The speed and scale at which new cloud resources can be spun up has resulted in uncontrolled deployments, misconfigurations, and security risks. And it has had security teams racing to secure the business’ rapid migration from traditional on-premises environments to the cloud. While many organizations have successfully extended their prevention and detection capabilities to the cloud – they are now experiencing another major gap. Once something bad has been identified, understanding its true scope and impact is nearly impossible at times. The proliferation of cloud resources across a multitude of cloud providers, and the addition of container and serverless capabilities all add to the complexities. It’s clear that organizations need a better way to manage cloud incident response.
Security teams are looking to move past their homegrown solutions and open source tools to incorporate real cloud forensics capabilities. However, with the increased buzz around cloud forensics, it can be challenging to decipher what is real cloud forensics, and what is fauxrensics.
Drawing from Cado’s recently released white paper, this blog covers the five core capabilities that security teams should consider when evaluating a cloud forensics and incident response solution:
Depth of Data
There have been many conversations among the security community about whether cloud forensics is just log analysis. The reality however, is that cloud forensics necessitates access to a robust dataset that extends far beyond traditional log data sources. While logs provide valuable insights, a forensics investigation demands a deeper understanding derived from multiple data sources, including disk, network, and memory, within the cloud infrastructure. Full disk analysis complements log analysis, offering crucial context for identifying the root cause and scope of an incident. For instance, when investigating an incident involving a Kubernetes cluster running on an EC2 instance, access to bash history can provide insights into the commands executed by attackers on the affected instance, which would not be available through cloud logs alone.

