I’m a big fan of the Pyramid of Pain. I know I know…the ‘Pyramid of Pain’ sounds more like a wrestling move and less like a cyber-related discipline (something like this - thanks to Bing AI for generating):

Here's the real Pyramid of Pain - it’s essentially a model that refines the ‘idea of difficulty’ there must be for attackers to change their routine. The higher up the model you go, the more difficult you are making that attacker’s life.
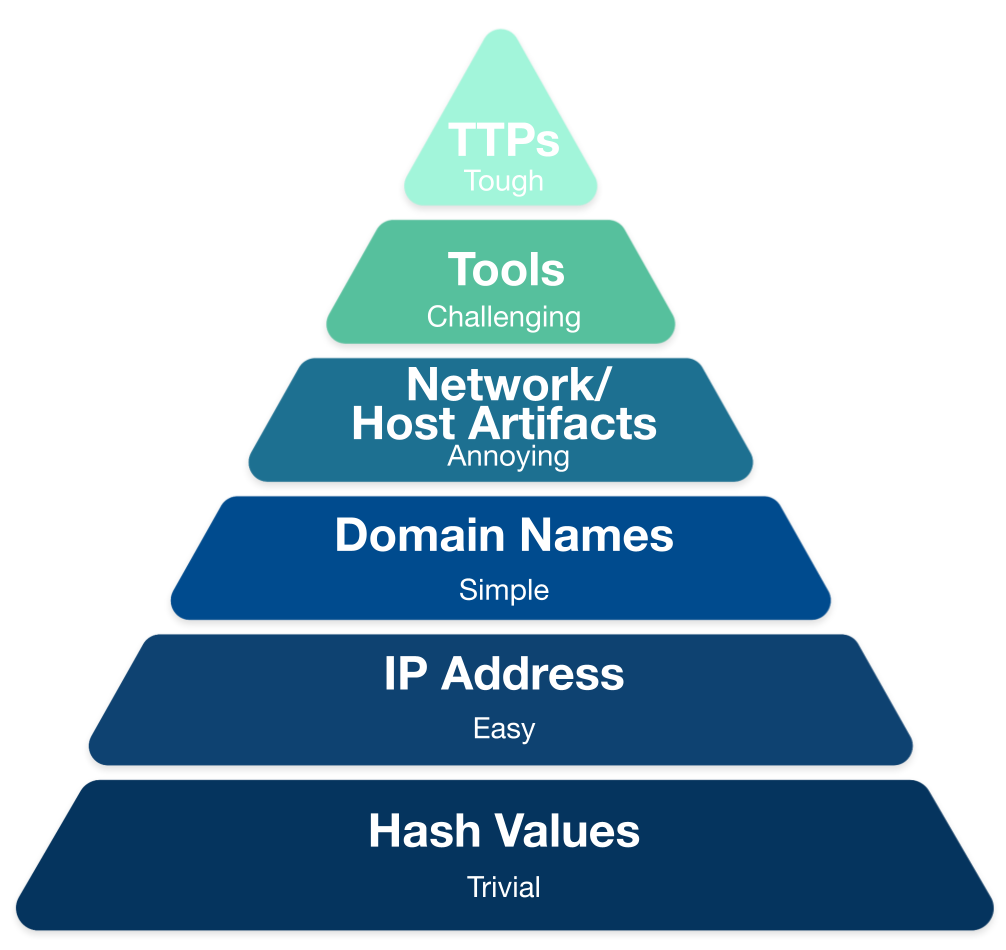
To me, the Pyramid of Pain (I’ll refer to it as PoP throughout this blog) is one of the must fundamental ways to understand the need to thwart ‘hacktivity’ attempts beyond traditional AV or ‘next generation anything’ tools.
For example, if your company can detect malicious activity based on potentially malicious SSL or TLS certificates (and you couldn’t detect that one year ago), you are winning or you’re heading in the right direction. If your company can find or catch evil in suspicious windows logs via automated means (and you could’t do that one week ago), you are winning as a company.
Catch my drift?
Any competitive CISO/Security Officer out there should and would want to progress up and further into this model.
