Cado Response delivers forensic-level detail without forensic-level effort. Through the power of automation, the Cado Response platform enables security teams to capture critical evidence across server-based, container-based, and serverless environments with ease.
In this blog, we’re going to walk through a simple example of investigating a compromised ECS instance where we’ve installed xmrig with Cado Response.
First, we'll select Import ECS:
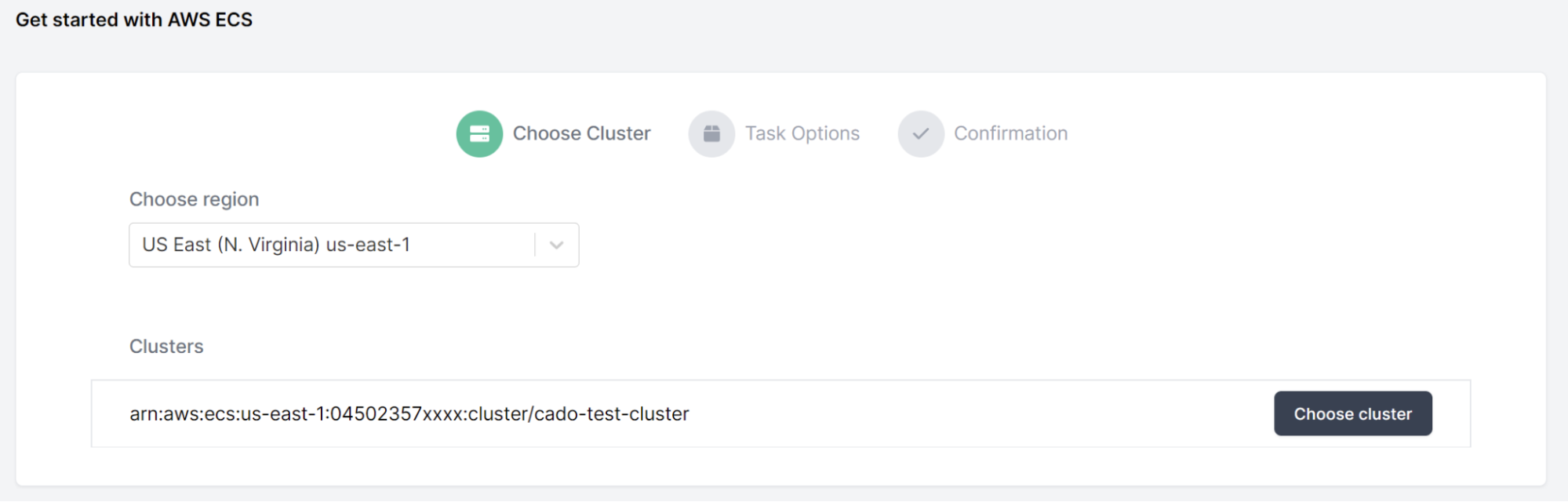
Then, we'll choose the compromised Cluster and Task:
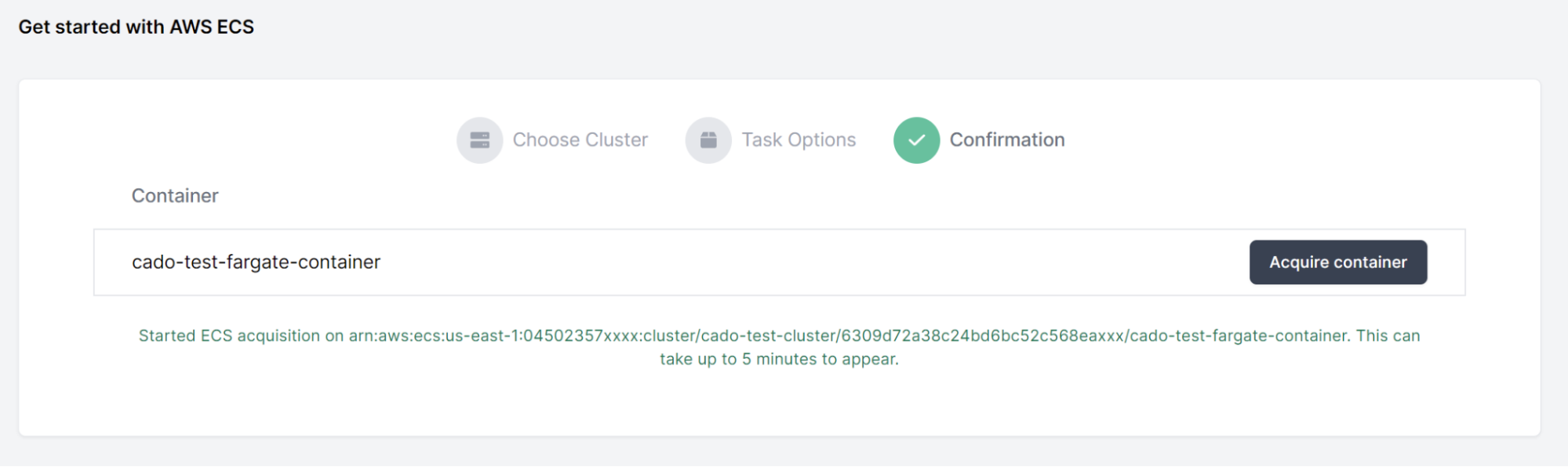
Then we’ll click Acquire Container. Cado Response will now automatically collect all the key logs and forensic artifacts from the container to enable an investigation.
