
Using the Unix-like Artifacts Collector and Cado Community Edition to Investigate a Compromised Linux System
Scenario: A Compromised Linux System
Imagine discovering that your Linux server has been compromised. This situation calls for immediate action to understand the extent of the breach, identify the cause, and mitigate any damage.
Collecting Data with the Open-source Unix-like Artifacts Collector (UAC)
While the full version of the Cado platform offers one-click data collection, Cado Community users can still use the open-source tool UAC to collect relevant data from a Unix-like system. We previously covered how KAPE can be used to collect data from a Windows system for import into Cado Community edition.
The process involves:
- Running UAC: Clone UAC from Github and execute UAC to collect a wide range of data, including system logs and user information.
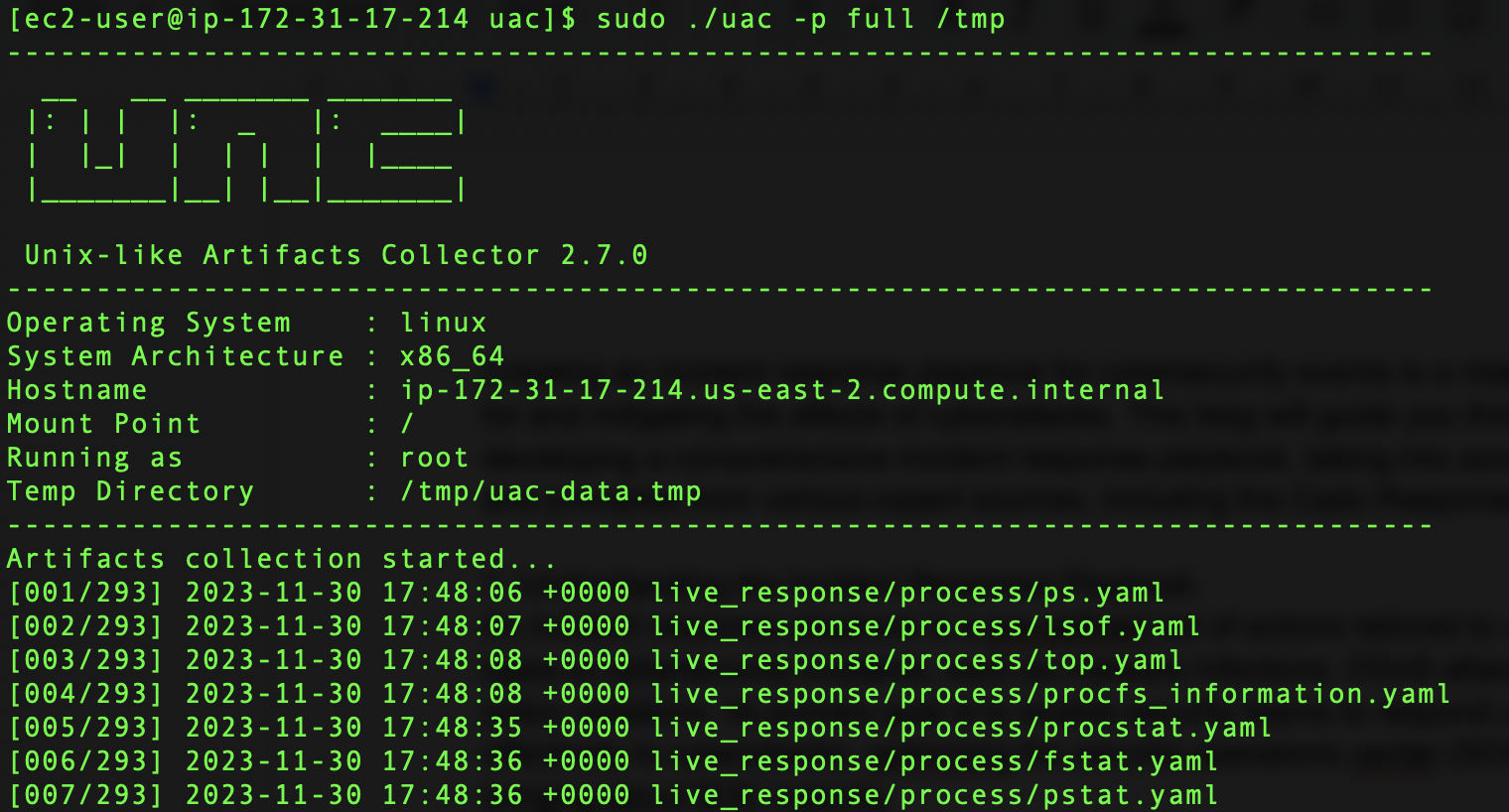
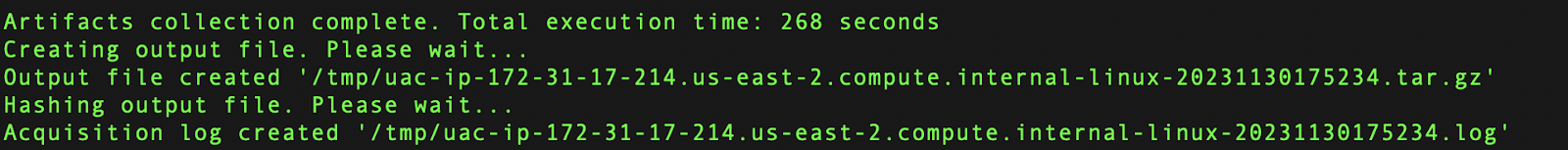
- Uploading to S3 Storage: Once UAC completes the data collection, it generates an archive. This archive should be uploaded to an S3 storage bucket. Community users will need to first convert the .tar.gz output file to a .zip file.
