With estimates that by 2025 85% of business applications will be SaaS-based, it is a sector that is growing rapidly, with Gartner stating it's the fastest growing cloud sector 2016. Threat actors have noticed this growth and with more and more businesses relying on SaaS applications, they are very appealing targets so it's no surprise that attacks against SaaS services are on the rise. This is on top of the fact that it can be hard to identify and swiftly mitigate threats against SaaS applications due to factors such as a lack of control and visibility in SaaS environments, Shadow IT, and the fact that organizations are often at the mercy of SaaS providers to perform effective vulnerability management.
Here are some of the top threats targeting SaaS environments:
Business Email Compromise
Business Email Compromise (BEC) is when attackers compromise or impersonate legitimate business email accounts or employees to conduct fraudulent activities. Typically, attackers impersonate high-level executives or trusted employees to convince individuals within the organization to transfer funds, disclose sensitive information, or execute unauthorized transactions. BEC attacks often involve social engineering techniques, exploiting trust and familiarity to manipulate their target.
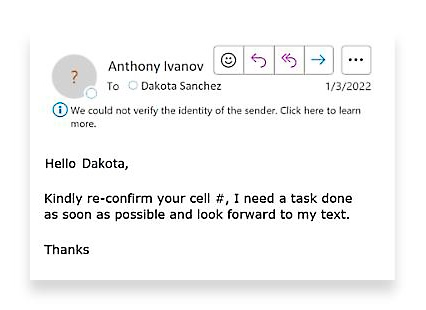
An example of a BEC email, where an attacker impersonates a company executive
The increase in remote working has also contributed to a spike in BEC attacks, as organizations rely more heavily on email for transfer funds requests. BEC attacks are one of the most common and costly attacks on organizations, with the result in substantial financial FBI stating that BEC attacks cost 2.7 billion globally in 2022. Vigilance, employee awareness, and robust authentication measures are crucial in mitigating the risks associated with BEC attacks.
Account takeover
An account takeover attack is when an attacker gains access to a user's account either by stealing credentials, exploiting vulnerabilities, credential surfing, or any number of other methods. Once the attacker has compromised the account, they may then misuse it for a wide variety of malicious activities, including fraudulent transactions, data theft, or spreading malware.
Insider threats
Insider threat attacks are attacks where individuals within an organization misuse their access privileges to compromise security. These threats can manifest in various forms, including data theft, sabotage, or unauthorized access to sensitive information. Unlike external threats, insiders possess intimate knowledge of the organization's systems and protocols, making their actions harder to detect. Insider threats can stem from disgruntled employees, negligent behavior, or unintentional mistakes.
Vulnerabilities
Vulnerabilities are flaws in the system that can be exploited by attackers, to either disrupt or gain access to a SaaS service. They can be incredibly hard to mitigate and often users are completely at the mercy of the SaaS provider to manage any vulnerabilities that are discovered in the system. when attackers employ these kinds of attacks they are often used as a stepping stone to one of the other attacks mentioned in this blog
Supply chain attacks
Supply chain attacks target the interconnected network of vendors, suppliers, and partners that support an organization's operations. Attackers exploit vulnerabilities within the supply chain to infiltrate trusted systems and compromise data integrity or disrupt business operations. These attacks can involve malicious code injected into software updates, compromised hardware components, or unauthorized access to sensitive information through third-party service providers. Mitigating supply chain attacks requires comprehensive risk assessment, vendor management protocols, and ongoing monitoring of supply chain security.
Tips for Investigating SaaS Environments
Investigating SaaS environments can be partially complicated. with analysts often needing more evidence sources to work with. Here are some tips for investigating incidents in SaaS environments.
Be Prepared
The worst time to discover you haven't been collecting Logs and other evidence is when you're in the middle of an incident and go looking. Only to find that it was never recorded or inaccessible. So before any incidents have a chance to occur ensure firstly, that your logs are enabled and secondly, that they can be accessed by relevant parties.