Within minutes, we can immediately see suspicious activity has been flagged:
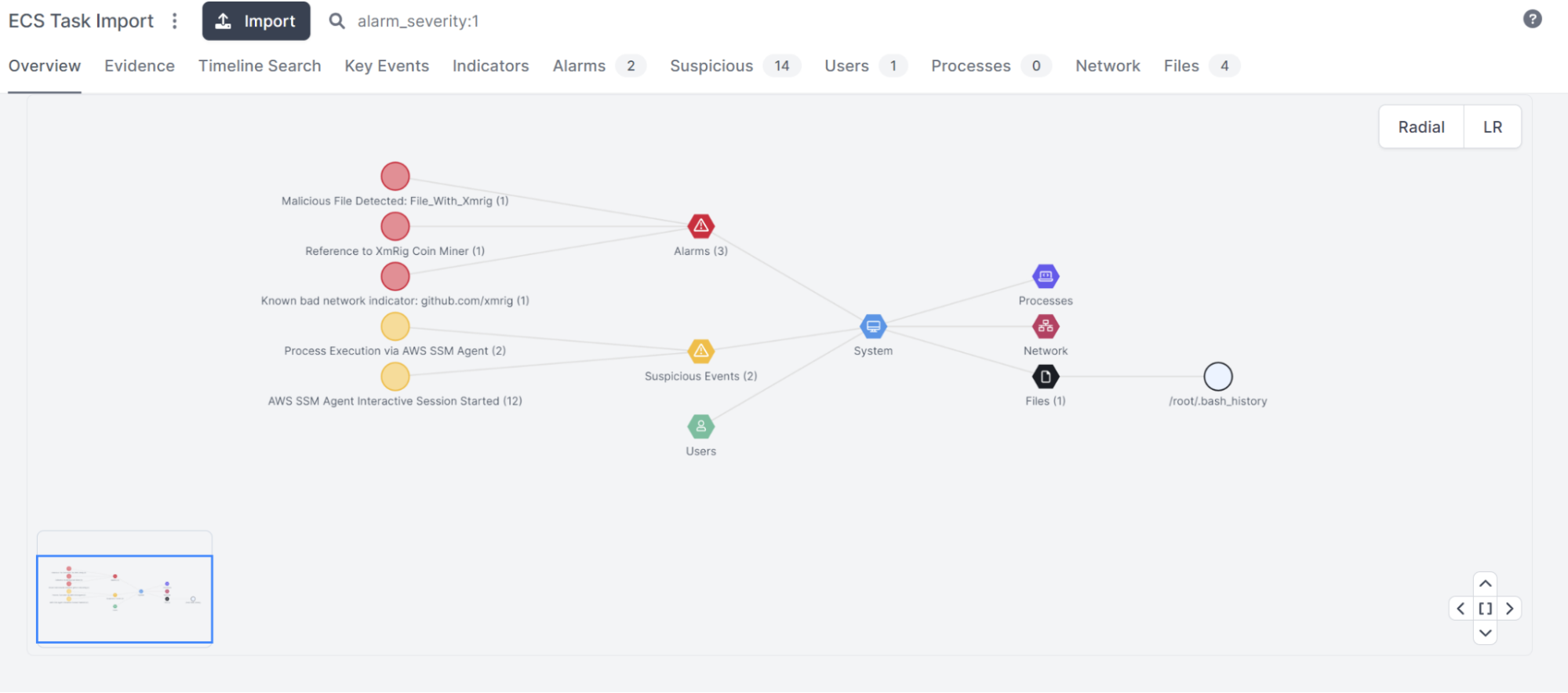
Diving deeper, we can see the alarms are for xmrig:
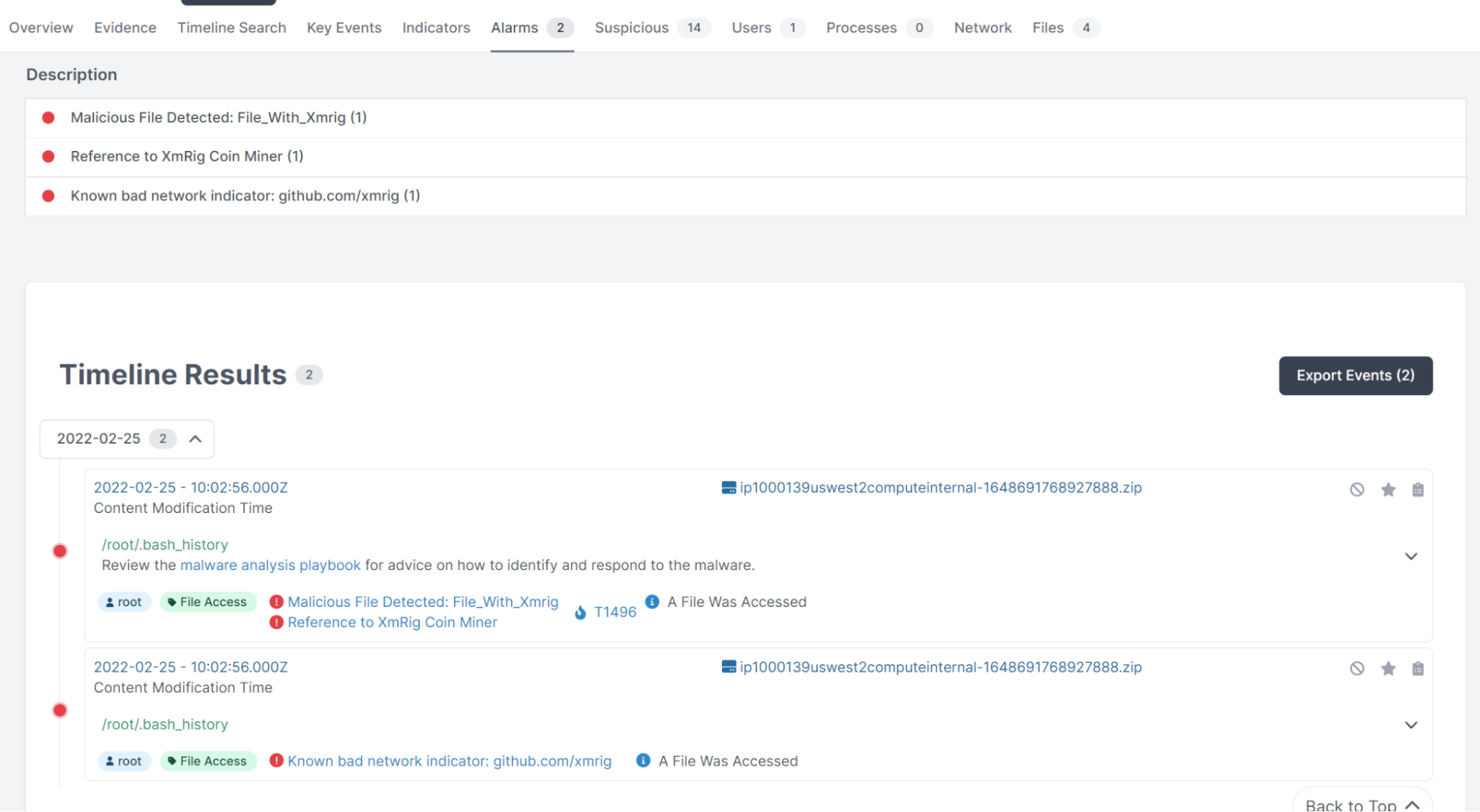
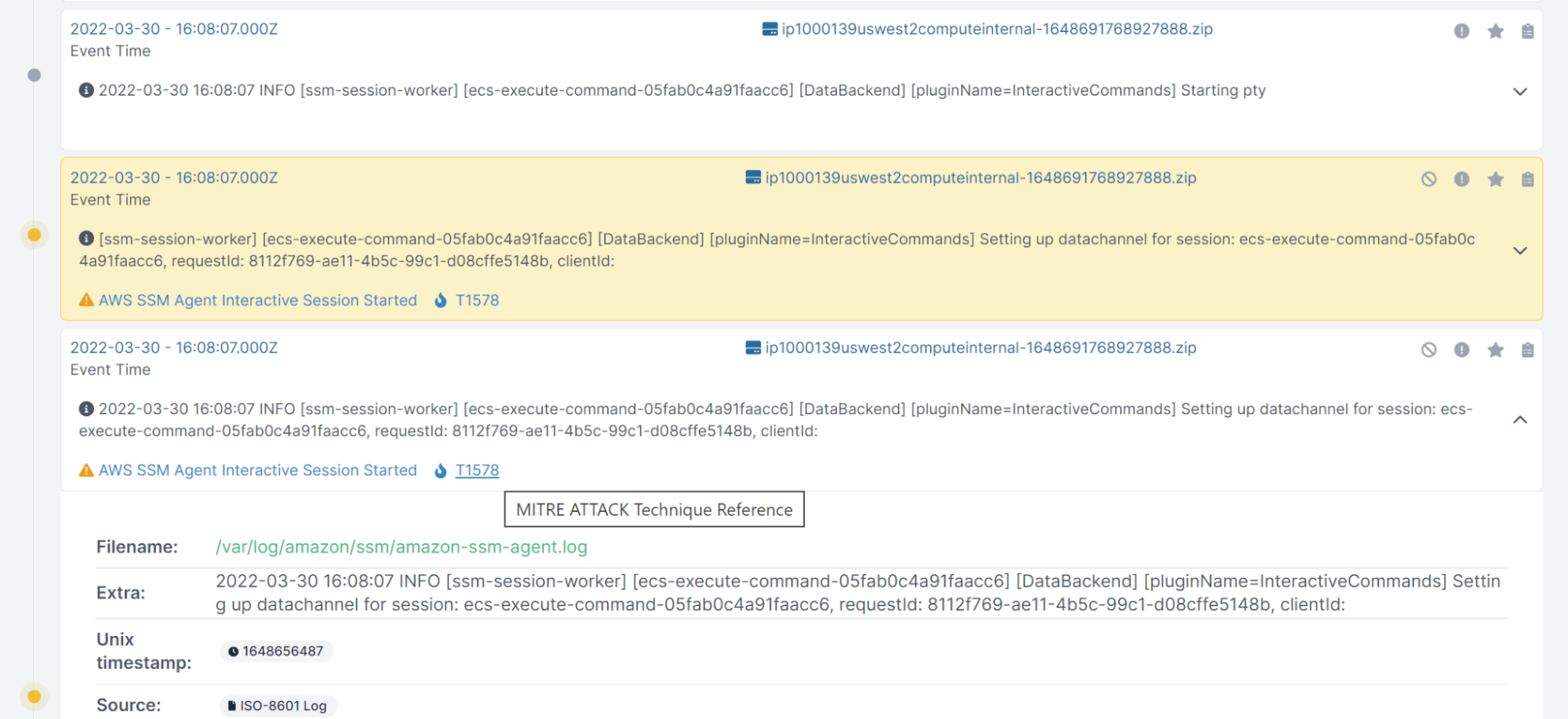
By clicking the timestamp, we can start to investigate surrounding activities:
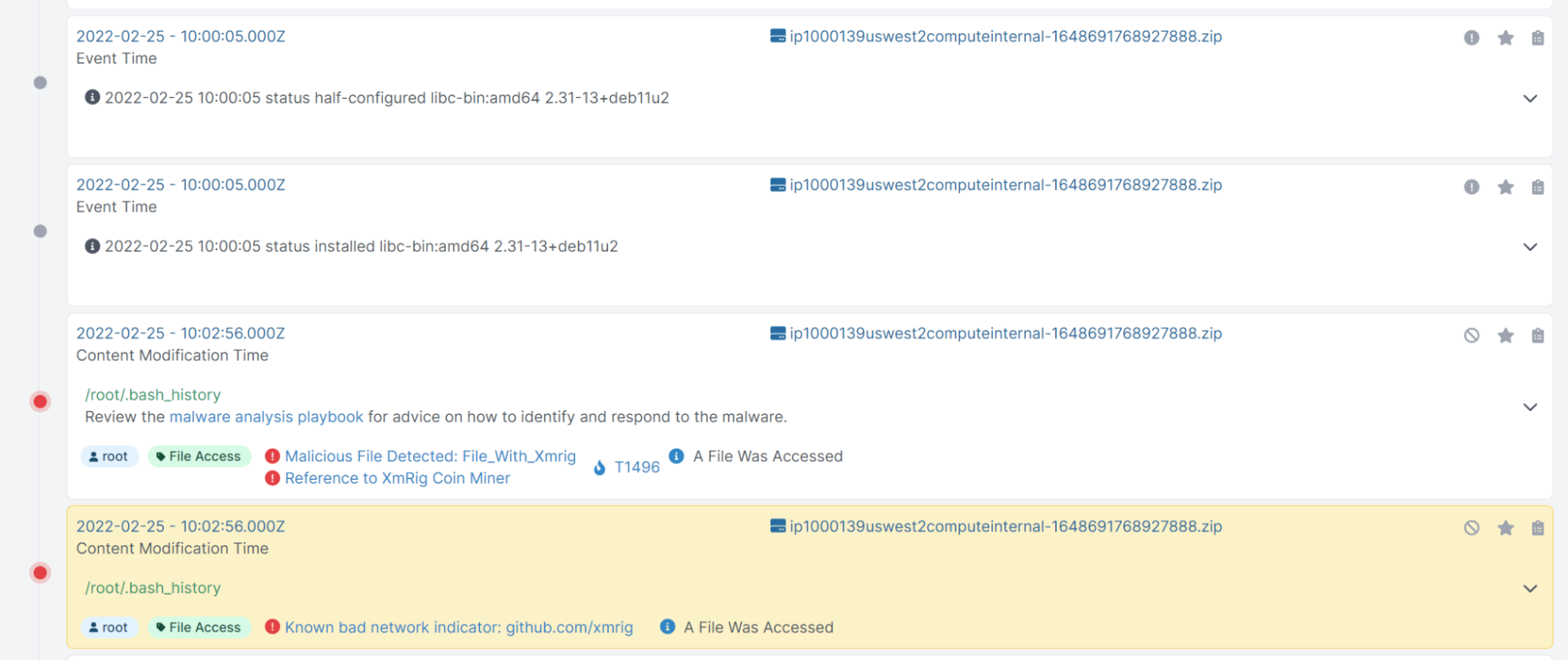
While there are thousands of events occurring within a couple of minutes, there are a few ways we can narrow in our investigation -- the easiest being to filter by Malicious or Suspicious events:
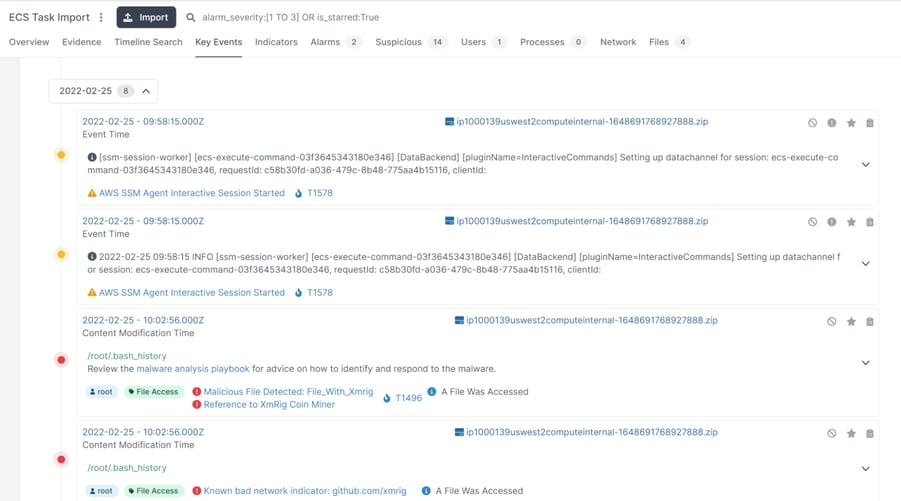
From here, we can see someone executing commands directly using ECS Execute (which AWS