
Cloud Incident Response in the Fast Lane: Leveraging Automation to Reduce MTTR
Swift identification, investigation, and containment of threats is vital to reducing Mean Time to Response (MTTR) and mitigating cloud risk. The utilization of automation to expedite data collection and attack containment is absolutely key to the process.
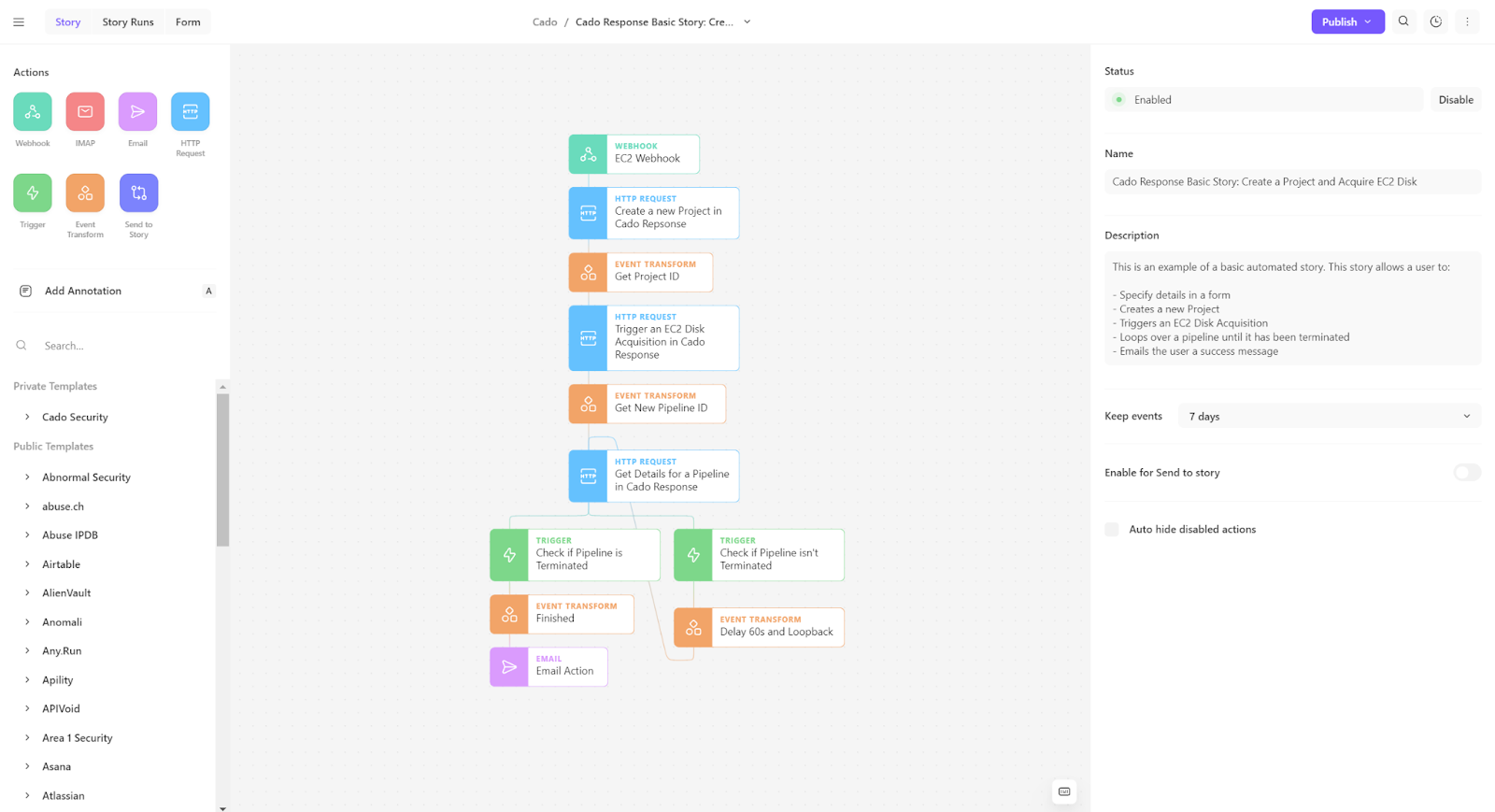
Automated cloud forensics through Tines SOAR and the Cado Platform
Tired of Waiting on Your Cloud Team?
One of the most common challenges organizations face is gaining access to forensics data. In many large enterprises, access to cloud resources typically falls outside the responsibility of the security team, leading to a lengthy and laborious process to obtain evidence. For example, security analysts often have to manually submit requests to the cloud team to gain access to potentially compromised assets. This process could take days to weeks; and in the meantime, the attacker is free to carry out malicious actions while the security team is playing catch up.
However, enabling immediate access to forensic evidence in the cloud is possible by integrating a cloud forensics and incident response platform with incident management tools. For example, cloud forensics and incident response platforms that enable security teams to integrate with security solutions like AWS GuardDuty, Microsoft Defender, XDR, CNAPP, SOAR, and SIEM by leveraging built-in automation rules, ensures collection actions are automatically triggered immediately upon incident detection.
Forensics Investigations in Ephemeral Environments is Possible
Automating data collection is especially important when it comes to ensuring the ability to perform forensics investigations and incident response in ephemeral environments. Particularly in ephemeral environments, where resources are constantly spinning up and down, data can vanish if not captured swiftly. In this scenario, automation becomes critical.
Preventing Spread and Damage
Automation can extend beyond data collection; it also plays a vital role in ensuring rapid response. By automating response actions, such as system containment across potentially compromised resources, allows security teams to limit damage and prevent further spread while a deeper forensic investigation takes place in the background.
By automating both data collection and system containment upon detection, security teams are empowered to significantly reduce the time it takes to respond to threats identified in cloud, container, and serverless environments.
Cado Expedites Incident Response in the Cloud

Automated collection and response in the Cado Platform
The Cado Platform aims to automate as much of the incident response as possible, from data capture to root cause analysis. The platform offers rapid access to detailed forensic data in various environments like multi-cloud environments, containers, and serverless setups. This enables security teams to better manage risks identified in these environments and reduce overall MTTR (Mean Time to Response).
With Cado, security teams can:
- Bypass their cloud team: With automation rules and integration with popular detection tools, there's no need to manually request access to resources. The Cado platform can automatically collect the evidence security teams need, without having to submit tickets to the cloud team to gain access to potentially compromised resources.
- Investigate ephemeral environments: With resources constantly spinning up and down, ephemeral environments consisting of resources, such as containers, can prove to be the most challenging to investigate. Dynamic by nature, in these environments, evidence can quickly disappear before an analyst gains access. With Cado, security teams can automatically collect and preserve evidence captured across ephemeral resources so that it's available for investigation purposes.
- Respond quickly: The Cado platform also offers automated remediation capabilities to ensure security teams can quickly contain threats without human intervention. By leveraging built-in automation rules, response actions can be triggered based on various criteria according to what's best practice for the organization. A common use case is to automatically contain potentially compromised systems upon detection of malicious activity to minimize damage and spread.
Interested in learning more? Contact our team to see a demo.
More from the blog
View All PostsAccelerating Incident Response with Automation
March 14, 2025Automated Remediation in the Cloud: Empowering Efficiency with Cado
August 3, 2023Bridging the Detection and Response Gap With CIRA
September 28, 2023

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.