By combining cloud logs, host, and memory information, security teams gain enhanced visibility and context to identify the root cause, scope, and impact of compromises.
Chain of Custody
Chain of custody is extremely critical in the context of legal proceedings and is an essential component of forensics and incident response. However, chain of custody in the cloud can be extremely complex with the number of people who have access, and the rise of multi-cloud. The ability to preserve unaltered copies of forensic evidence in a secure manner is required to ensure its integrity throughout an investigation.
Real cloud forensics platforms should autonomously handle chain of custody in the background, recording and safeguarding evidence without human intervention.
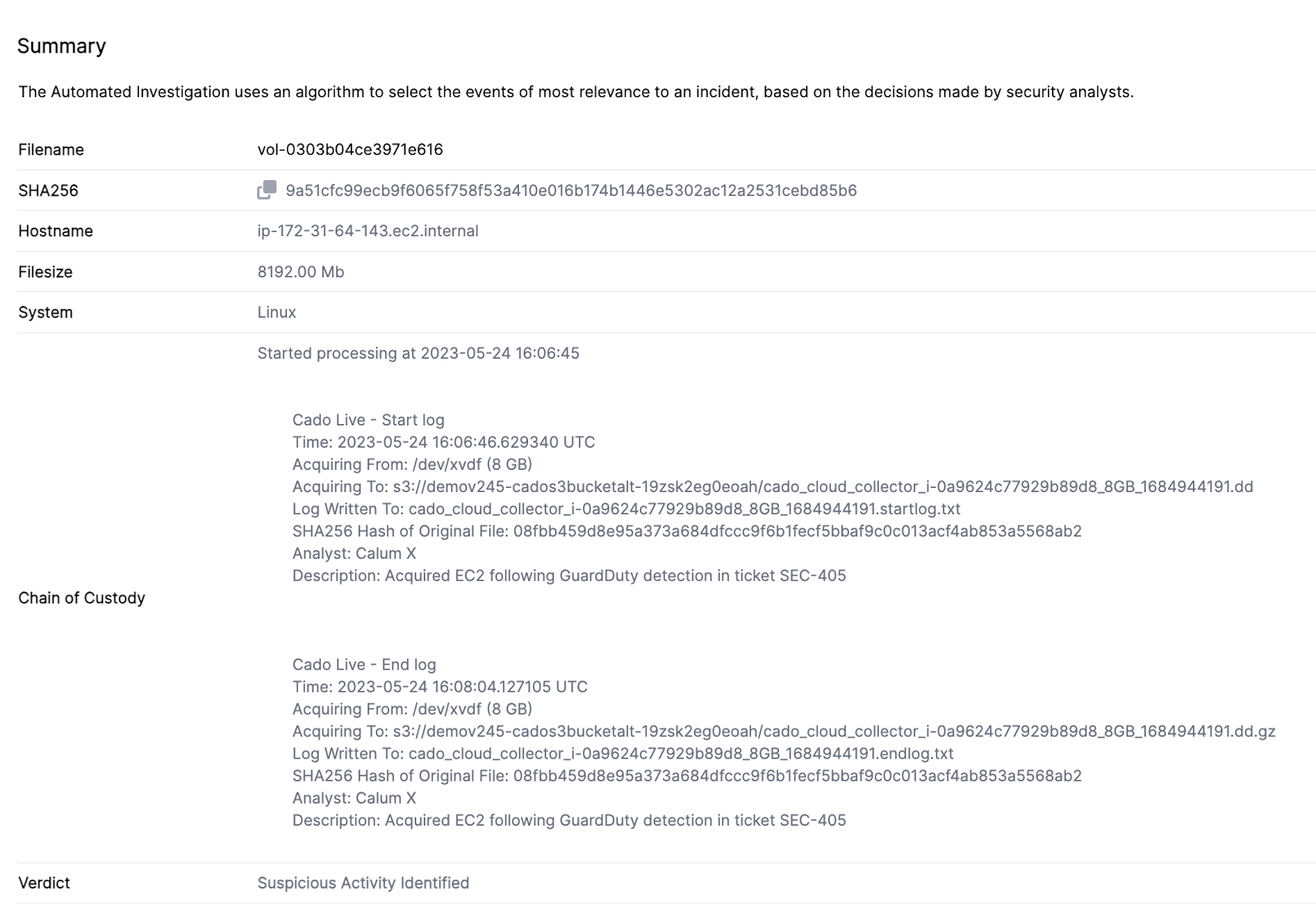
Chain of custody in the Cado platform
Automated Collection and Isolation
When malicious activity is detected, the speed at which security teams can determine root cause and scope is essential to reducing Mean Time To Response (MTTR). Automated forensic data collection and system isolation enables security teams to prevent potential damage and spread while a deeper-dive forensics investigation takes place. This method also ensures critical incident evidence residing in ephemeral environments is preserved in the event it is needed for an investigation. Cloud forensics and incident response platforms should offer the ability to natively integrate with incident management tools and/or built-in product automation rules to make this possible.

Automated cloud forensics through Tines SOAR and the Cado Platform
Ease of Use
Security teams shouldn’t require deep cloud or incident response knowledge to perform forensic investigations of cloud resources. They already have enough on their plate. While traditional forensics tools and approaches have made investigation and response extremely tedious and complex, modern forensics platforms prioritize usability at the core and leverage automation to drastically simplify the end-to-end IR process – even when an incident spans multiple CSPs. Offering features such as cross cloud support, data enrichment, a single timeline view, saved search, and faceted search can help advanced analysts achieve greater efficiency and novel analysts participate in more complex investigations.
