A Billion $ Problem
SaaS applications provide a large attack surface, yet they are over overlooked when it comes to preparing for an incident. Moreover, when an identity is compromised through a SaaS application, more often than not inadequate logging and visibility prevents a thorough investigation being conducted and the root cause remaining unknown.
Bridge the Gaps in SaaS
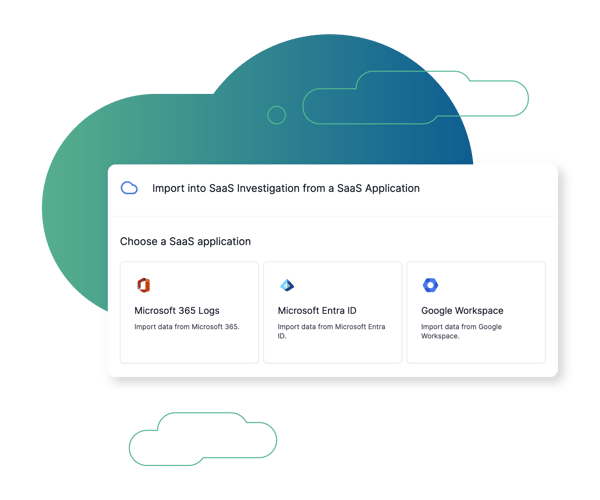
Critical Data Source Coverage
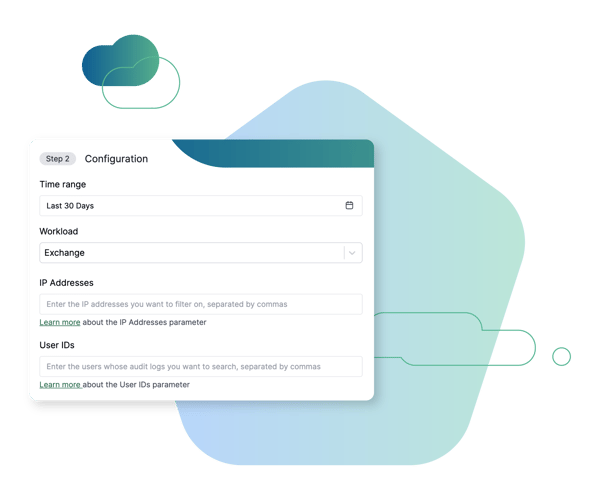
Cado provides the ability to investigate business email compromise (BEC), account takeover (ATO), and insider threats. It allows users to seamlessly acquire SaaS logs from Microsoft 365, Microsoft Entra ID, as well as Google Workspace.
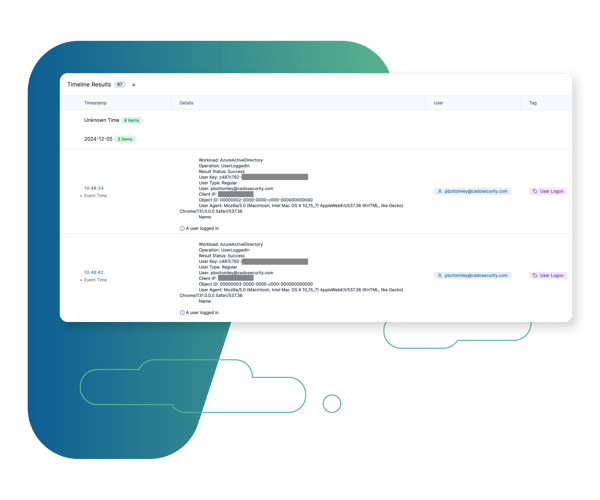
Unified Timeline
These critical data sources can be analyzed alongside other sources captured across on-prem and cloud environments to gain a better understanding of the scope and impact of malicious activity.
Browse Other Use Cases
Explore other ways security teams are using the Cado platform to advance their mission.
Cross Cloud Investigations
Investigate incidents identified in AWS, Azure, and GCP in a single pane of glass.
Container & K8s Investigations
Perform container investigations in environments including EKS, AKS, GKE, and Kubernetes.
SOC Triage
Automate triage acquisition of endpoint resources to gain immediate event insights and facilitate quick escalation.
Cloud Detection & Response (CDR)
Marry threat detection with automated forensic collection and investigation to expedite response to cloud threats.
Evidence Preservation
Ensure evidence residing in ephemeral environments is immediately captured and preserved before it disappears.

The Cado Advantage
Cado Security is helping organizations around the world achieve results.