- Importing into Cado: From the S3 storage, import the collected data archive into Cado for analysis.
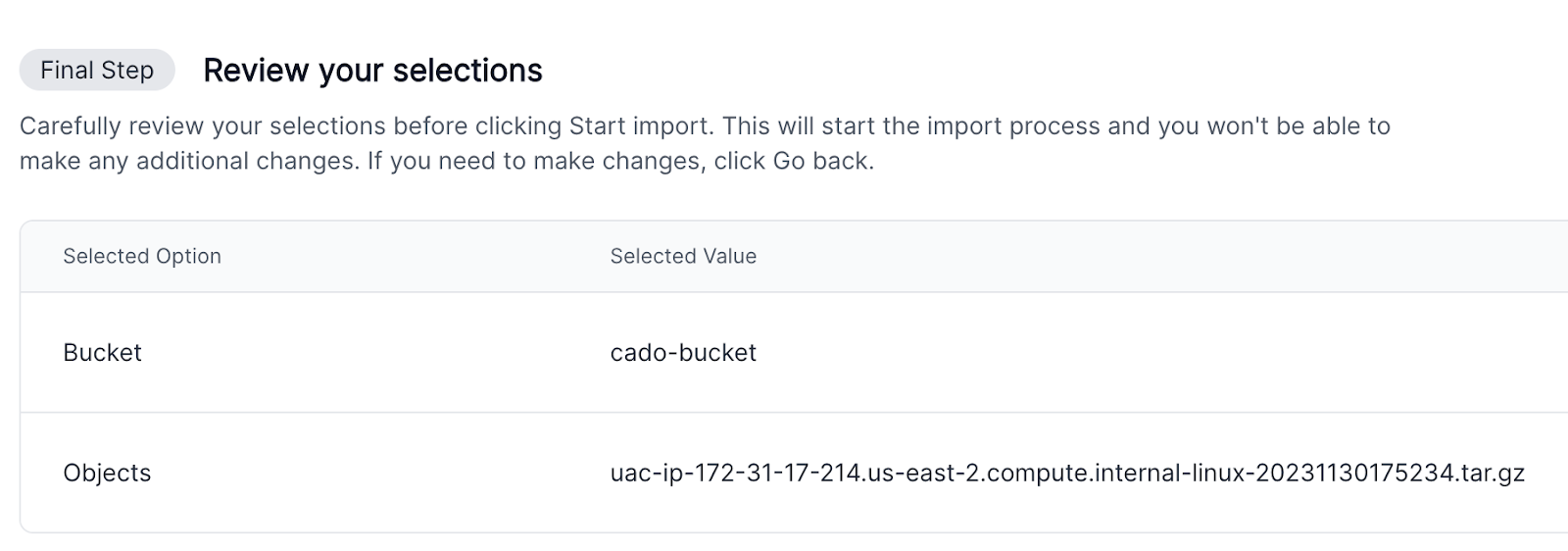
Automating the Investigation with Cado Community Edition
Cado is a powerful platform that simplifies the investigation process. The Community Edition, while not as feature-rich as the full version, still offers robust capabilities once data has been imported.