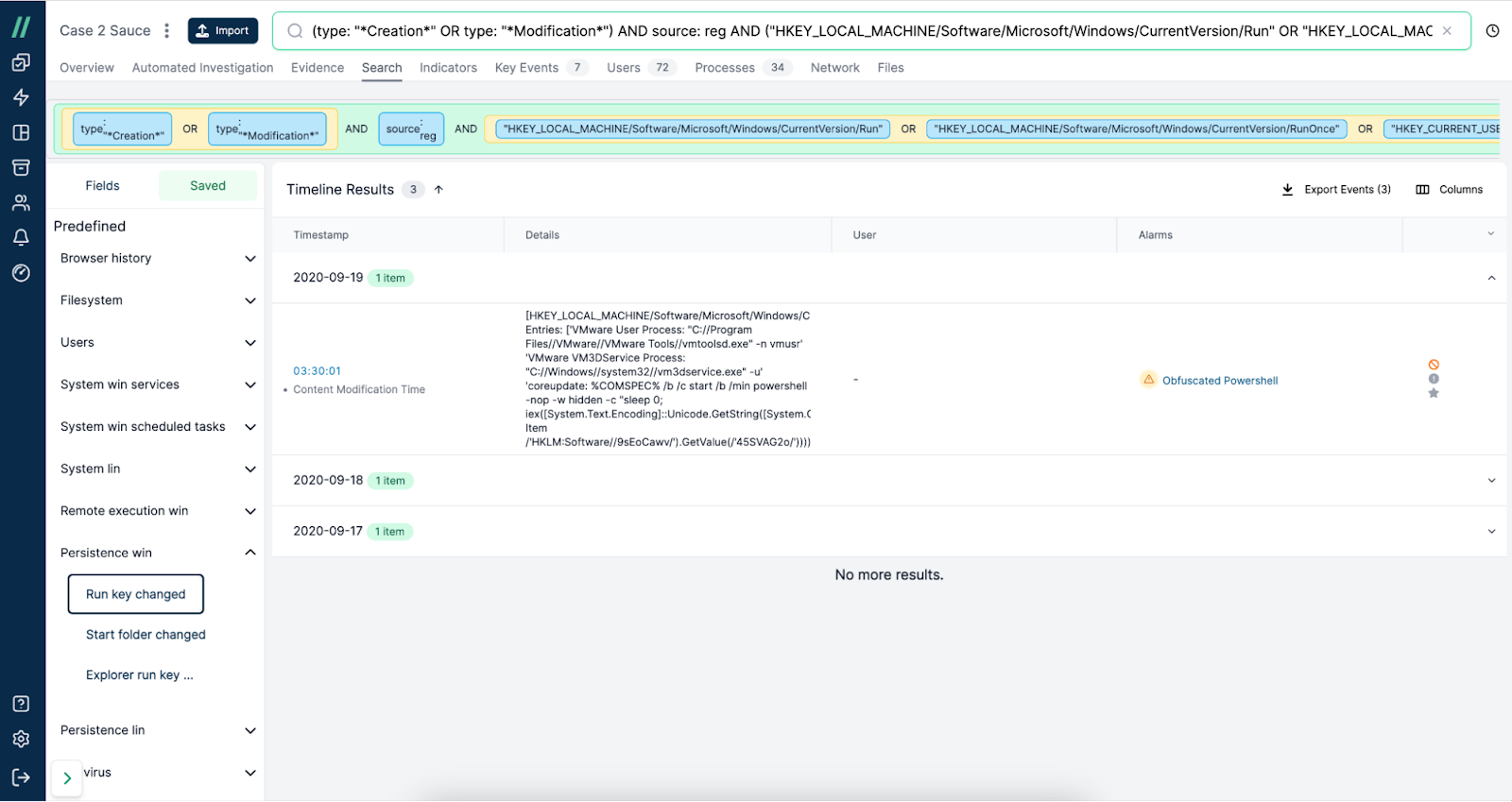
Cado’s timeline view
Diving into forensics data within the Cado Platform
Incident Preparedness
A proactive approach to incident response is essential in order to effectively manage rapidly evolving cloud threats. Having the ability to continuously assess your incident response program enables you to rapidly identify and mitigate any gaps identified that could prevent the organization from being able to effectively respond to potential threats. Real forensics platforms deliver features that enable security teams to prepare extensively – and understand their shortcomings before they are in the heat of an incident. For example, cloud forensics platforms can provide the ability to:
- Run readiness checks and see readiness trends over time
- Identify and mitigate issues that could prevent rapid investigation and response
- Ensure the correct logging, management agents, and other cloud-native tools are appropriately configured and operational
- Ensure that data gathered during an investigation can be decrypted
- Verify that your permissions are aligned with best practices and are capable of supporting your incident response efforts
- And more
If you are evaluating forensics tools for the cloud, we hope that this blog helps you better assess what capabilities you may need.
Cloud Forensics with Cado
Cado Security streamlines cloud forensics investigations by addressing the key challenges discussed above. The Cado platform is designed to offer capabilities that simplify and expedite forensics in the cloud. With features such as, allowing analysts to access multiple data sources in one place even across multiple cloud providers. Autonomously ensuring that evidence is stored securely and that the chain of custody is maintained. Providing a unified timeline view of an incident. Automation rules to reduce MTTR when isolating systems or collecting evidence. On top of providing key insights into incident preparedness even before incidents occur.

Cado’s timeline view
If you’re interested in learning how Cado can help you achieve a robust cloud forensics program, schedule a demo with our team.



