
Unpacking the SEC's Cybersecurity Disclosure Requirements for Incident Response Teams
The Securities and Exchange Commission (SEC) has introduced new rules mandating public companies to report cybersecurity breaches. This highlights the growing importance of cyber security outside of security and IT teams, requiring c-level leadership to be able to quickly understand the impact of security incidents. While the legislation requirements aim to drive institutional changes from the board down, they place significant pressure on security practitioners and incident responders to quickly and accurately navigate incident investigations and provide timely information to management.
4 Things Incident Response Teams Need to Know about the New Legislation
1. Time is of the Essence
IR teams must have the ability to quickly understand the severity of cyber security incidents. The new SEC rules mandate timely reporting once an incident is deemed material, giving organizations four days. It's important to note that the four day deadline only applies after materiality is determined, but there is an expectation for timely determination without unreasonable delays. This means speed is a huge factor here. It's critical that incident responders and security analysts have the ability to quickly access, process, and analyze incident evidence.
2. Communication and Documentation are Vital
Effective communication is crucial when determining incident materiality and reporting on incidents. Although the responsibility of determining materiality of an incident lies with the c-suite and board, they need timely and accurate information from the incident response and security teams in order to make a decision. In the event of an incident, even one that may not be deemed material, having detailed documentation about how materiality determinations were made and the evidence that the decision was based on is essential. Especially if the SEC decides to investigate at a later date.
3. A Repeatable Process is Key
When establishing an incident response program, it’s important to prepare a set of questions in advance that the board is going to need answers to. This ensures repeatability, as questions such as How did the attacker gain access? What level of access did the attacker gain? What data (if any) was compromised? These questions will need to be answered every time. Incident response teams should regularly test their program and escalation processes to ensure a seamless flow of information. Active involvement of key stakeholders in materiality determinations is crucial, requiring coordination across various departments, including finance, legal, and IT.
4. The Scope May Be Larger Than You Think
The scope of the new legislation is larger than many people may think. There is a misconception that it only requires reporting on major data breaches impacting publicly traded companies. For a start, it covers much more than just data breaches, it's anything that threatens the security or assets of the company, be that dental of service, ransomware, or a huge array of other threats. While it is technically true that only publicly traded companies have to comply with the SEC, customers of non-public companies may demand compliance and disclosures across their supply chains according to the SEC's legislation.
5 Key Forensics Capabilities That Can Help Security Teams Comply with the SEC’s Disclosure Requirements
In order to adhere to the new reporting deadlines set by the SEC, organizations must leverage the latest and greatest forensics and incident response capabilities. Here are 5 key cloud forensics capabilities that can assist security teams in meeting these new requirements:
1. Single Click Access to Data
When suspicious activity is detected in a cloud environment, security teams often face a number of obstacles to gain access to the impacted resource. As access is often managed by a separate cloud team, security analysts generally have to manually open a ticket to request access. In many cases, it takes days to get this actioned. In the cloud, however, single-click access to data is possible by leveraging cloud-native APIs and automation. This means security teams can gain access to potentially compromised assets in the matter of minutes to get the answers they need.

Access Cloud Resources in a Single Click With Cado
2. Depth of Data
It's important that security teams have the ability to collect sufficient evidence in order to properly and thoroughly investigate an incident. In many cases, in order to identify incident root cause and scope, log analysis alone is not enough and full disk analysis is required. In addition, memory and network data are also critical sources.