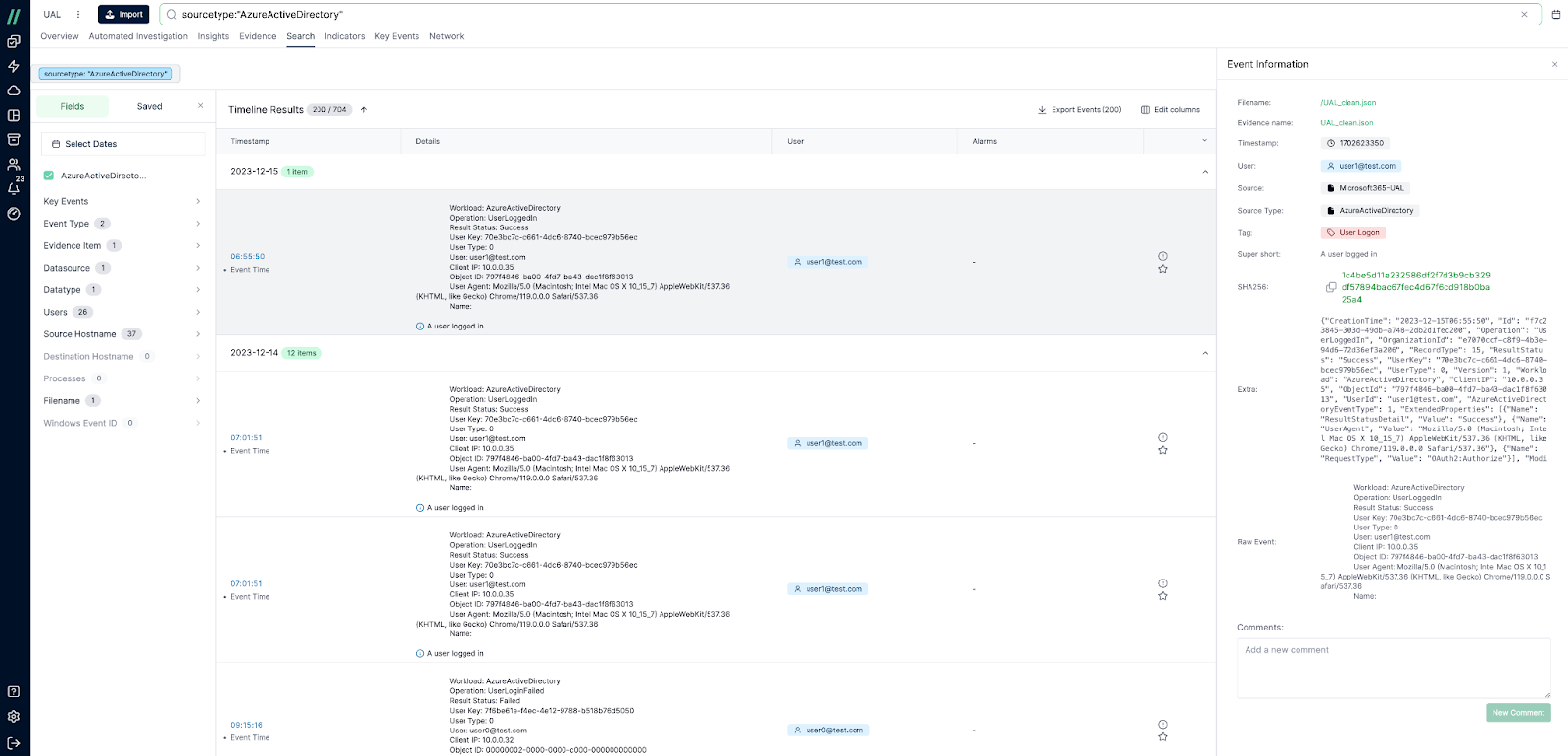
M365 UAL In the Cado Platform
Know the different types of logs
There is more than just one Log, with different events logged in different places the most common across SaaS platforms are the following:
System logs: system logs record activity performed by software, such as operating systems, or other applications. These can be used to answer questions such as when was a device spun up or what services have been running on a given container.
Application Logs: these are logs that record activity performed by external users when using an application. Answers to questions such as who logged in and when? And who used what applications? Can be found here.
Audit Logs: these record events, changes on system infrastructure, and questions such as who created a resource? Or who reconfigured a permission? Can be answered with these logs.
The Cado Platform Now supports SaaS environments
The Cado Platform recently launched the ability to import Unified Audit Logs (UAL) from Microsoft 365 into the platform. Empowering analysts to leverage the power of the cloud when investigating incidents inside M365 SaaS environments.
The platform can acquire the UAL and provide analysts with quick access without the need to navigate the maze of assigning complex roles to individual analysts or use the complicated PowerShell Commands normally needed to retrieve the UAL. And once the UAL is in the Cado platform, The UAL can be analyzed directly alongside other forensics artifacts such as those from an affected user's workstation.
