Ephemeral Means Data Disappears
Containers have seen increased adoption in cloud environments over recent years given their lightweight, easy to deploy, and resource-efficient nature. However, the ephemeral nature of container-based and serverless resources can make it impossible to investigate potential threats.
Leave No Stone Left Unturned
.png?width=600&name=Cado%20New%20Use%20Case%20Graphics%20R2_Container%20Investigations%201%20(Collage).png)
Full Range Support.
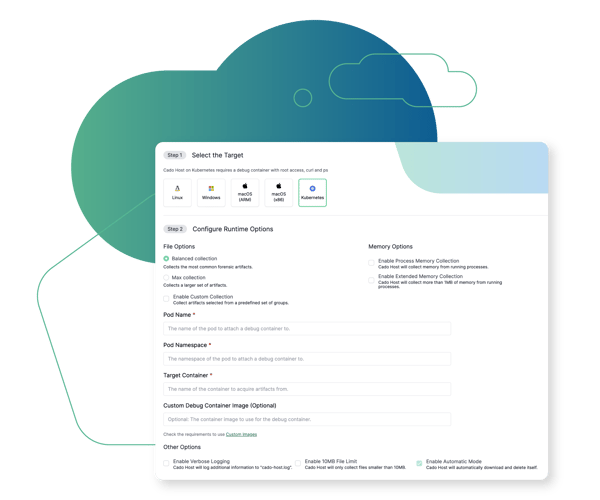
Distroless Containers? No Problem.
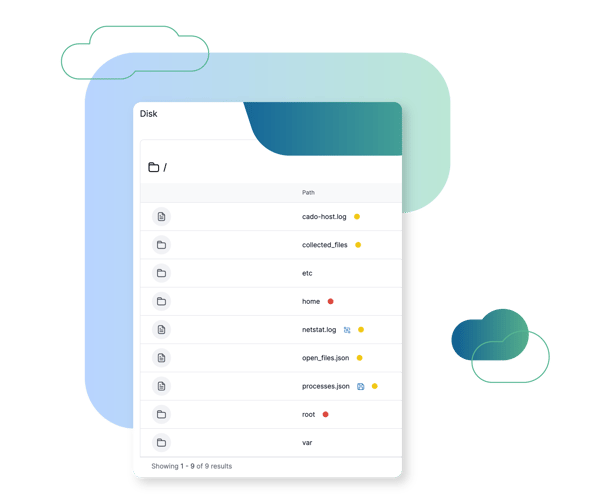
Filesystem Exploration
Cado automatically collects key data sources, including running processes, network connections, as well as key system and log files, which can be explored using Cado's browse disk capability. Cado also uses their previously open-sourced "varc" tool-set to collect memory from individual processes for forensic analysis.
Browse Other Use Cases
Explore other ways security teams are using the Cado Security platform to advance their mission.
Cross Cloud Investigations
Investigate incidents identified in AWS, Azure, and GCP in a single pane of glass.
SOC Triage
Automate triage acquisition of endpoint resources to gain immediate event insights and facilitate quick escalation.
SaaS Investigations
Analyze SaaS logs alongside other critical sources to investigate compromises, such as Business Email Compromise (BEC).
Cloud Detection & Response (CDR)
Marry threat detection with automated forensic collection and investigation to expedite response to cloud threats.
Evidence Preservation
Ensure evidence residing in ephemeral environments is immediately captured and preserved before it disappears.

The Cado Advantage
Cado Security is helping organizations around the world achieve results.