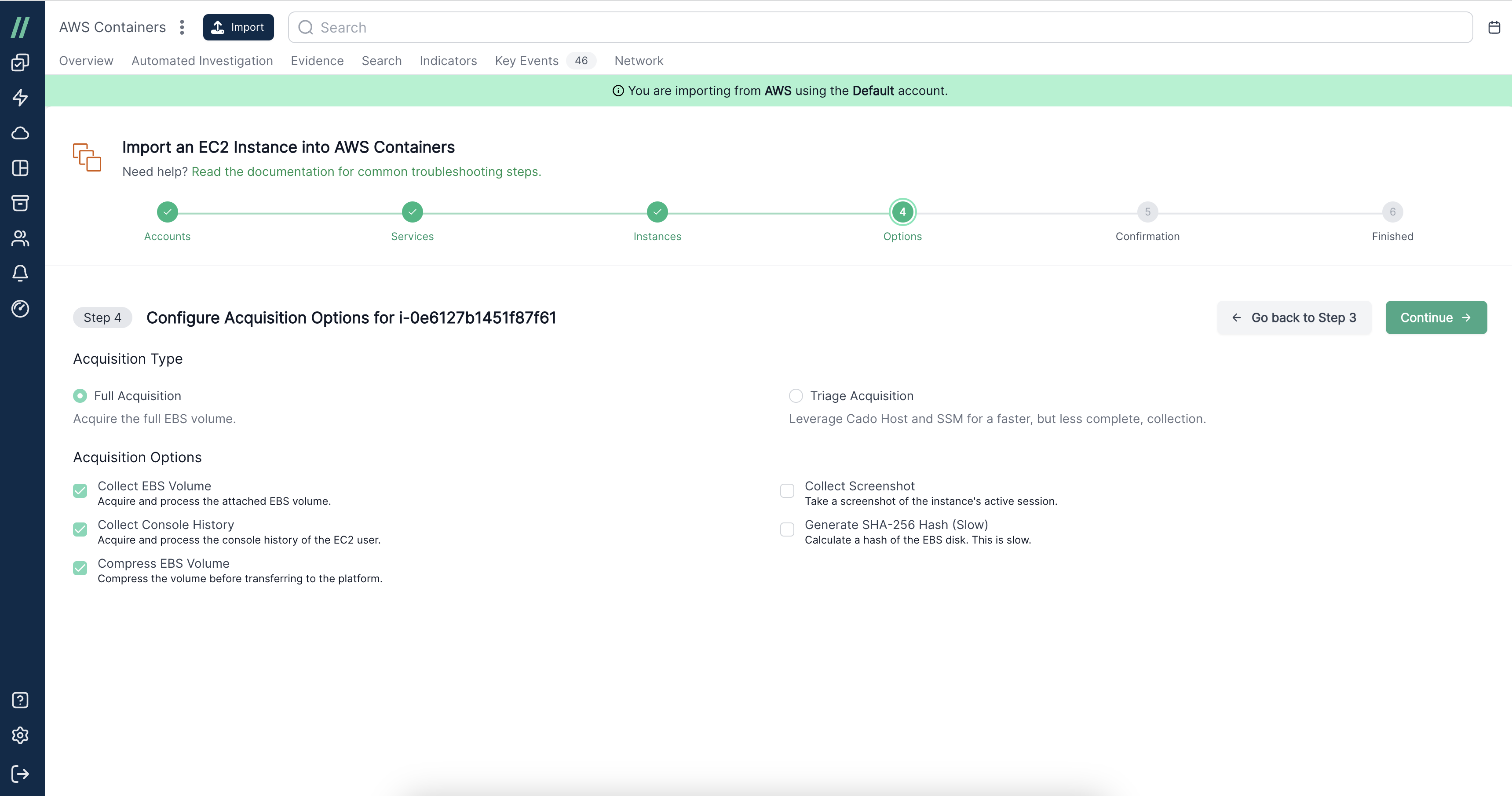
Perform Triage and Full Disk Acquisition With Cado
3. Multi-Cloud Support
Security teams often use a patchwork of tools to gather and analyze evidence, which can make investigations complicated and time consuming. This can be a combination of open-source, home grown, and commercial tooling that may not always work well together and this approach becomes even more complicated when it comes to investigating multi-cloud environments. Having a single solution that can enable investigations across multiple Cloud Service Providers (CSPs) is critical to address the needs of customers.
