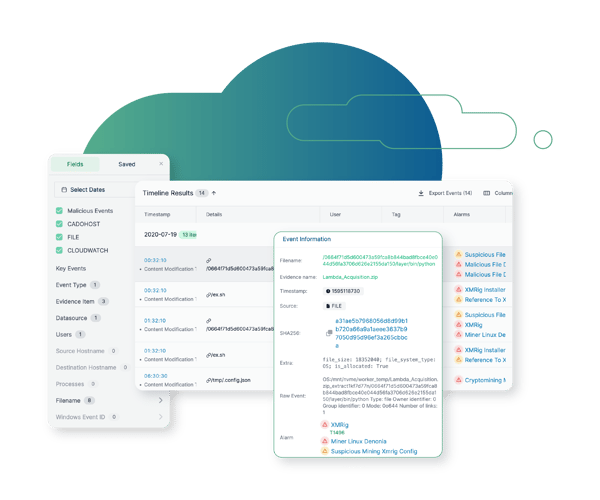
Forensic Success with Cado Security
With Cado Security, forensic experts don't have to be cloud experts to secure their environment. The Cado Platform streamlines investigations in complex, hybrid environments so forensic teams can focus on what they do best. By applying automation with deep investigation abilities in the form of a fully unified timeline, the platform automates the mundane, and enables forensic analysts to focus on the most pressing issues.
The Cado Platform for Forensic Teams
It's hard enough to find top notch talent, and with the rapid migration to the cloud there is a growing demand for security teams to also possess deep cloud knowledge. As threats increasingly target cloud infrastructure, a more efficient and automated approach is required to enable faster investigation and response.
Full Chain of Custody
The Cado Platform handles chain of custody completely autonomously behind the scenes, saving time and allowing forensic teams to focus on the investigation itself.
Instant Data Capture
Gain immediate access to forensic data across cloud, container, and serverless resources without having to worry about working across multiple teams and platforms.
Parallel Processing
Patent-pending architecture enables rapid processing, allow to automatically spin up cloud workers to process evidence items in parallel - which typically takes days.
Streamlined Investigations
Automatically flag key malicious activity, and presents a full timeline of events and surfaces the root cause and scope of the incident.
Top Cado Use Cases
See how security teams are using the Cado platform to close the cybersecurity skills gap.
Cross Cloud Investigations
Respond to incidents identified in AWS, Azure, and GCP in a single pane of glass.
Container & K8s Investigations
Perform container investigations in environments including EKS, AKS, GKE, and Kubernetes.
SOC Triage
Automate triage acquisition of endpoint resources to gain immediate event insights and facilitate quick escalation.
SaaS Investigations
Analyze SaaS logs alongside other critical sources to investigate compromises such as Business Email Compromise (BEC).
Cloud Detection & Response (CDR)
Marry threat detection with forensic context to expedite response.
Evidence Preservation
Ensure evidence residing in ephemeral environments is immediately captured and preserved before it disappears.

“We have a cloud team that takes countless manual steps to capture and process forensic data...I can't wait to go tell them I can do this in just a few clicks!”
DFIR Team Lead
Fortune 500 US Insurance Company