The investigation process typically involves:
- Automated Investigation: Cado initially presents an automated analysis of the data. This analysis highlights critical areas such as potential points of entry, affected files, and suspicious activities. This gives you some great starting points to investigate.
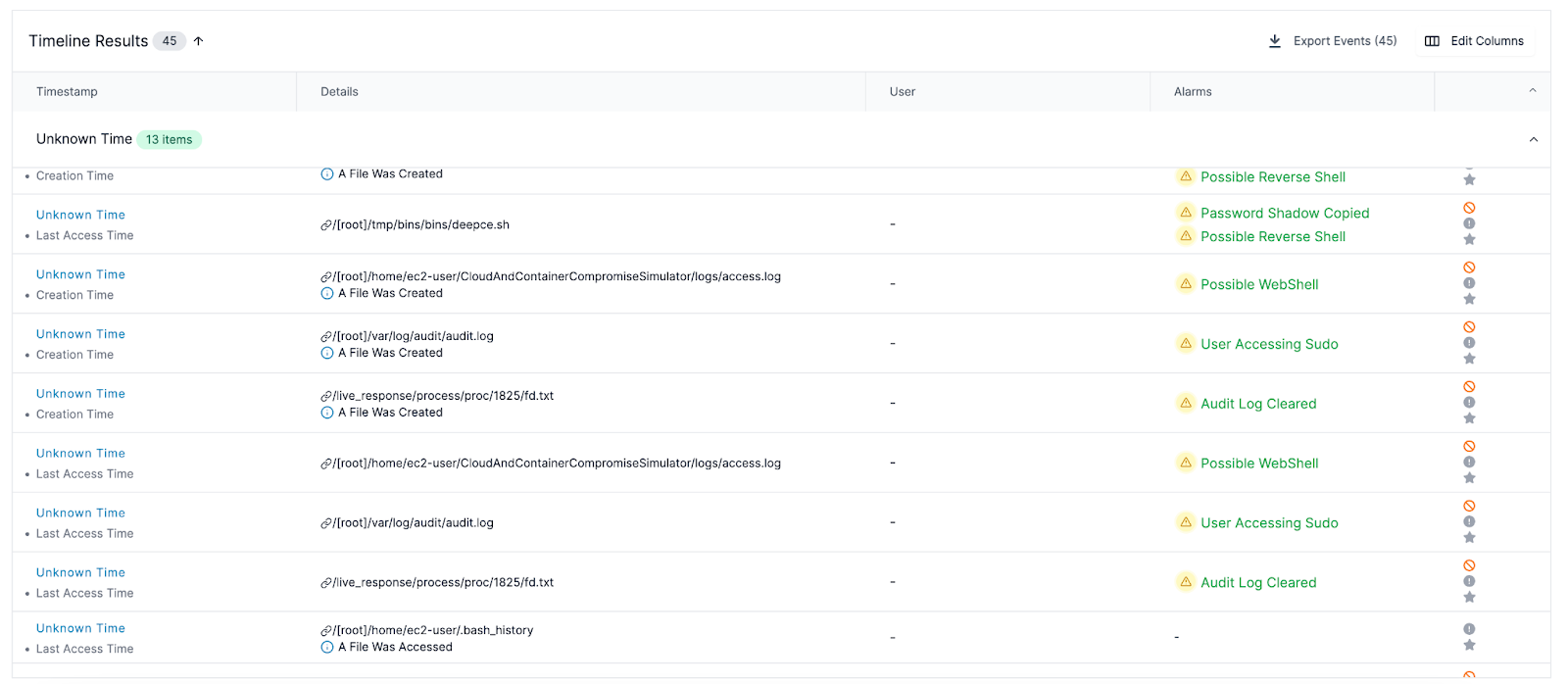
- Timeline Analysis: One of Cado’s strengths is its timeline feature. Investigators can view a chronological sequence of events leading up to and following the compromise. This timeline is crucial for understanding the attack’s progression and pinpointing the initial breach moment.