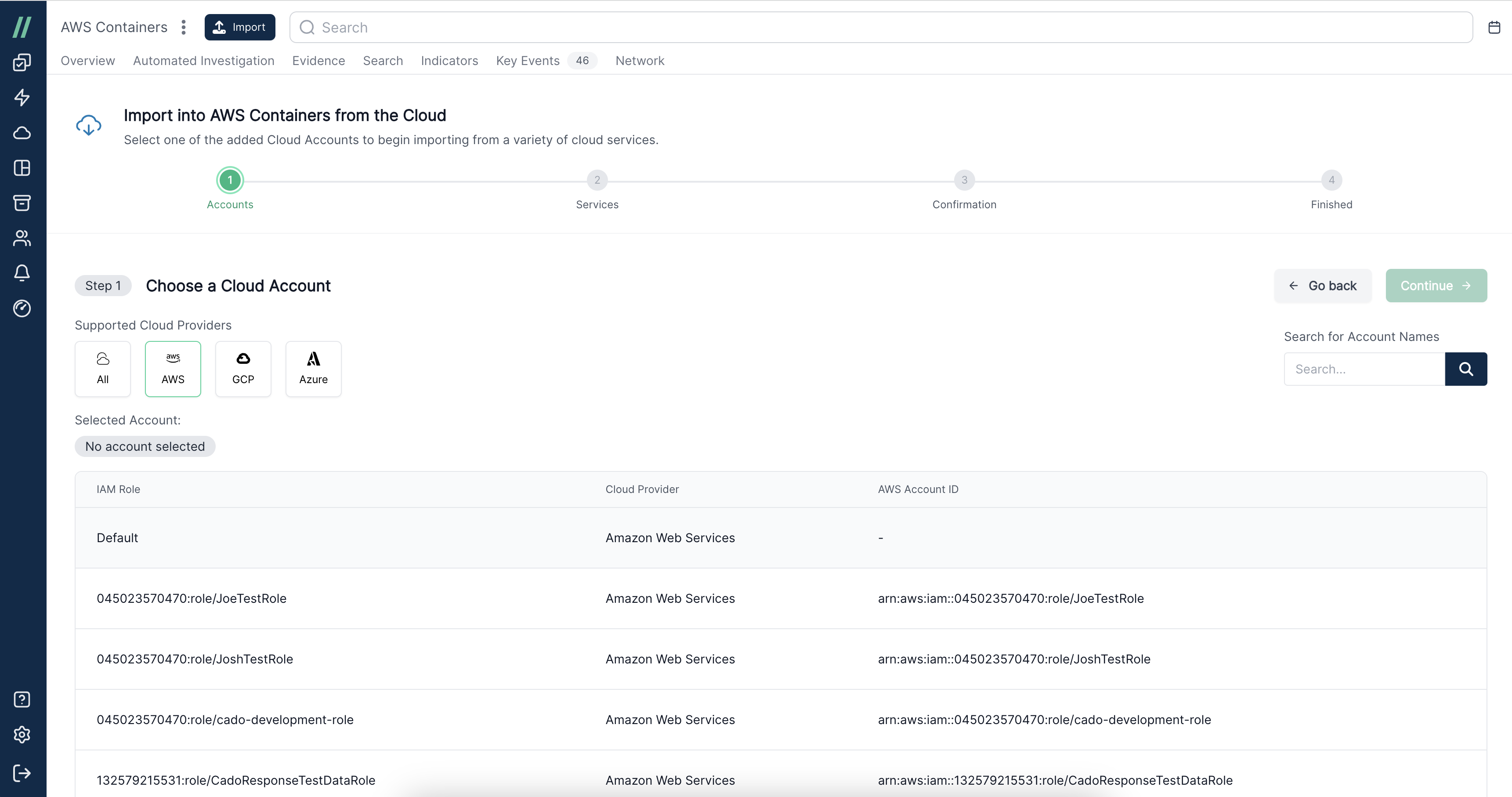
Multi-Cloud Investigations Made Easy with Cado
4. Single Timeline Analysis
After evidence is collected, security teams often resort to spreadsheets to pull together an event timeline. While extremely important to an investigation, manually pulling together a timeline is quite the heavy life -- especially in more complex cases, where hundreds of machines are potentially impacted. A platform that has the ability to process hundreds of different data sources and correlate them into a single timeline automatically can save analysts days during an investigation.
