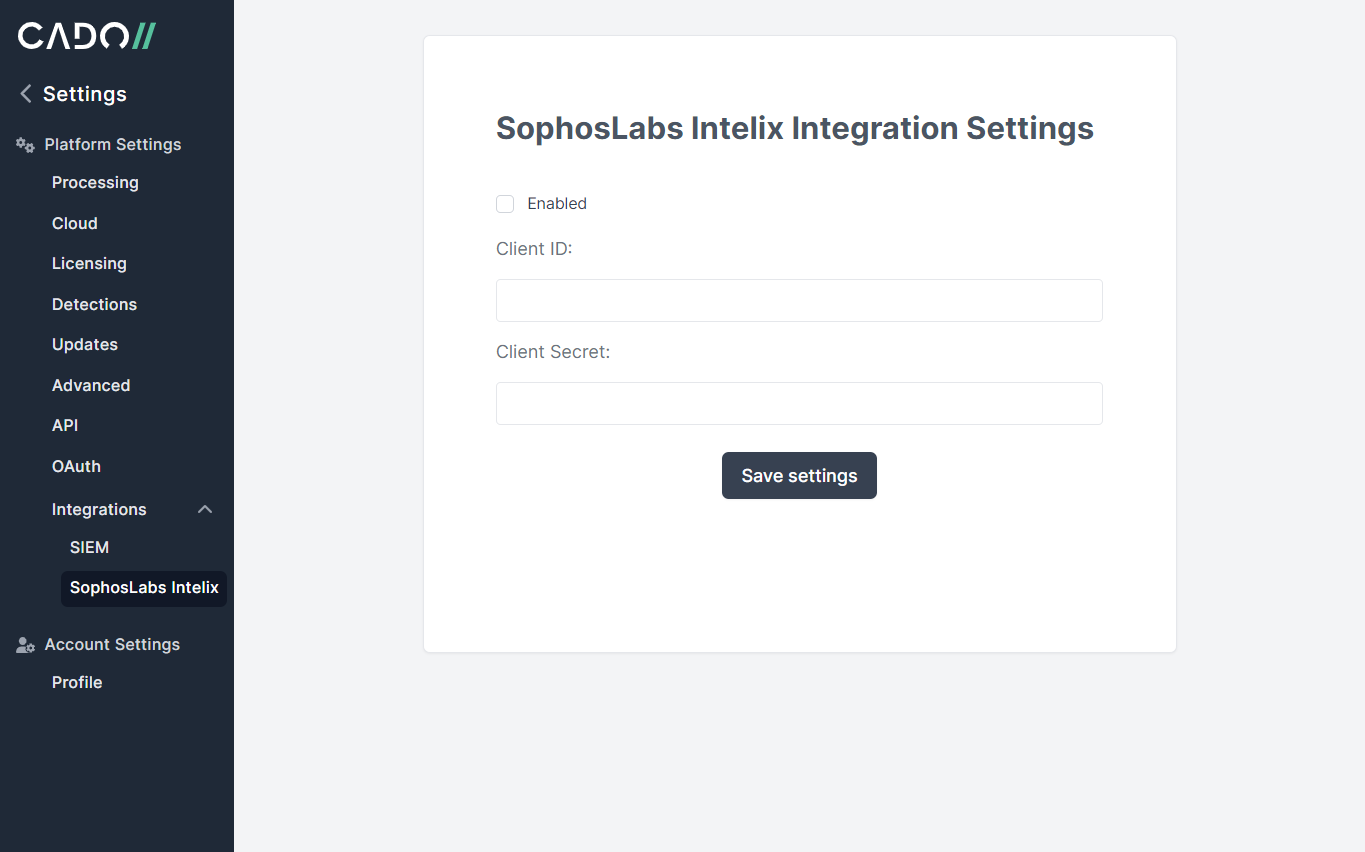
Then simply add the credentials to the Cado Response Platform in the SophosLabs Intelix Integration settings page:
Now you can benefit from additional intelligence and dynamic sandbox analysis capabilities powered by SophosLabs Intelix to further enhance your cloud investigations.
More from the blog
View All PostsCado Response Now Integrates with Splunk SOAR to Automate Your Cloud Incident Response Workflow
February 14, 2022Automate Incident Response with the new Tines and Cado Response Integration
October 28, 2021Accelerating Incident Response with Automation
March 14, 2025

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.