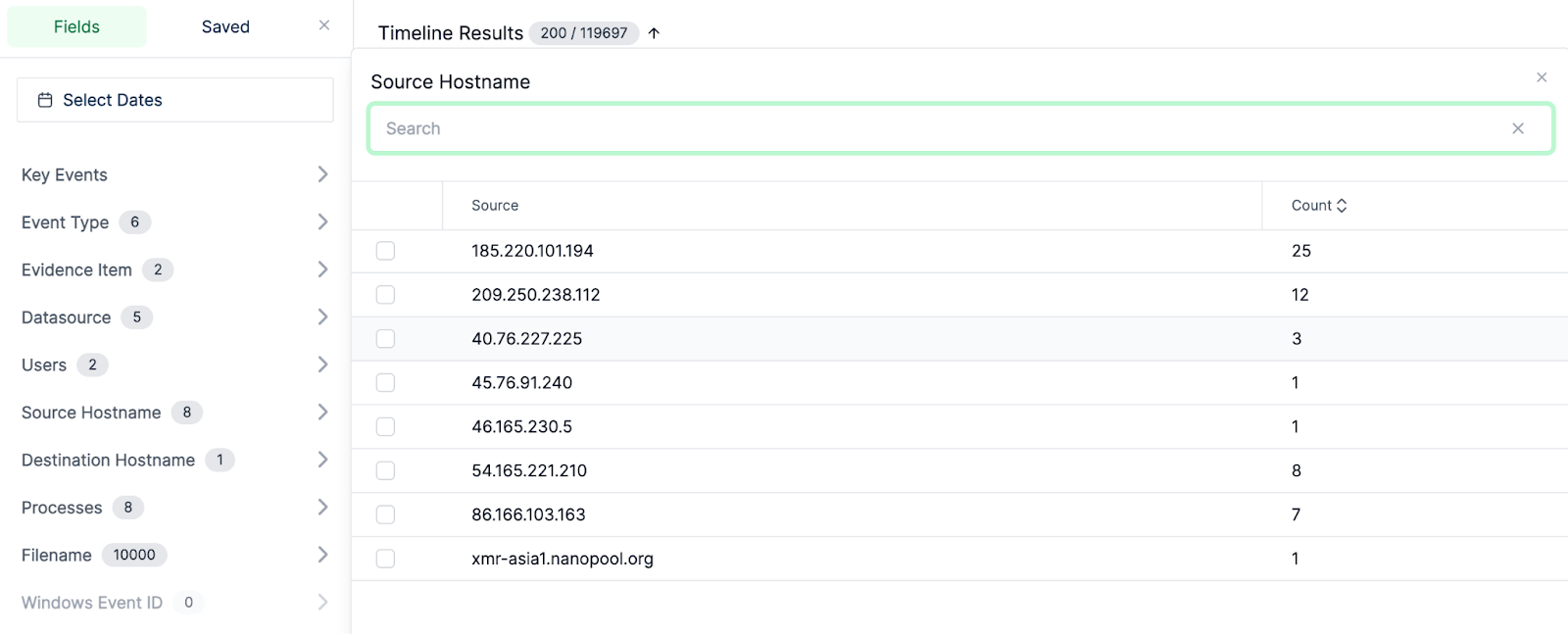
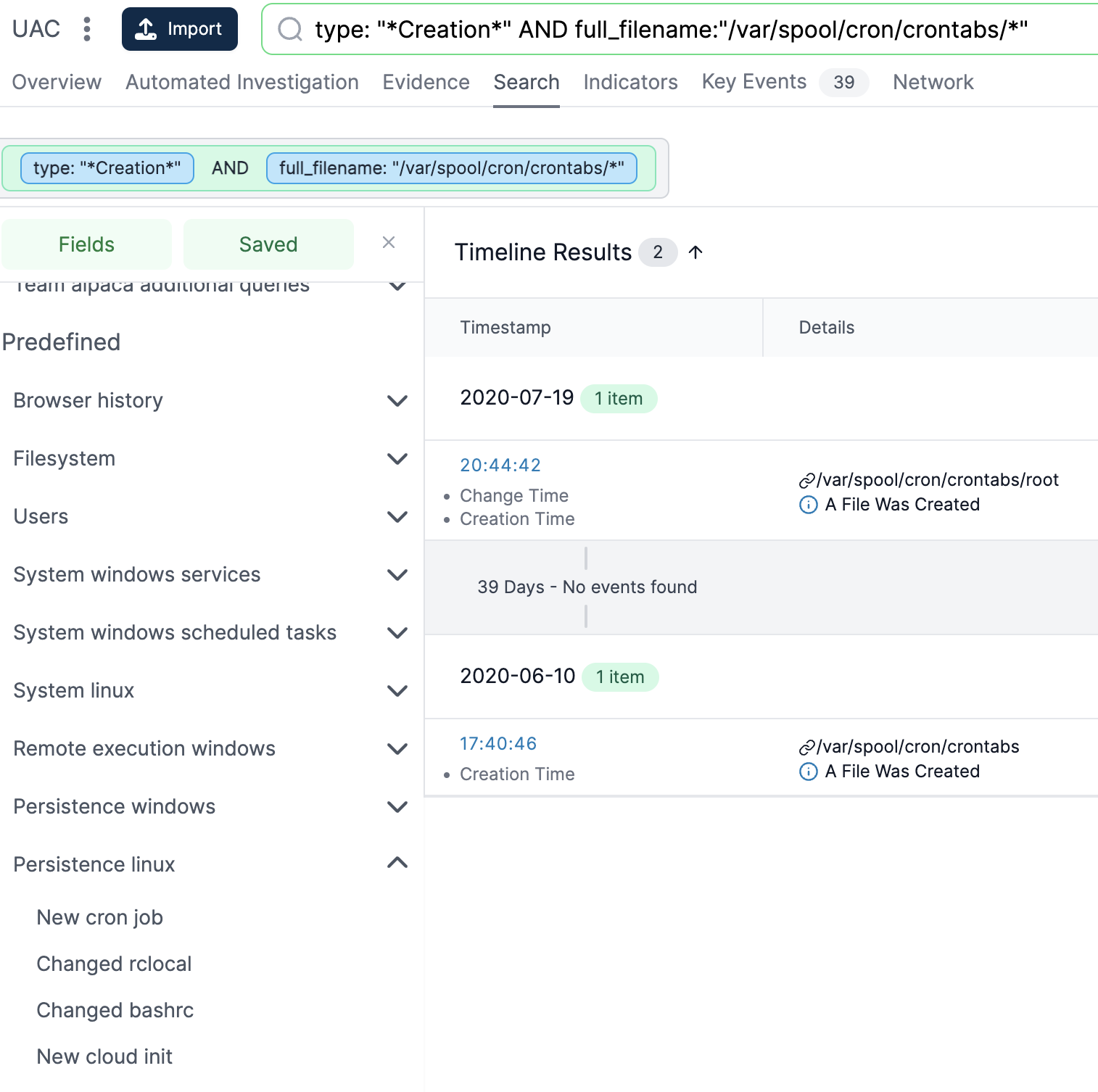
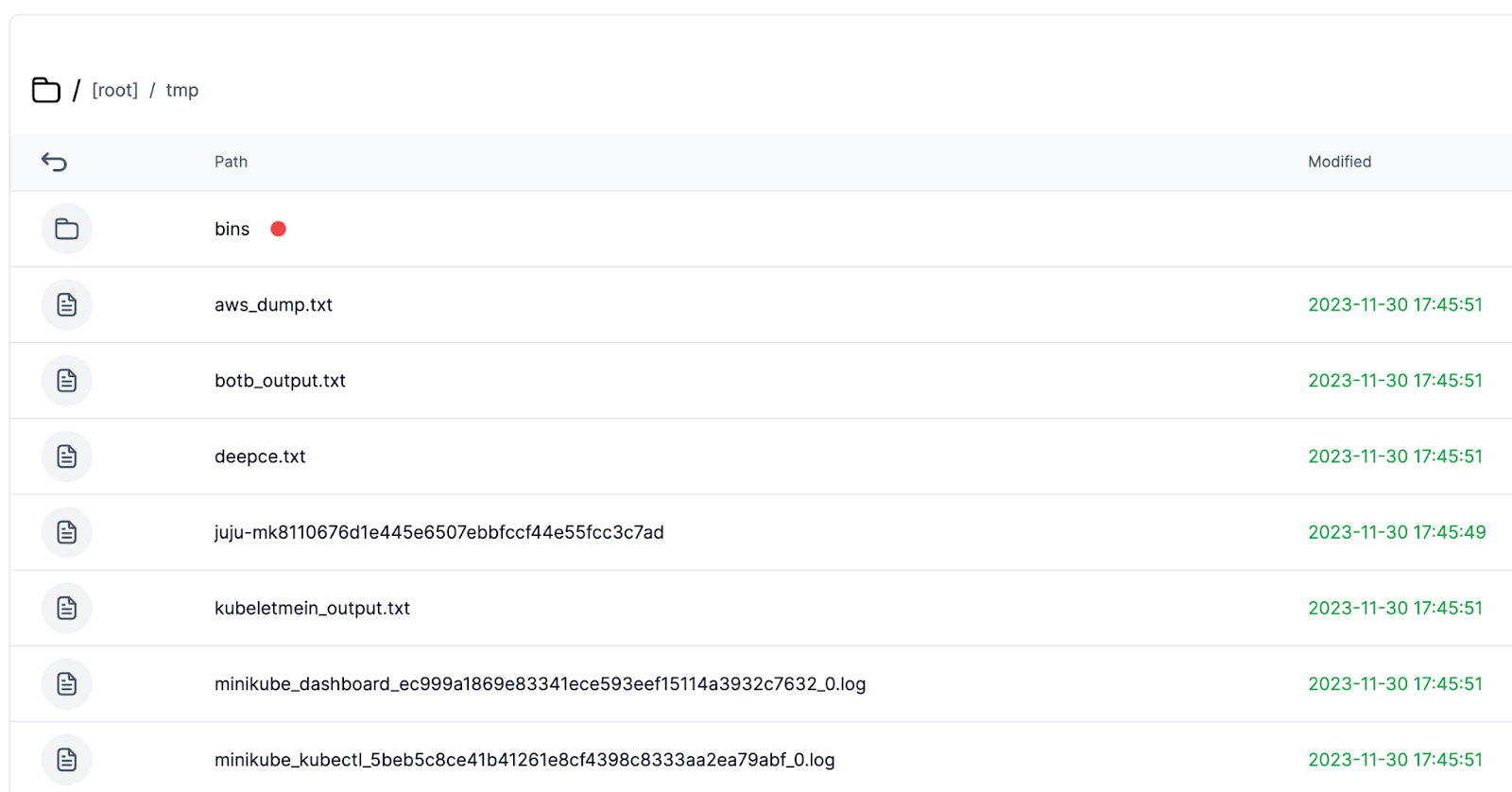
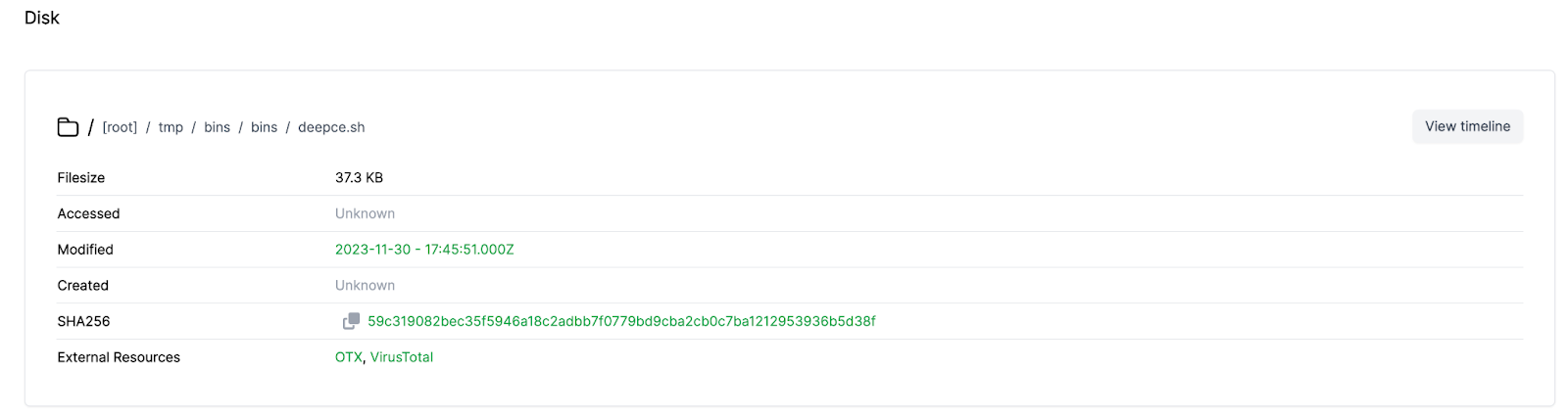
- Diving into Individual Files: Investigators can delve into specific files or artifacts for a more detailed examination.
Additional ResourcesFor more information on UAC, visit the UAC Github Repository. You can deploy the Cado Community edition from our website, or book a demo to see what the full version can do.
More from the blog
View All PostsEnhancing Cado Community Edition with Velociraptor
November 15, 2022DFIR with KAPE and Cado Community Edition
May 4, 2023Cado Security Launches Free Community Edition of its Platform
August 9, 2022

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.