Speaking of CISO’s, with the recent charges brought against Timothy Brown (CISO at Solar Winds), I thought resuscitating a blog with reference to Solar Winds would be good review. Here’s a good article discussing both the PoP (to a certain degree) and Solar Winds:
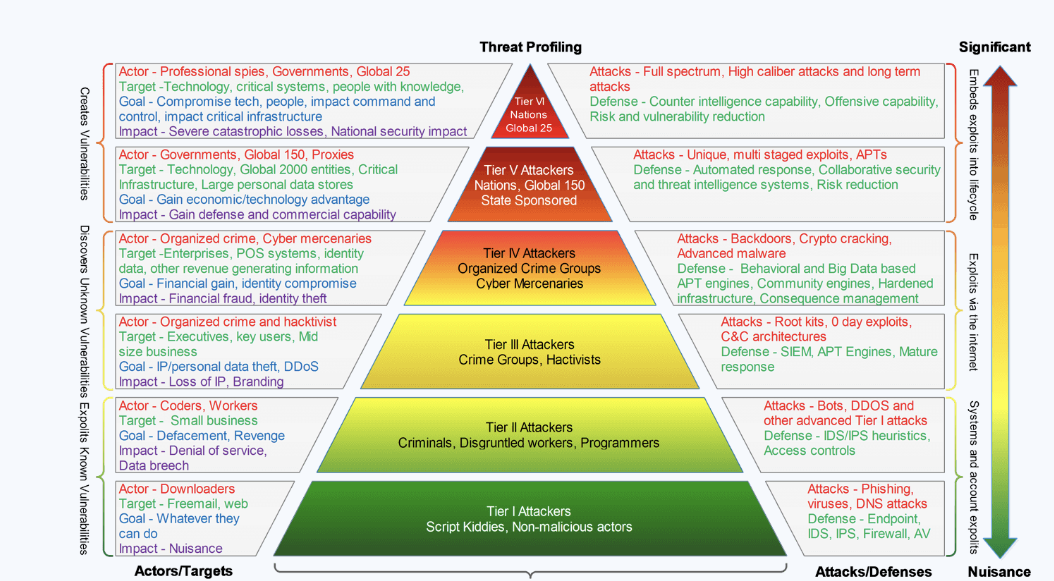
I love the context provided above by Dynamite Analytics. The overlay shown between the PoP and the superstar (or not-so-superstar) attackers across the PoP matrix might bring you to your knees in attempting to understand it all, but (net-net), here’s what this model is trying to tell us all…
If you’re an attacker and you sit at the top of this pyramid, well…you’re among the elites or best in the world at what you do. For an even better look & feel of this particular model, take a gander here. Now that has been baselined, let me ask you the most important question.
How good do you want to be?
Part of it is, well, how good do you need to be at detecting sophisticated cloud or multi-cloud compromise? That’s absolutely part of it. But, organic desires that come from within will lead to better results IMHO. So, the real question again is, How good do you want to be?
I’d hope really good - maybe you even want to be the best there is. To have data resilience strong enough to thwart even nation states situated at the top of the pyramid is, well, very impressive. Without needing to say it though, the ‘inevitable’ budget problem always comes to mind for everyone (in order to have that kind of data resilience).
That’s why it is super important to capture a Threat Profile of your community. Knowing the attackers’ mindset well enough to know the ambiguous word ‘risk’ with relation to hacker groups and communities. Basically, you need to know if it’s practical for the top echelon to even knock on your door.
In other words, which attacker groups out there want your data bad enough to single you out as a company?
I think we could all universally say, “if my company has a public domain, then we are at risk of cybercrime-motivated actors.”
That’s great. We know that much. We also know there are cyber institutions out there that will profile you at a cost, and help you understand where your greatest risks lie (beyond the basic cybercrime motivations).
So don’t just assume it’s ‘the little guys’ wanting to steal your company’s money. It’s important to profile beyond that mark.
Now that that's all been said, I’ll discuss why I’m bringing this up or writing a blog about this in the first place. If you want to progress ‘upwards’ within the PoP (with your own capabilities), you’ll need someone or something else already resting at that higher echelon to help you progress.
Along those same lines, deep cloud breaches are authored by sophisticated actors with very dedicated skill sets. Why do I make this claim? Simply because cloud is all-new territory, ever-evolving and with all new learning and all new rededicating oneself to understanding all of the important cloud elements or moving parts. This takes time (hence, they are skilled and further the Dynamite model).
Attacking cloud-based resources requires a unique skillset and mindset. So much so that MITRE created a specific ATT&CK model for cloud-based intrusions. These cloud attacks can be much more advanced or far more sophisticated than your classic commodity attacks (like a BEC, for example).
To go with the above, plenty of companies haven’t thought about building out a cloud-specific incident response process yet. Here at Cado, we want to help. We’re prepared to facilitate the enablement of cloud forensics and incident response for your organization.
Cado is primed to enable to your security team with responding to these types of advanced and ever-changing cloud attacks. We enable incident responders, the SOC, anyone with the mission of preparing, finding and confirming evil lurking within their CSP or Cloud Service Provider footprint.
Just how good do you want your company to be?
We’re here to help. Reach out to our team.
More from the blog
View All Posts

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

