Security analysts and incident responders face mounting pressure from multiple fronts. Firstly, alert fatigue is real. Security teams are inundated with a flood of alerts, with 61% of analysts receiving more than 500 alerts per day. This results in an inability to investigate everything, and the reality is that over ⅓ of cloud alerts remain untouched, leaving risk on the table.
Further, the rapid migration to cloud resources has security teams playing catch up. While they attempt to apply traditional on-prem tools to the cloud, it’s becoming increasingly clear that they are not fit for purpose. Especially in the context of forensics and incident response, the cloud presents unique complexities that demand cloud-specific solutions. For example, organizations are increasingly adopting services from multiple cloud platforms (in fact, according to Gartner’s 2020 Cloud End-User Buying Behavior Survey, 76% of respondents had adopted multi-cloud infrastructure), and container-based and serverless set ups have become the norm. Security analysts already have enough on their plate, it’s unrealistic to expect to be cloud experts too.
Compounding the issue, there is a lack of DFIR talent. With a global cyber security staffing shortage of 3.4 million people, approximately 71% of organizations are affected. Let’s double click into this, why is this such an issue?
- Highly specialized skill set: DFIR professionals need to have a deep understanding of various operating systems, network protocols, and security architectures, even more so when working in the cloud. They also need to be proficient in using a wide range of forensic tools and techniques. This level of expertise takes a lot of time and effort to develop.
- Rapid technological changes: The cloud landscape is constantly changing and evolving with new services, monitoring tools, security mechanisms, and threats emerging regularly. Keeping up with these changes and staying current requires continuous learning and adaptation.
- Lack of formal education and training: There are limited educational programs specifically dedicated for DFIR. Further, an industry for cloud DFIR has yet to be defined. While some universities and institutions offer courses or certifications in digital forensics, they may not cover the full spread of knowledge required in real-world incident response scenarios, especially for cloud-based environments.
- High-stress nature of the job: DFIR professionals often work under tight deadlines in high-pressure situations, especially when handling security incidents. This can lead to burnout and high turnover rates in the profession.
To help organizations close the DFIR skills gap, it's critical that we modernize our approaches and implement a new way of doing things in DFIR that's fit for the cloud era. Modern cloud forensics and incident response platforms must prioritize usability in order to up-level security teams. A platform that is easy to use has the power to:
- Enable more advanced analysts to be more efficient and have the ability to take on more cases
- Unlevel more novel analysts to perform more advanced tasks than ever before
- Eliminate cloud complexity– such as the complexities introduced by multi-cloud environments and container-based and serverless set ups
How Cado Brings Usability to Cloud Forensics and Incident Response
The Cado platform brings usability to cloud forensics and incident response via the following feature set:
Data Enrichment: Automated correlation of collected data with threat intelligence feeds, both external and proprietary, delivers immediate insight into suspicious or malicious activities. Data enrichment expedites investigations, enabling analysts to seamlessly pivot from key events and delve deeper into the raw data.
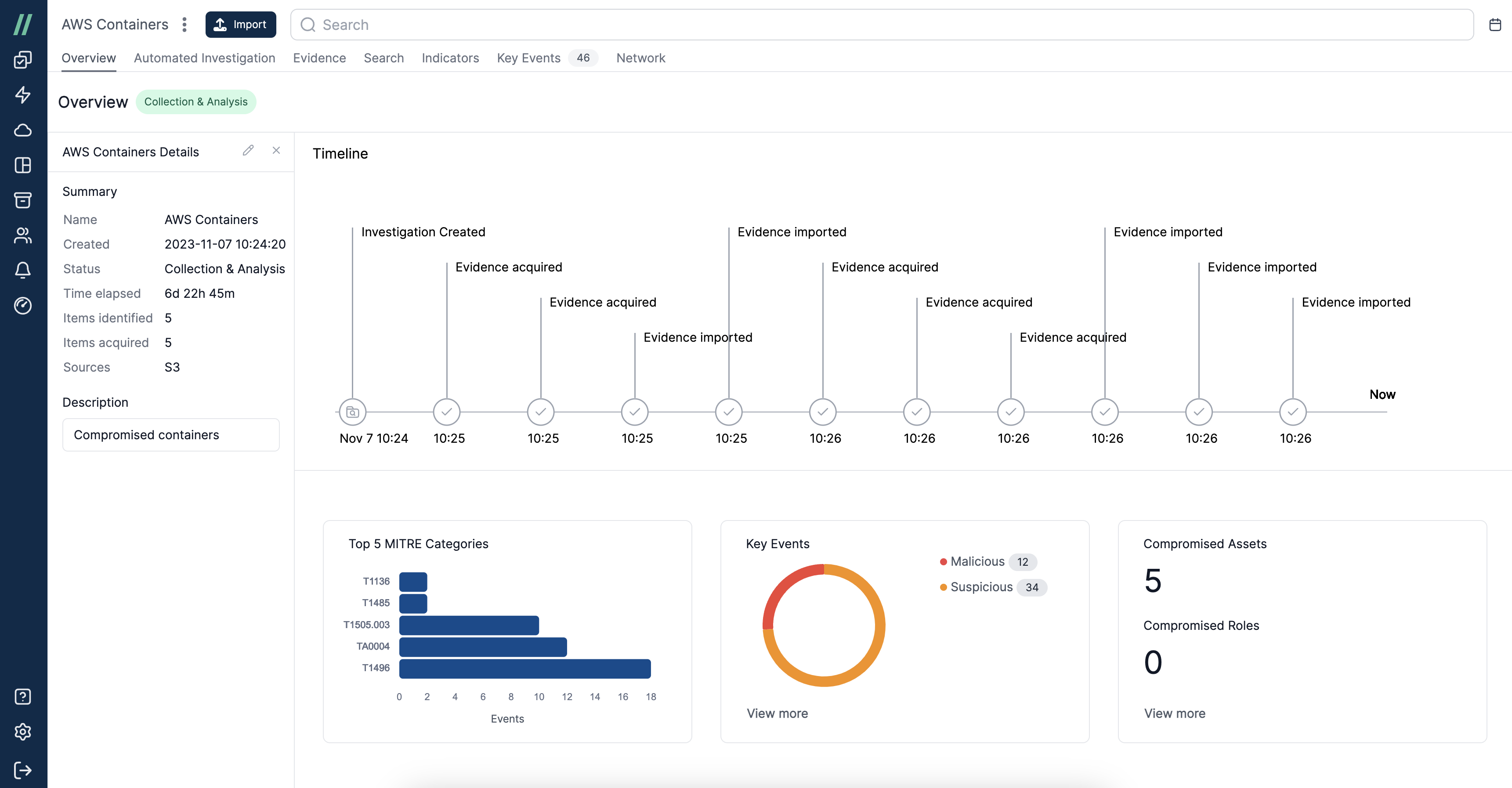
Diving into Keys Events from Cado's Project Overview Dashboard
Single Timeline View: A unified perspective across various cloud platforms and data sources is crucial. A single timeline view empowers security teams to seamlessly navigate evidence based on timestamps, events, users, and more, enhancing investigative efficiency. Pulling together a timeline has historically been a very time consuming task when using traditional approaches.

Cado Security's Timeline View