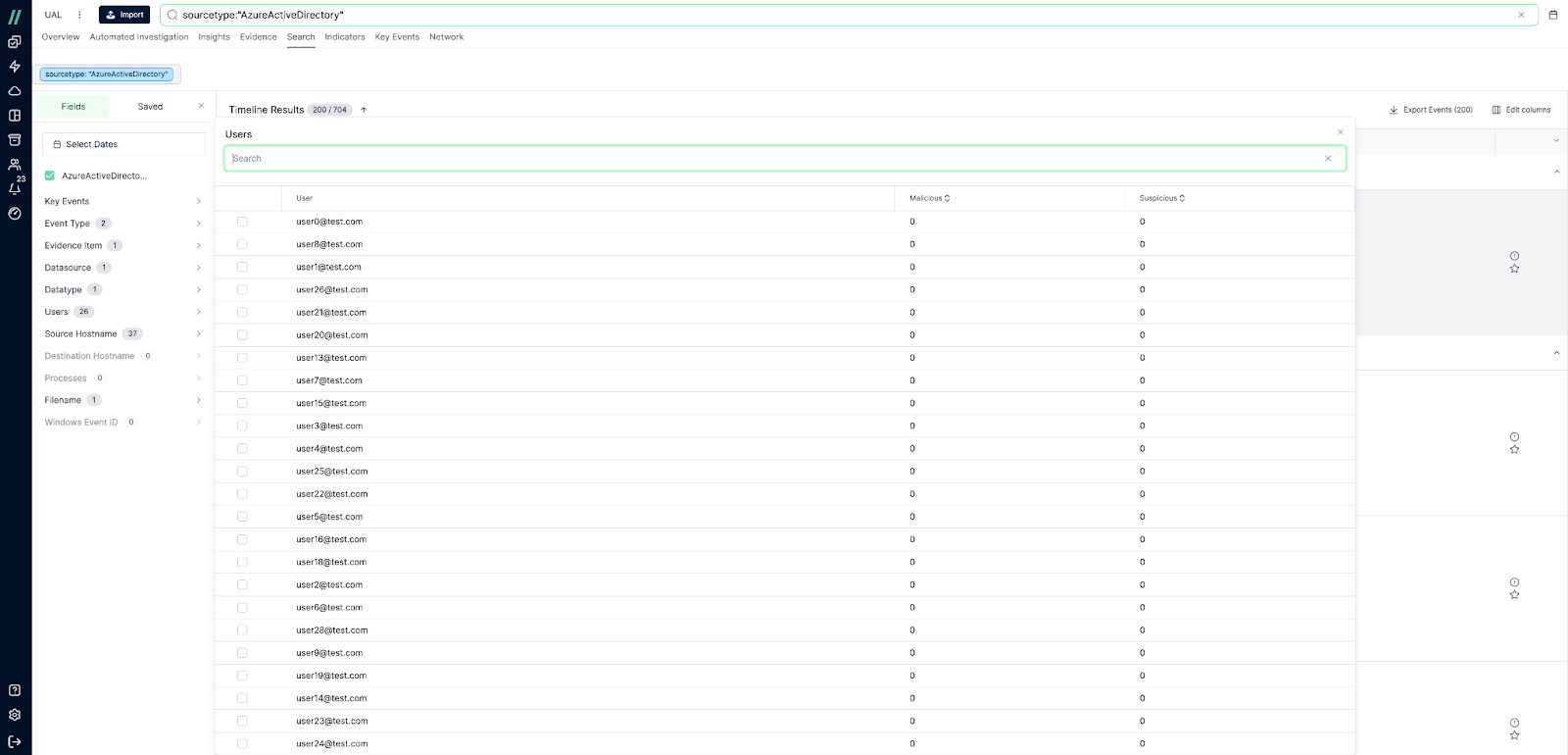
Searching the UAL in the Cado Platform
Cados unique approach to cloud security drastically reduces the amount of time and effort required to investigate and respond to threats identified in the cloud, on-premises, and in SaaS environments. Features such as single-click data capture allow rapid evidence collection across cloud, container, serverless, on-premises and SaaS is essential to reducing Mean Time To Response (MTTR). Once evidence is collected the Cado Platform leverages the full power of the cloud to process that data in parallel, meaning hundreds of data formats to be normalized in just minutes.