deploys via the SSM agent installed into containers). By pivoting over to the specific log, we can see activity from a few IPs. We can also download the log to view it locally:
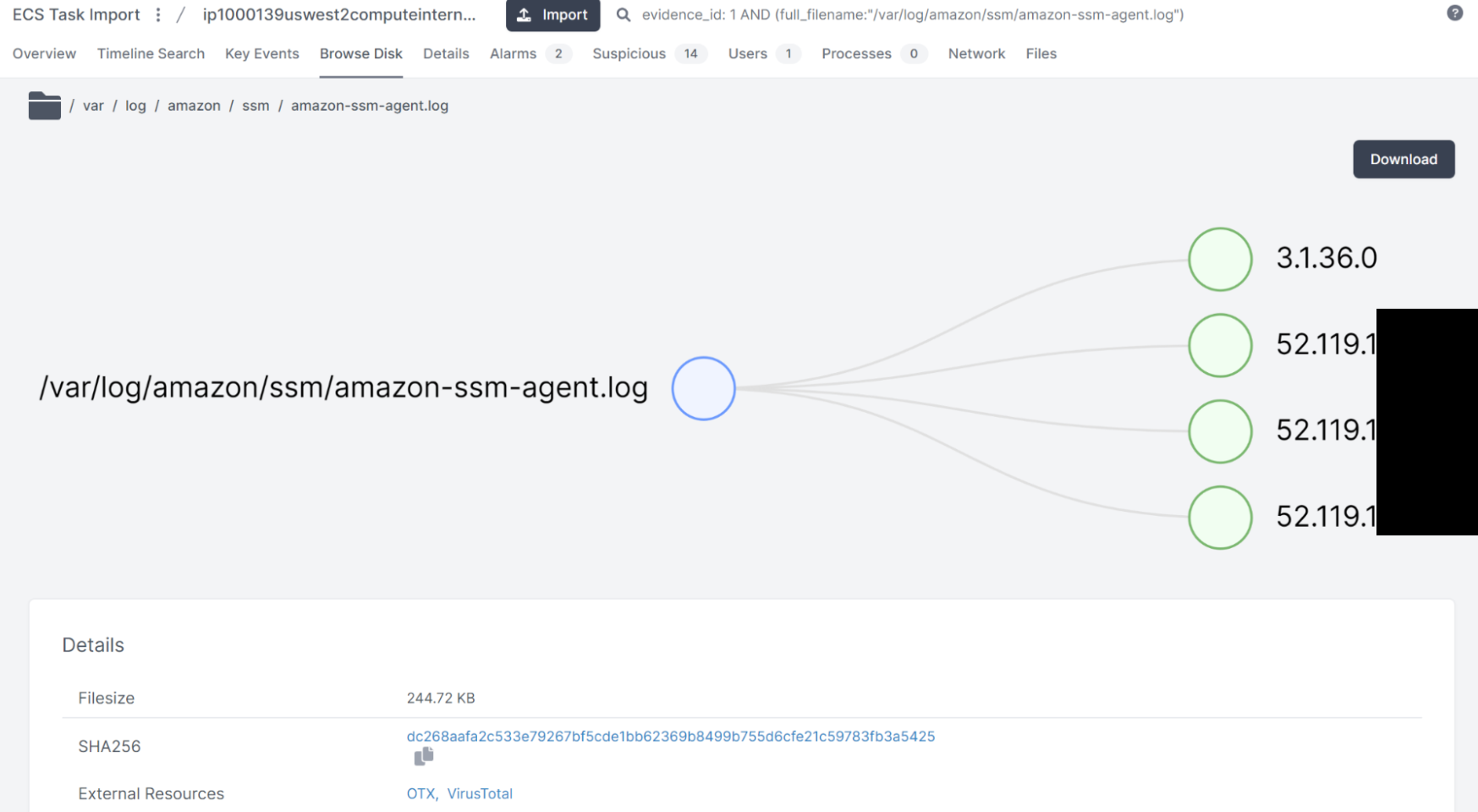
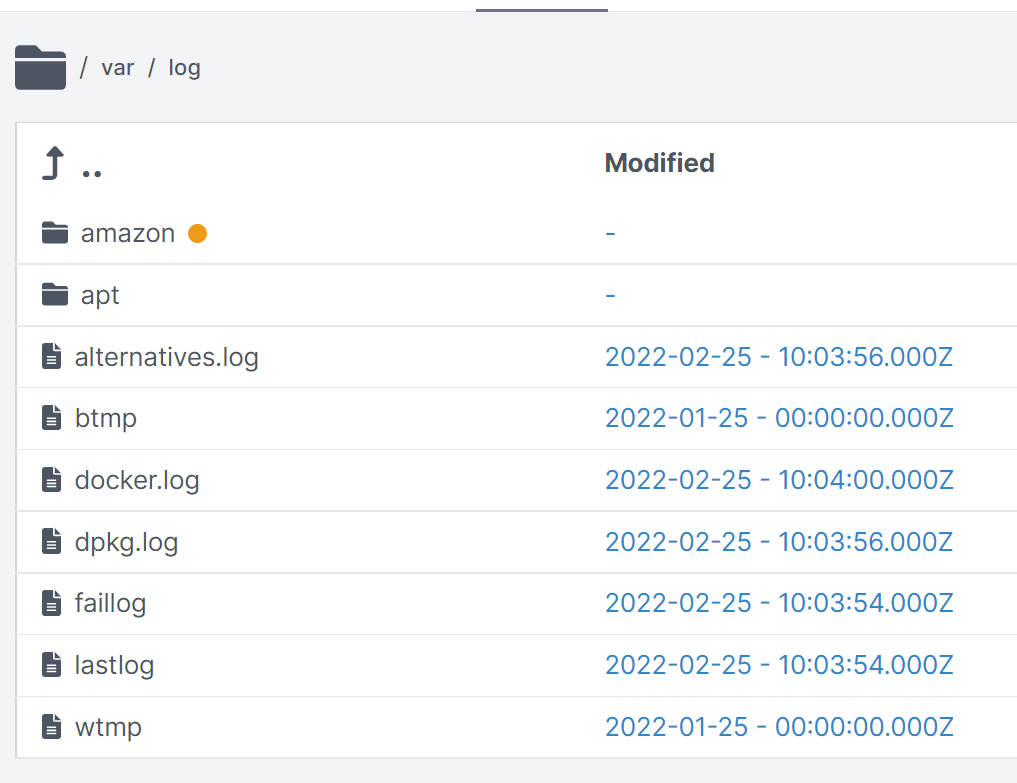
In addition, we also have full access to the collected files and can browse through the file system retrieved from the container:
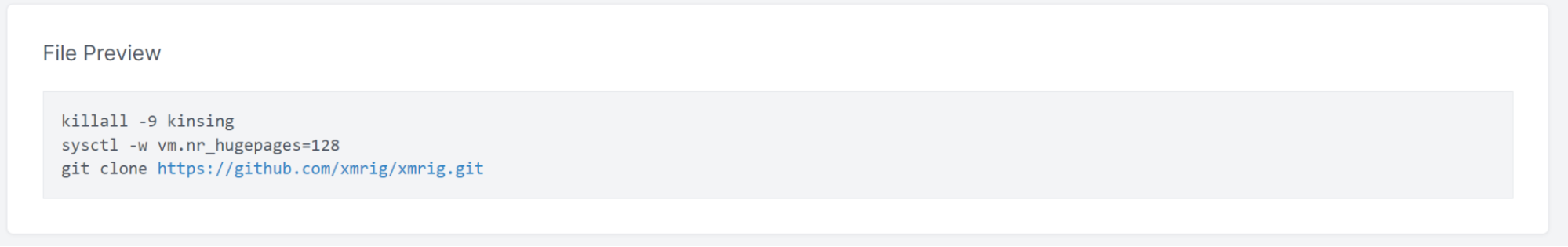
We can also look inside the collected files, including the bash history which triggered the initial investigation pivot points. The bash_history predictably shows some interactive activity pulling down the xmrig repository:
While this was a more simple investigation and a real compromise would have a number of different threads to pull, this shows that once you have access to the right data, container investigations become far less complex. Often, the most challenging part of a cloud investigation is getting the required data before it the container disappears.
Ready to perform your own investigation? Try the Cado Response free trial.
More from the blog
View All PostsAligning Forensic Investigations to the MITRE ATT&CK Framework
February 29, 2024OpenShift Container Forensics with the Cado Platform
March 4, 2024Leveraging Adversary Emulation for Effective Cloud Forensic Analysis
December 20, 2024

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