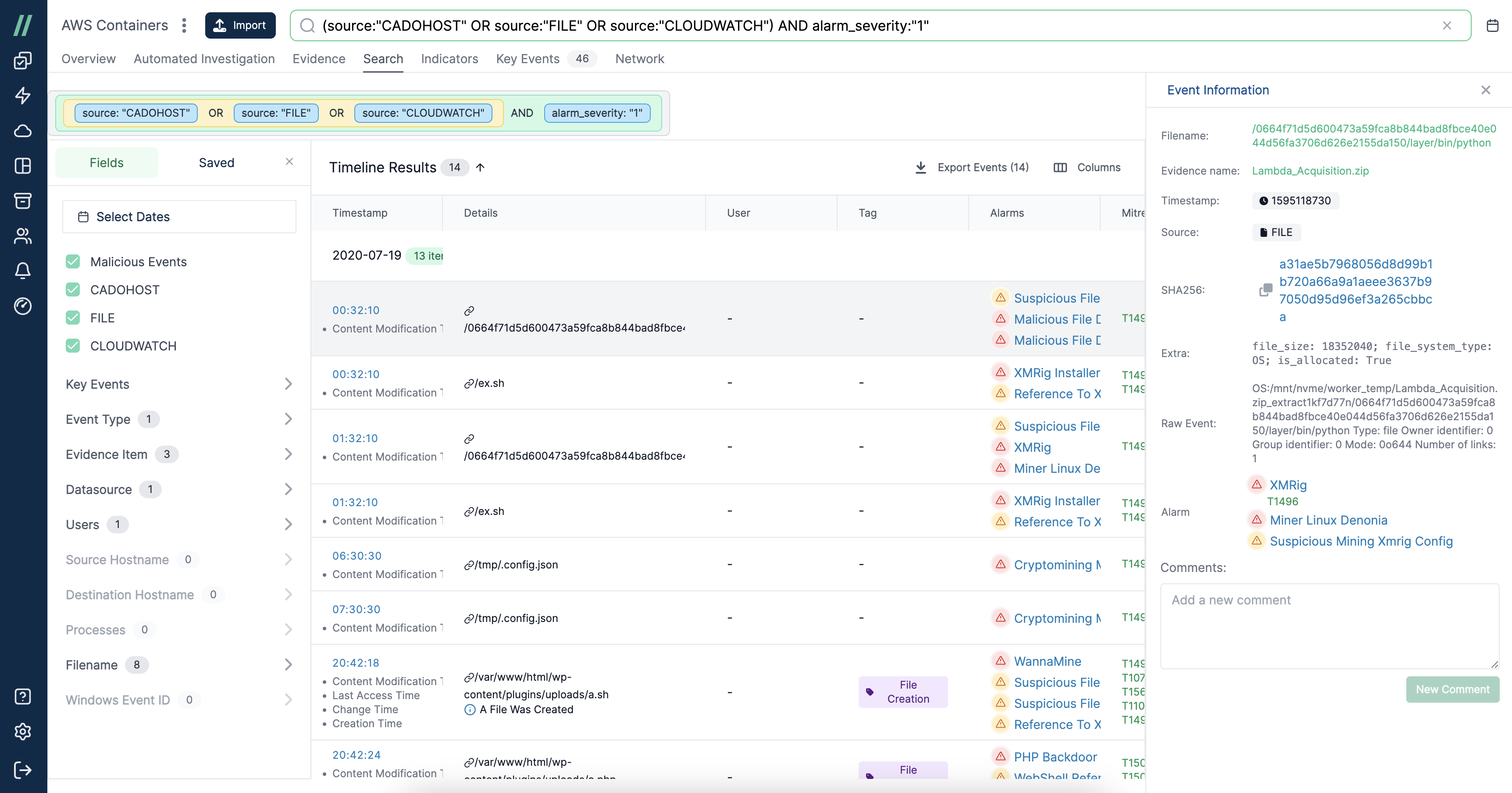
Single Timeline View in the Cado Platform
Incident Response Preparedness
A proactive approach to cloud forensics and incident response enables security teams to understand whether they are prepared to quickly investigate and respond to threats before an incident occurs. This ensures that when an incident is detected, the security team will have the ability to quickly identify the root cause and remediate the threat. Being proactive also enables security teams to continuously improve their incident response program by preemptively identifying and rectifying any existing gaps, so as not to waste valuable time during the heat of an incident. Further, it's incredibly important in context of reporting mandates with tight deadlines such as those outlined in the SEC's cybersecurity disclosure requirements.

Cado’s Incident Readiness Dashboard
Interested in learning how Cado can help you comply with incident reporting mandates? Schedule a demo with our team. Want to know how prepared you are to investigate and respond to incidents? Sign up for our free Incident Response Readiness Assessment.
More from the blog
View All PostsNavigating the Cyber Security Regulatory Maze: Balancing Incident Response, Breach Disclosure, and Compliance in the Cloud Era
October 27, 2023What Does "Material" Mean? Reflecting on SEC's Cyber Disclosure Requirements
May 14, 2024It's Been 4 Months Since the SEC's Cybersecurity Disclosure Requirement: Here's What We've Learned
April 26, 2024

Subscribe to Our Blog
To stay up to date on the latest from Cado Security, subscribe to our blog today.
