Security Experts ≠ Cloud Experts
Organizations have adopted a multi-cloud strategy to enhance the resilience and efficiency of their infrastructure. This diversification means security teams are often expected to secure data across multiple Cloud Service Providers (CSPs). Each provides hundreds of different services and their own set of best practices and data sources. It is unrealistic to expect security teams to possess this level of intricate cloud knowledge.
Remove Chaos from Multi-Cloud
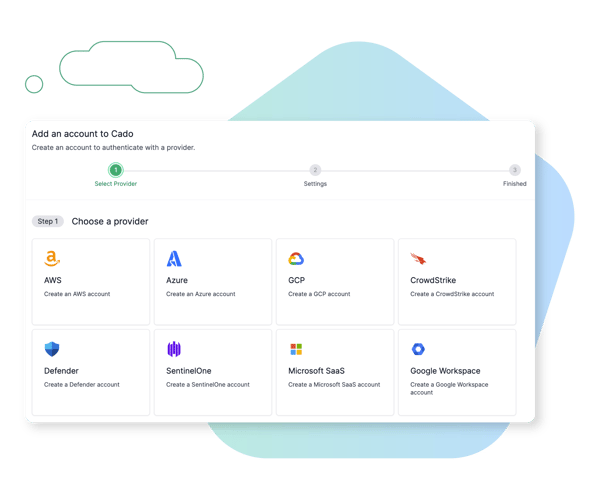
Unified Account Management
.png?width=600&name=Cado%20New%20Use%20Case%20Graphics%20R2_Cross%20Cloud%202%20(Collage).png)
Multi-cloud and Cross Cloud Investigations
Cado Security provides a seamless and guided experience for native acquisition of cloud-based resources across the three major cloud service providers - AWS, Azure, and GCP. Evidence can be acquired from compute, serverless, containers, object storage services, and more. This includes cross cloud acquisition of full volume captures as well as lightweight triage collections for rapid triage.
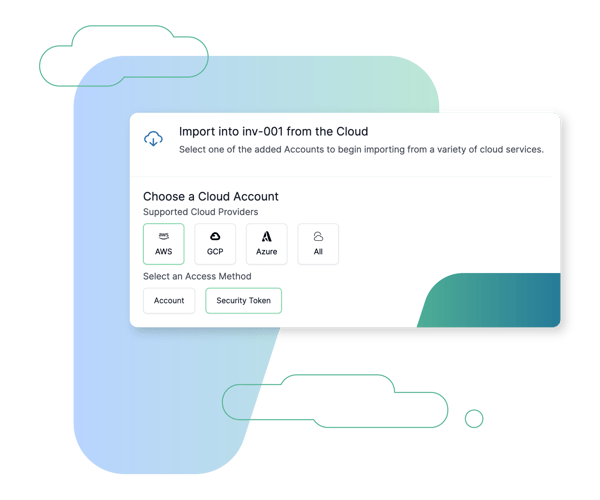
Flexible and Secure Access Methods
As well as being able to acquire resources using cloud accounts, single use credentials (AKA Just-in-Time access) can be used. This means cross account roles with long term access and high privileges don't have to be embedded into the application, potentially alleviating security concerns of internal cloud teams.
Browse Other Use Cases
Explore other ways security teams are using the Cado Security platform to advance their mission.
Container & K8s Investigations
SOC Triage
Automate triage acquisition of endpoint resources to gain immediate event insights and facilitate quick escalation.
SaaS Investigations
Analyze SaaS logs alongside other critical sources to investigate compromises, such as Business Email Compromise (BEC).
Cloud Detection & Response (CDR)
Marry threat detection with automated forensic collection and investigation to expedite response to cloud threats.
Evidence Preservation
Ensure evidence residing in ephemeral environments is immediately captured and preserved before it disappears.

The Cado Advantage
Cado Security is a multi-cloud security solution helping organizations around the world achieve results.







