Cado Labs researchers have discovered evidence of retaliation from Russian cyber threat groups, in response to yesterday’s expectations that Germany will supply Ukraine with Leopard 2 tanks.
Telegram Triage
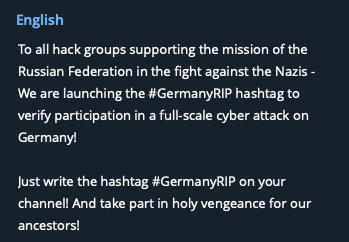
During routine monitoring of Telegram channels associated with Russian-language hacktivist groups, several posts referencing the Leopard 2 rumours were discovered. These posts were accompanied by the hashtag #ГерманияRIP which translates to “#GermanyRIP”. The hashtag appears to be used to unite individual groups in an effort to encourage collective cyber attacks against German infrastructure.
Messages including the hashtag were first spotted on the public Telegram channel of the Killnet group, on the evening of Tuesday the 24th of January, and were soon forwarded to channels operated by other Russian-language hacktivist groups.

DDoS Reports
Shortly after the call to action, reports concerning DDoS attacks leveraged against German organisations began to appear. As a caveat: It’s not clear how accurate these reports are, several of the websites were reachable at the time of writing.
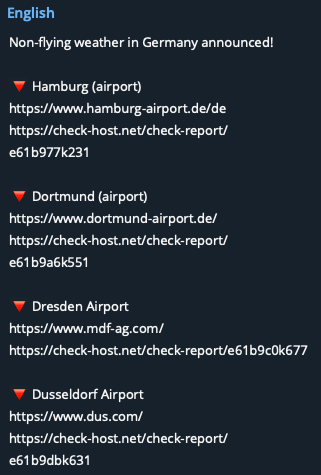
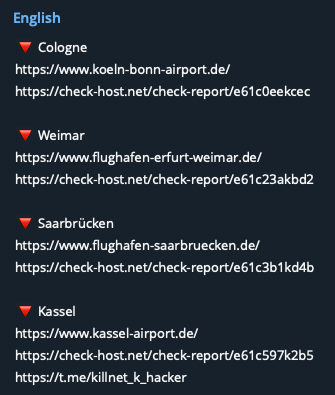
Anonymous Russia claimed to have conducted DDoS attacks against the websites of major German airports, including Hamburg, Dortmund, Dresden and Dusseldorf, amongst others.
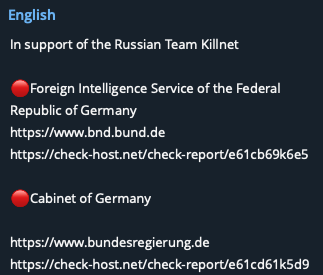
A group named “Anonymous Sudan” also reportedly conducted DDoS attacks against the websites of the German foreign intelligence service and the Cabinet of Germany, in support of Killnet.
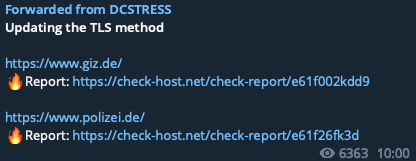
Other Russian-language groups soon reported similar attacks, including on GIZ (a German development agency) and the national police website.
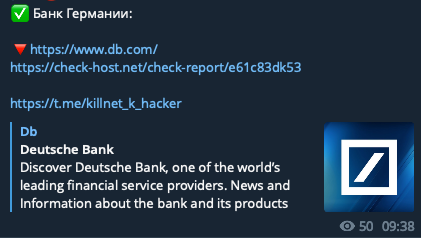
Reports of additional attacks on German airports, along with attacks on financial institutions, such as Deutsche Bank and Giropay (an online payment system) were also spotted.
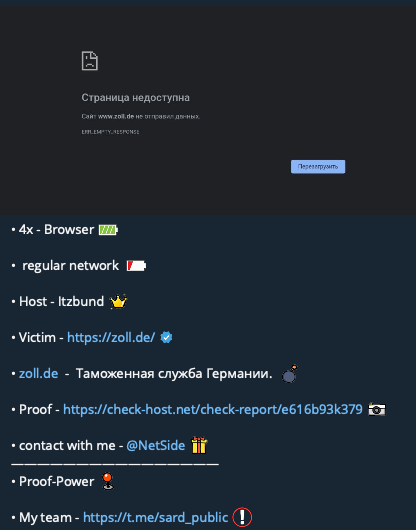
Cado researchers also encountered reports of attacks on the German customs service (zoll.de).
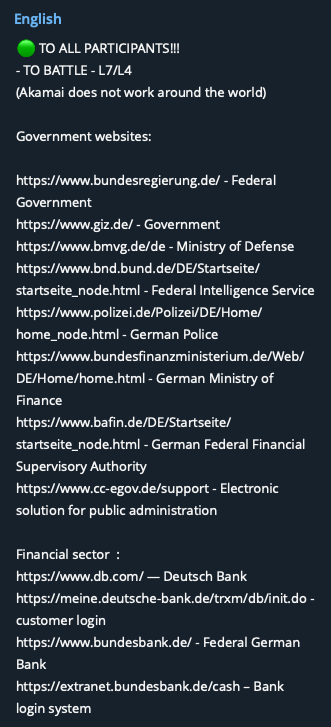
Furthermore, a message containing suggestions of additional targets in the government, financial and aviation sectors was seen.
Conclusion
As we’ve seen throughout the Russia-Ukraine war, cyber threat actors are quick to respond to geopolitical events, and are successful in uniting and mobilising groups with similar motives. The involvement of a group purporting to be the Sudanese version of Anonymous is interesting to note, as it demonstrates the ability for Russian-language hacktivist groups to conduct this mobilisation and collaboration on an international level.
It’s difficult to determine just how much disruption these DDoS attacks cause, and Cado Labs researchers could only verify that some of the websites had actually experienced disruption. Most seemed to have been restored quickly and were accessible at the time of writing.
Nonetheless, there’s no denying that the websites targeted host essential information, disruption to which is likely to have tangible effects. We expect to see more of this activity in the coming days.
More from the blog
View All PostsHonourable Malcolm Turnbull joins Cado Security's Board of Advisors
May 10, 2021Technical Analysis of the DDoS Attacks against Ukrainian Websites
February 20, 2022Cado Wins 2023 Fortress Cyber Security Award
May 31, 2023

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.