The Cado Platform also brings end-to-end automation to investigations providing a unified timeline of events and automated root cause analysis. Additionally, with its new AI Investigator, powered by Cado’s local LLM the platform gives a high-level summary of an incident and automatically analyzes potentially malicious files.
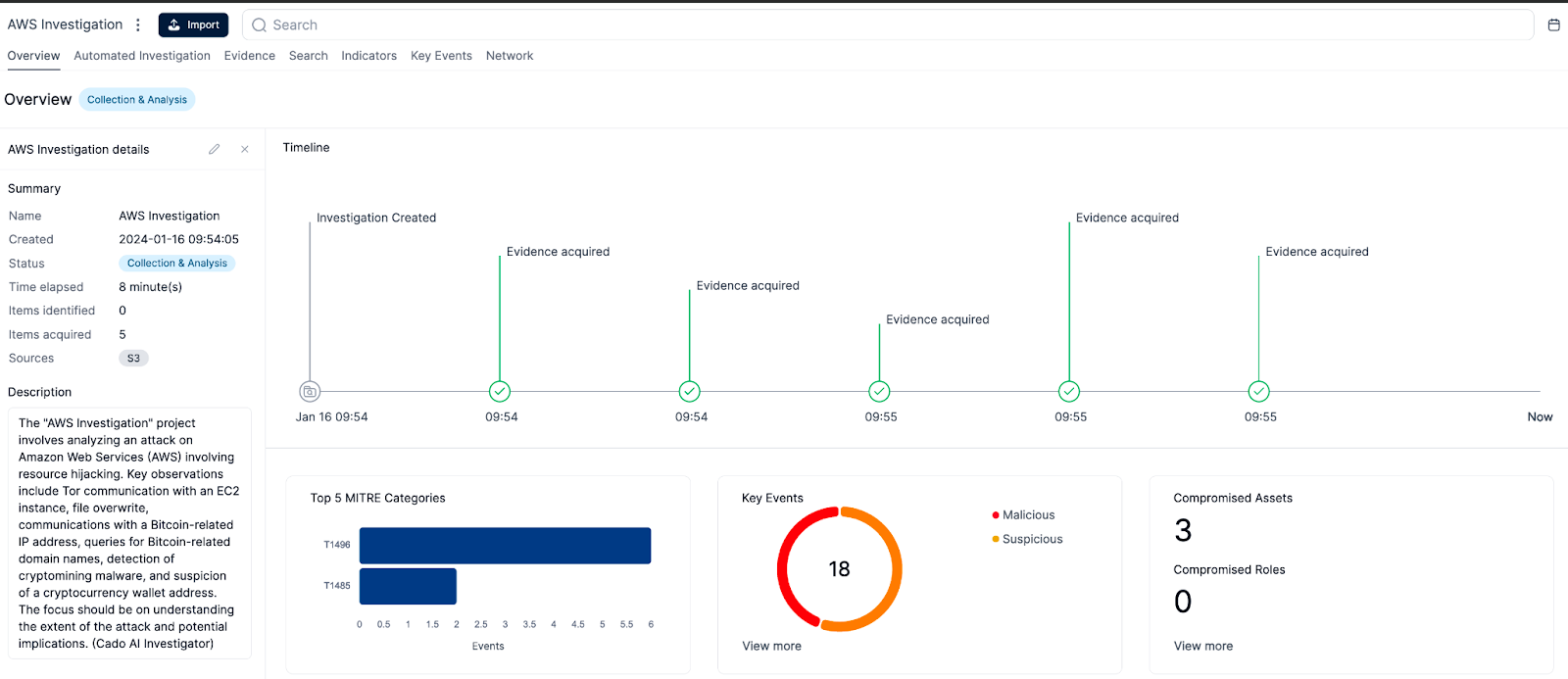
Cados AI Investigator at work
Finally, the platform presents all of its findings in one easy-to-view single pane view giving organizations a better understanding of the impact of threats with complete visibility across their entire ecosystem. Cado recently published a cheat sheet to help with investigating incidents in M365 environments providing an overview of the different logs, how to access them, and what they record. If you want to find out how the Cado Platform can help secure your SaaS environment schedule a demo with our team.
More from the blog
View All PostsHow Cado Helps Security Teams Perform Investigations Relating to Business Email Compromise (BEC) Attacks in M365
March 5, 2024Cado Introduces Support of SaaS Environments to Expedite Investigation and Response to Microsoft 365 Compromises
March 14, 2024Business Email Compromise (BEC): Understanding the Threat With Cado
March 19, 2025

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