Saved Search: Preserving queries during investigations allows analysts to re-execute complex searches or share them with colleagues, increasing efficiency and collaboration.
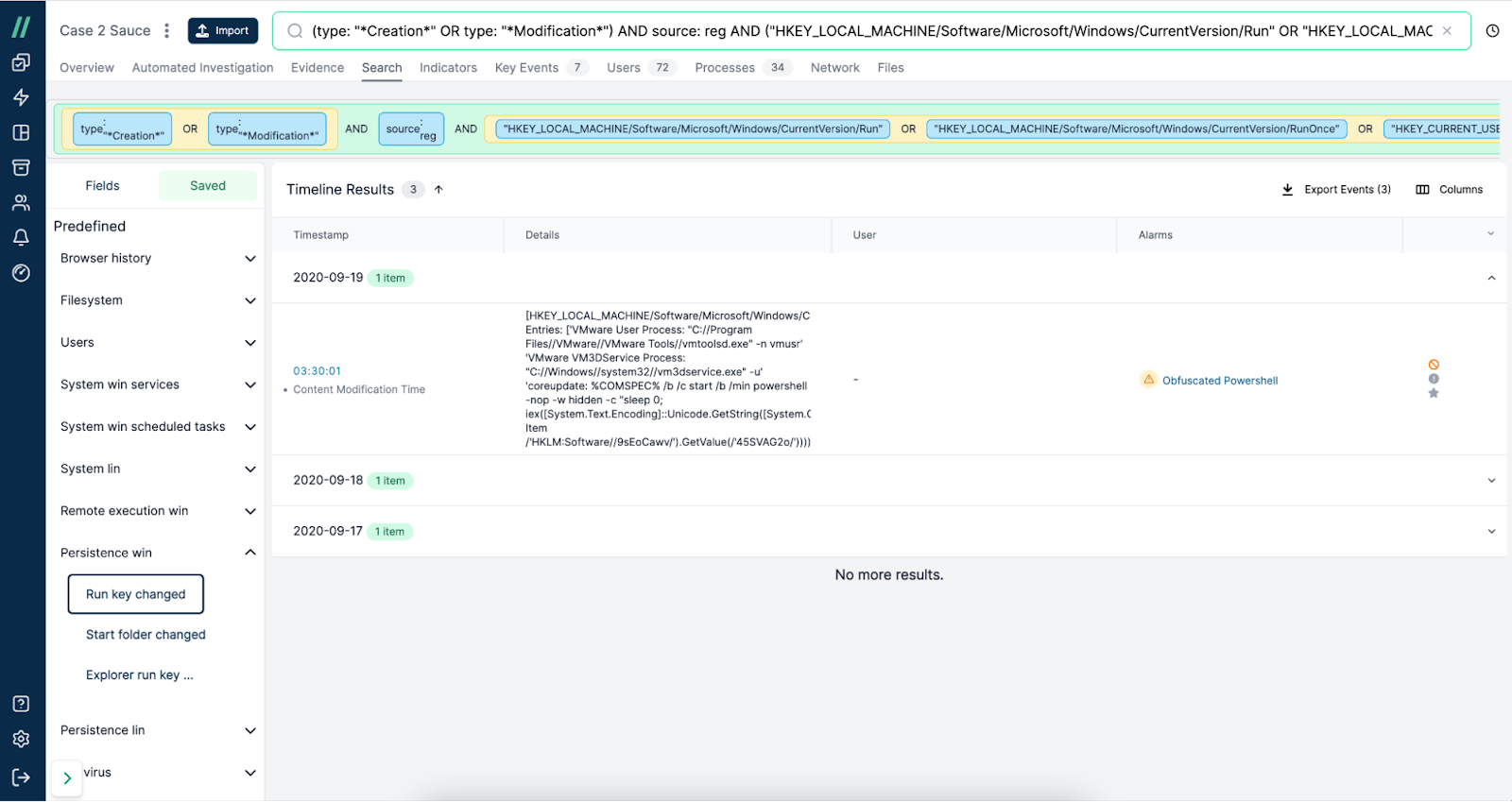
Cado's Saved Search
Faceted Search: Facet search options provide analysts with quick insights into core data attributes, facilitating efficient dataset refinement.
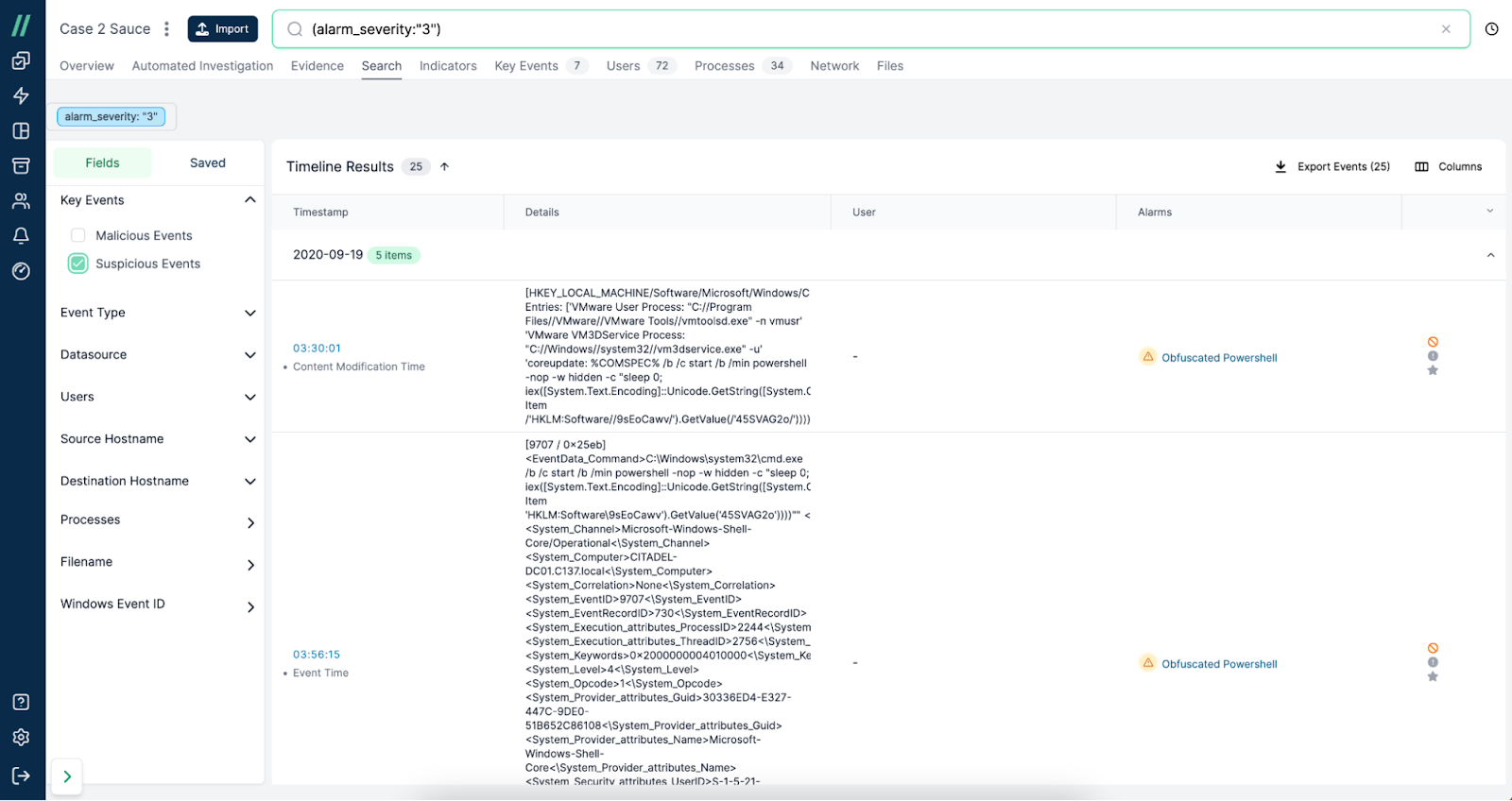
Cado's Faceted Search
Cross-Cloud Investigations: Analyzing evidence acquired from multiple cloud providers in a single platform is crucial for security teams. A unified view and timeline across cross cloud is critical in streamlining investigations.
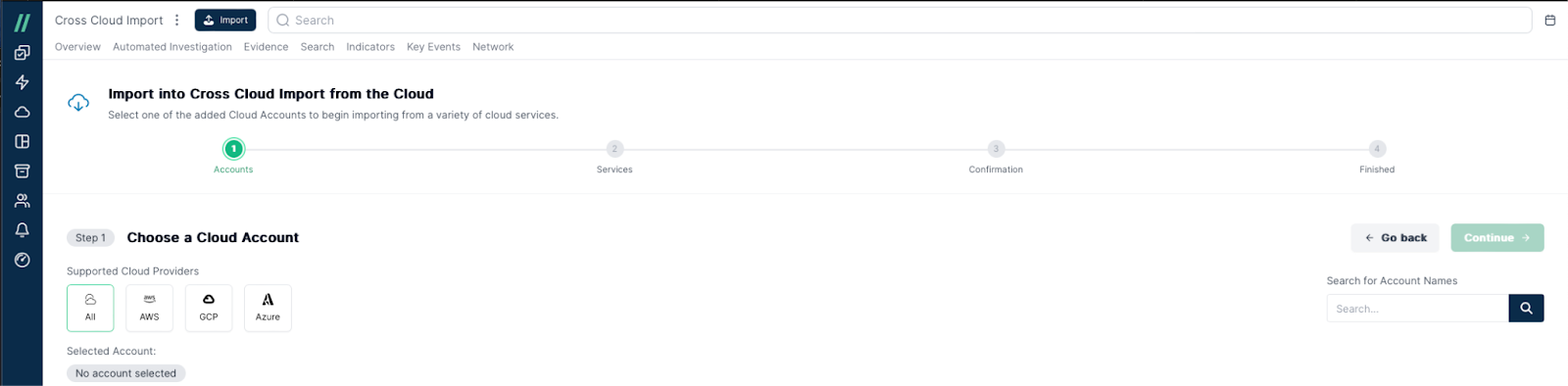
Cross-Cloud Imports in the Cado Platform
At Cado, we believe that security teams shouldn’t require deep cloud and incident response expertise to secure their environment. By prioritizing usability, common investigative tasks are simplified and expedited, from capturing the right data to identifying an incident’s root cause, scope, and impact.
If you want to see how Cado can bring ease of use to your cloud investigations, contact our team to schedule a demo.
More from the blog
View All PostsForensics or Fauxrensics? 5 Core Capabilities for Cloud Forensics and Incident Response
February 23, 2024The Future of Incident Response: AI-Powered Investigations with Cado Security
October 21, 2024Supercharging Investigations With Cado’s New Timeline
August 9, 2023

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

